Graph encryption shortest path query method and system supporting k disordered nodes
A technology of the shortest path and nodes, applied in cloud services, encrypted graph data navigation, and privacy protection fields, to achieve the effects of privacy protection, low computing cost computing operations, and strong index security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
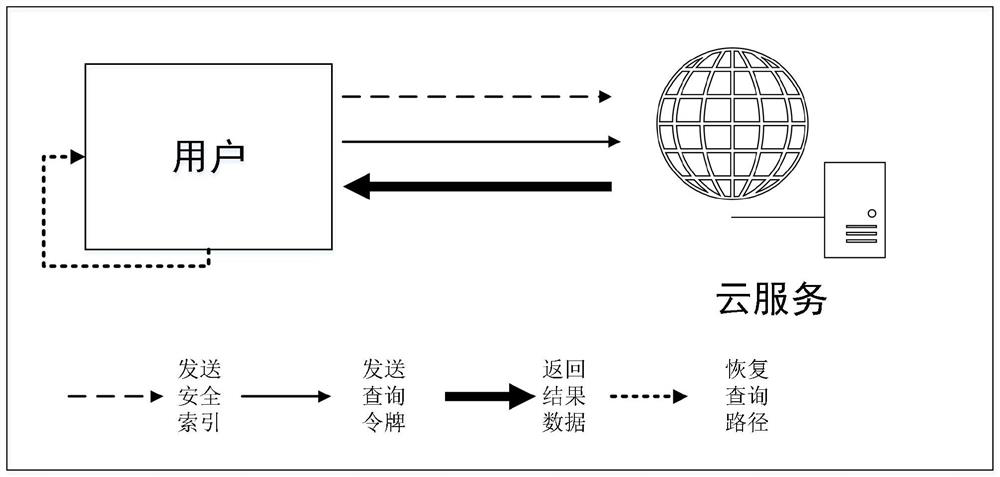
[0069] In this embodiment, the user module encrypts the graph data and calculates the security index and sends it to the cloud service module, and at the same time, the user module sends a shortest path query of k disordered nodes to the cloud service module and obtains the returned result;
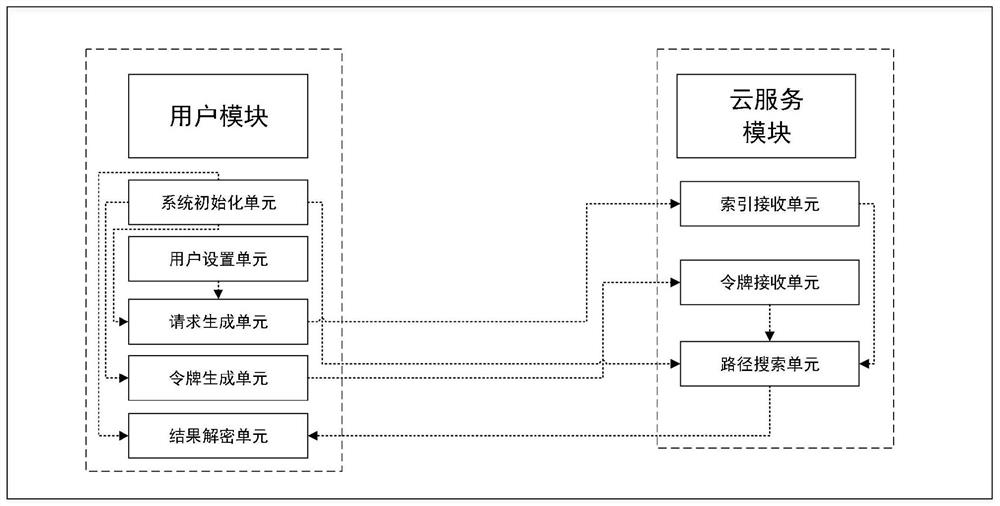
[0070] In this embodiment, a shortest path query system for k disordered nodes, such as figure 1 shown, including a user module and a cloud service module;
[0071] Taking the query processing of dense routes on the cloud in a navigation service as an example, the user module is the user who encrypts the graph data and selects the starting point, the ending point and k disordered nodes to query the route, and the cloud service module is a third-party platform. The user submits his own starting point, ending point and k disordered nodes to the third-party platform, and the third-party platform matches the appropriate shortest route for navigation;
[0072] The user module includes: a syst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com