Electric power 5G network slice authentication message matching method and device based on edge calculation
An edge computing and network slicing technology, which is applied in secure communication devices, electrical components, information technology support systems, etc., can solve the problems of affecting transmission delay, complicated communication authentication process, large data calculation and data transmission overhead, etc. The effect of transmission delay, reduction of data calculation and data transmission overhead, and improvement of calculation and communication efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
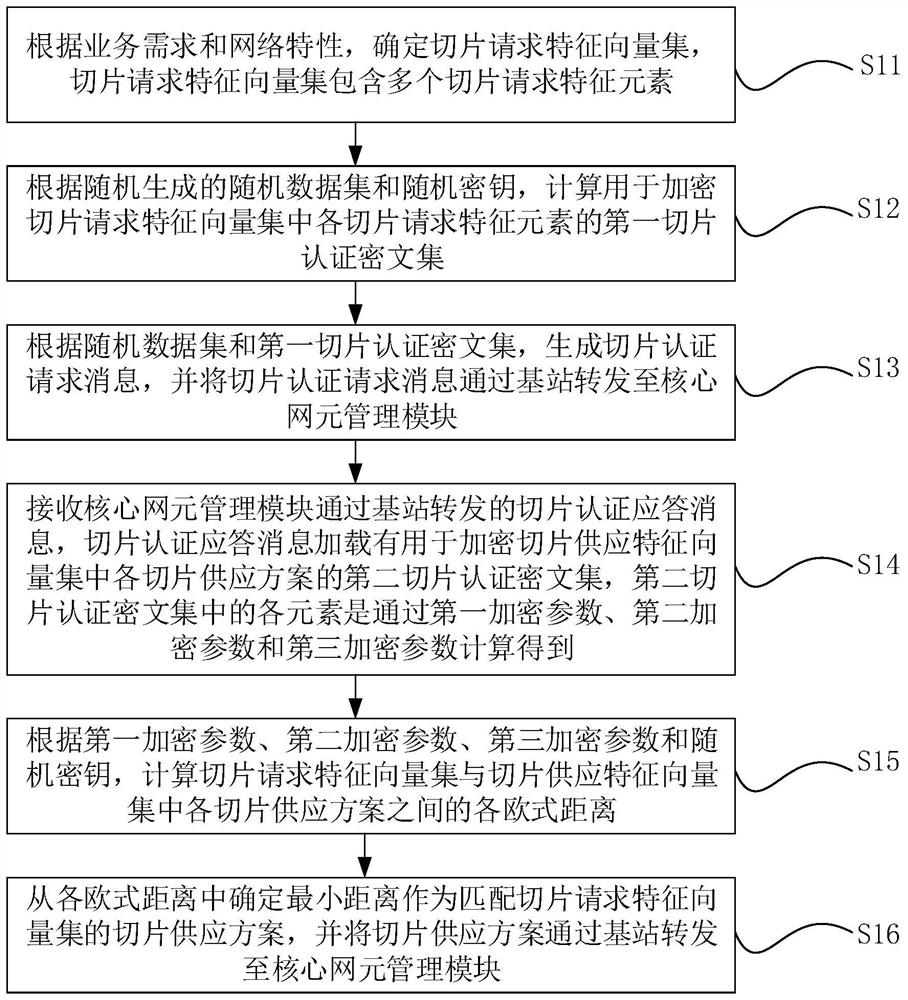
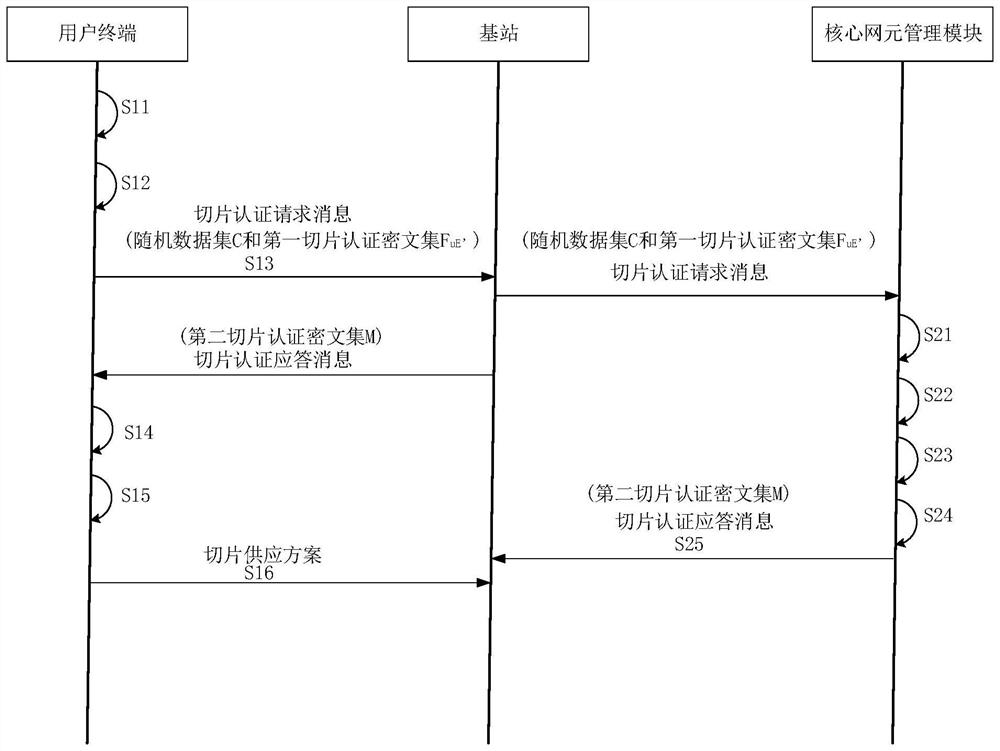
[0062] The edge computing-based power 5G network slice authentication message matching method provided by the embodiment of the present invention is used for user terminals, such as figure 1 shown, including the following steps:
[0063] Step S11: Determine a slice request feature vector set according to business requirements and network characteristics, where the slice request feature vector set includes multiple slice request feature elements.
[0064] The slice in this embodiment of the present invention may be a 5G network slice. The service requirements in the above are service conditions required by the user terminal to execute service applications. The network characteristics are the slice rate, bandwidth, delay, security level and other characteristics. Divide physical network resources into multiple fine-grained network slices based on features such as rate, bandwidth, delay, and security level. Physical network resource PNR={slice 1 , slice 2 ,…,slice n ,DS}, D...
Embodiment 2
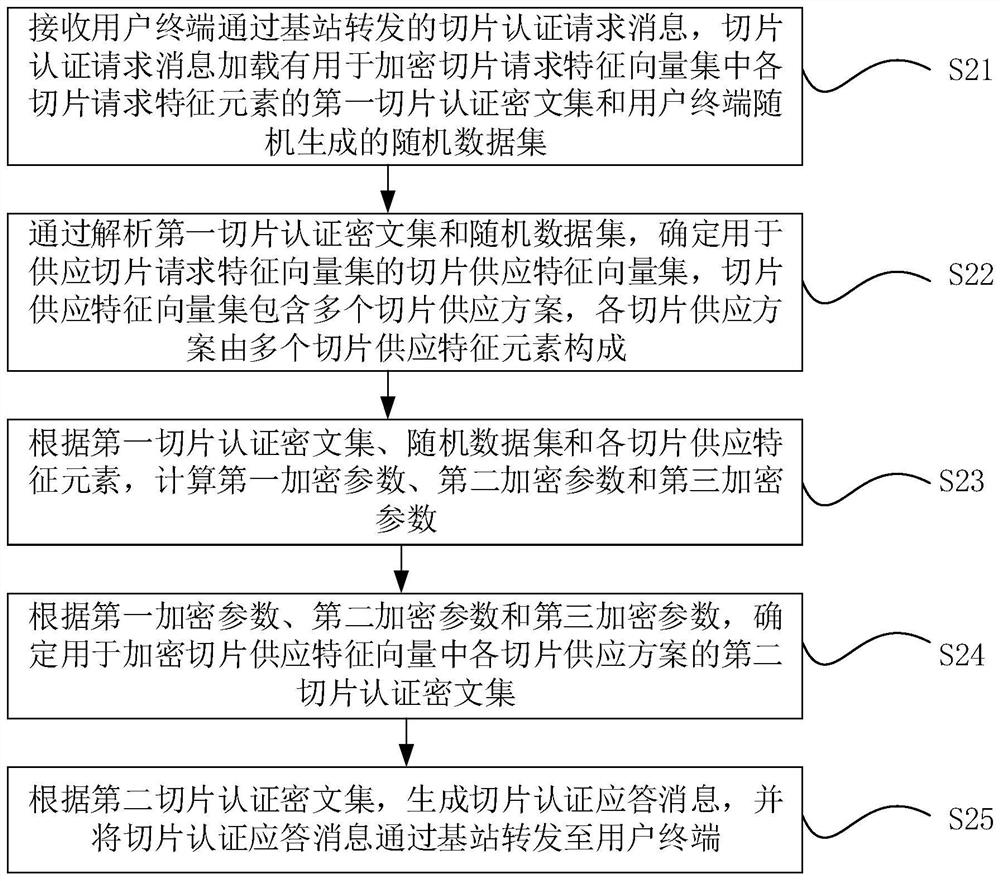
[0086] The embodiment of the present invention also discloses an edge computing-based power 5G network slice authentication message matching method, which is used in a core network element management module. The core network element management module can be represented by AMF, such as figure 2 shown, including the following steps:
[0087] Step S21: Receive the slice authentication request message forwarded by the user terminal through the base station, and the slice authentication request message is loaded with the first slice authentication ciphertext set for encrypting each slice request feature element in the slice request feature vector set and the random data set randomly generated by the user terminal .
[0088] The first slice authentication ciphertext set is shown in the above formula (1), namely F UE '={x' j =x j +rc j ,1≤j≤t}; and the random data set randomly generated by the user terminal is C=(c 1 ,…,c j ,…,c t ).
[0089] After receiving the slice authen...
Embodiment 3
[0106] The embodiment of the present invention also provides an edge computing-based power 5G network slice authentication message matching device, which is used for user terminals, such as Figure 4 shown, including the following modules:
[0107] The slice request feature vector determination module 41 is configured to determine a slice request feature vector set according to service requirements and network characteristics, and the slice request feature vector set includes a plurality of slice request feature elements.
[0108] The first slice authentication ciphertext calculation module 42 is configured to calculate the first slice authentication ciphertext set for encrypting each slice request feature element in the slice request feature vector set according to the randomly generated random data set and random key.
[0109] The slice authentication request message generating module 43 is configured to generate a slice authentication request message according to the random...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com