Anti-key exposure cloud data integrity verification method supporting fair payment
An integrity verification, cloud data technology, applied in the field of data security, can solve the problems of forgery of integrity verification certificates, unguaranteed data security, damage to message authentication labels, non-tampering, etc., to reduce computational overhead and communication. Overhead, effect of strong security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The embodiments of the present invention will be described in detail below with reference to the examples, and the implementation process of how the present invention applies technical means to solve technical problems and achieve technical effects will be specifically shown.
[0056] The main idea of the present invention is as follows:
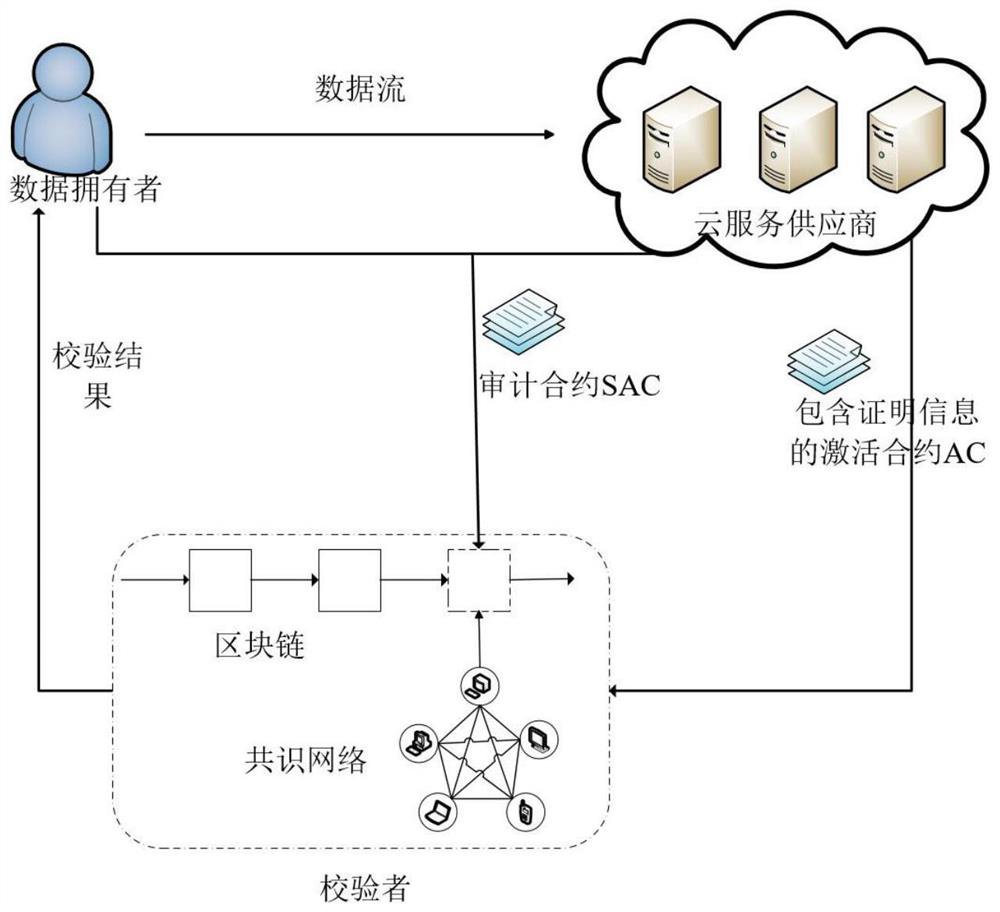
[0057] A cloud data integrity check method that supports fair payment and resists key exposure. The system model of this method is figure 1 As shown, there are three types of entities: data owner, cloud service provider, and verifier;
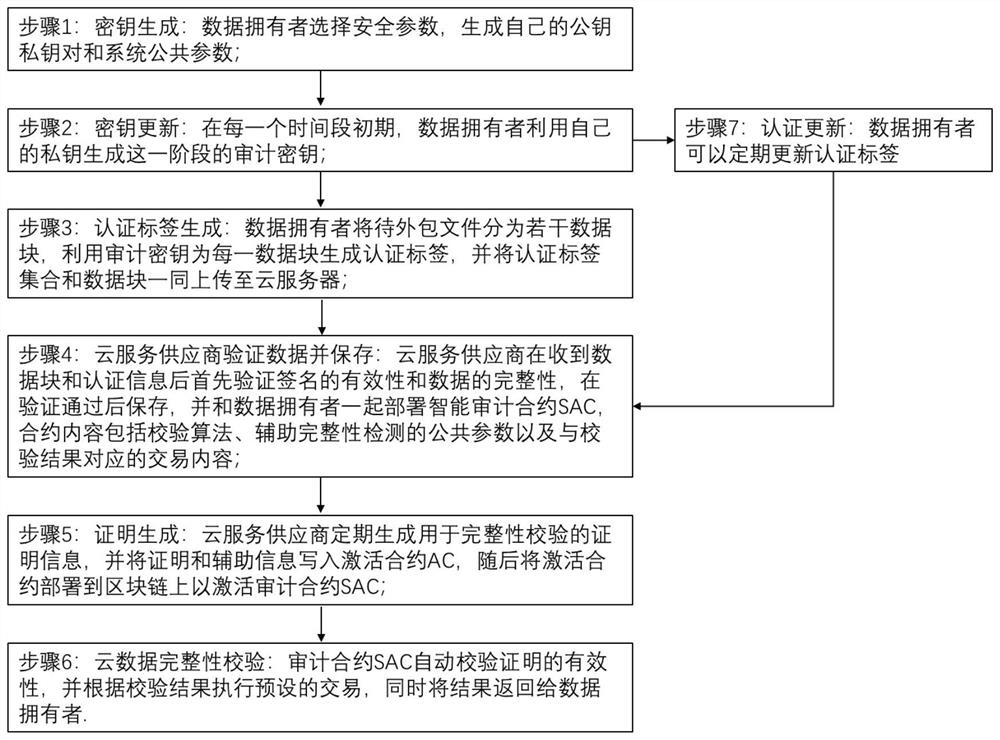
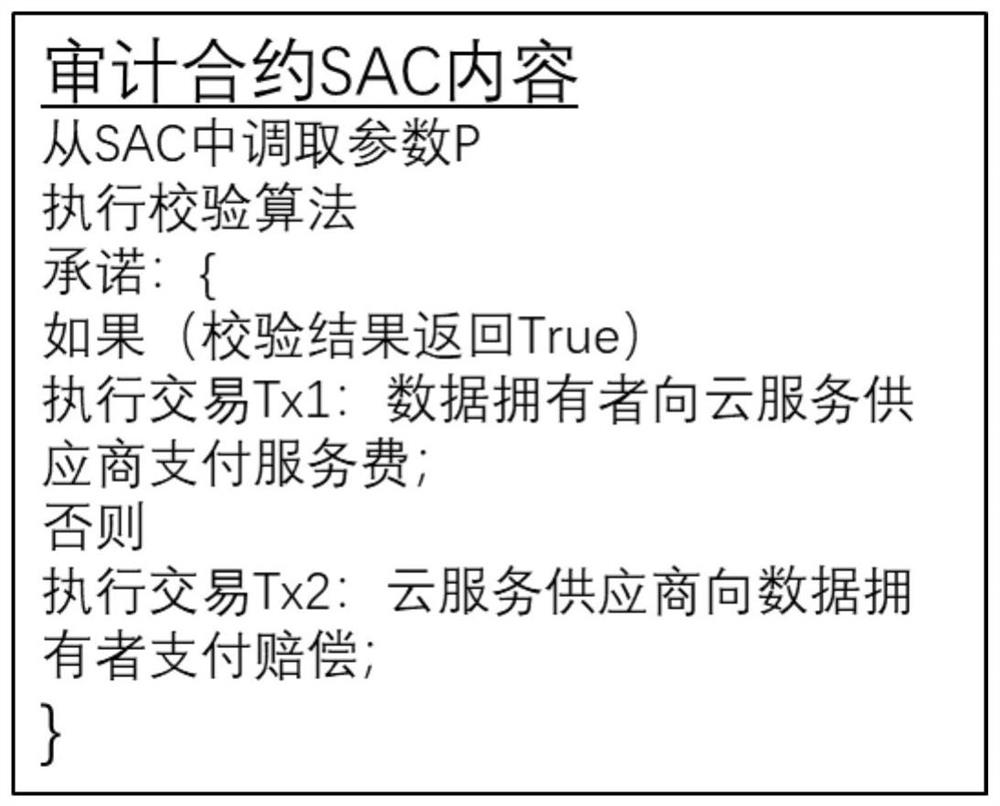
[0058] Data owner: The data owner uses the security parameters to generate a public key-private key pair and public parameters for integrity verification before data outsourcing; the data owner uses the private key to generate an audit key, and uses the audit key to calculate the authentication of the file tags, and then upload the data together with the set of authentication tags to the cloud serv...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap