Double-unmanned-aerial-vehicle 3D trajectory design method for maritime safety communication
A dual-drone, maritime security technology, applied in location-based services, large-scale transport vehicles, safety devices, etc., can solve problems such as blocking communication, drone information transmission eavesdropping, etc., to improve The effect of system security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
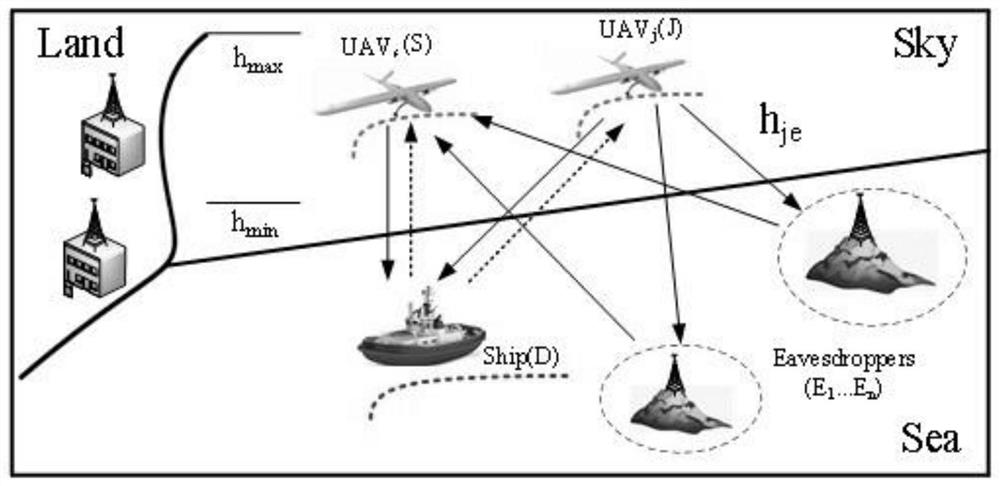
[0096] see figure 1 , UAVs S and J have the functions of information transmission and energy collection. Due to the small size of UAV S and UAV J and insufficient airborne energy, it is necessary to collect energy from the radio frequency signal sent by ship D and store it up to the threshold of its energy collection to meet the information transmission requirements of UAVs. In addition, the drone S transmits information to the ship D. Due to the openness of the RF signal, multiple potential eavesdroppers will eavesdrop on the messages of UAV S, and at the same time, UAV J sends artificial noise to interfere with eavesdropping. The invention jointly optimizes the 3D trajectory and the time slot allocation strategy of the UAV S and the UAV J to maximize the system security rate. It is verified by the simulation in the figure below that this implementation scheme can effectively improve the security performance of the communication system.
Embodiment 2
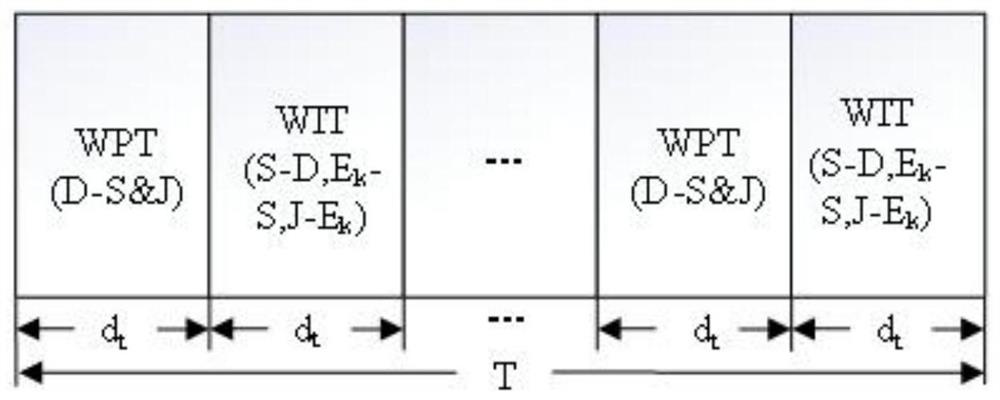
[0098] see figure 2 .Assume the total time of communication transmission is T, which is equally spaced by d t divided into N time slots. The slot switching coefficient α[n] represents the time allocation strategy for energy collection and transmission of information, where α={0, 1}. When α[n]=0, the nth time slot of the UAV is used for energy collection; when α[n]=1, the nth time slot of the UAV is used for information transmission. In particular, the UAV collects energy until its energy harvesting threshold is met.
Embodiment 3
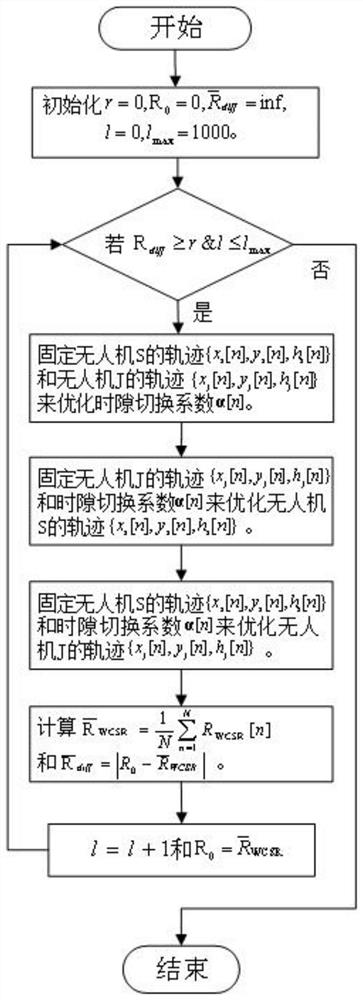
[0100] see image 3 , since the problem is a complex integer non-convex problem, existing algorithms are difficult to solve. This algorithm resolves the problem into three sub-problems and handles the three sub-problems separately.
[0101] For problem 1: given the trajectory of the drone S {x s [n],y s [n], h s [n]} and the trajectory of UAV J {x j [n],y j [n], h j [n]}, optimize the time slot switching coefficient α[n]. In the present invention, the integer α[n] is first continuous, that is, α[n]∈[0,1], then the geometric method is used to approximate the worst position of eavesdropping, and then the linear problem is solved by the simplicity method, and finally the binary value is used. The discriminant method obtains the optimal time slot allocation strategy α[n].
[0102] For problem 2: given the trajectory of drone J {x j [n],y j [n], h j [n]} and time slot switching coefficient α[n] to optimize the trajectory of UAV S {x s [n],y s [n], h s [n]}. The prese...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com