PD controller design method based on malicious software space-time propagation model
A malicious software and propagation model technology, applied to controllers with specific characteristics, electric controllers, etc., can solve problems such as difficult design and single adjustable control parameters, and achieve excellent control effects, strong applicability, and reduced harm Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0065] Embodiments of the present invention will be disclosed in the drawings below, and for the sake of clarity, many practical details will be described together in the following description. It should be understood, however, that these practical details should not be used to limit the invention. That is, in some embodiments of the invention, these practical details are unnecessary.
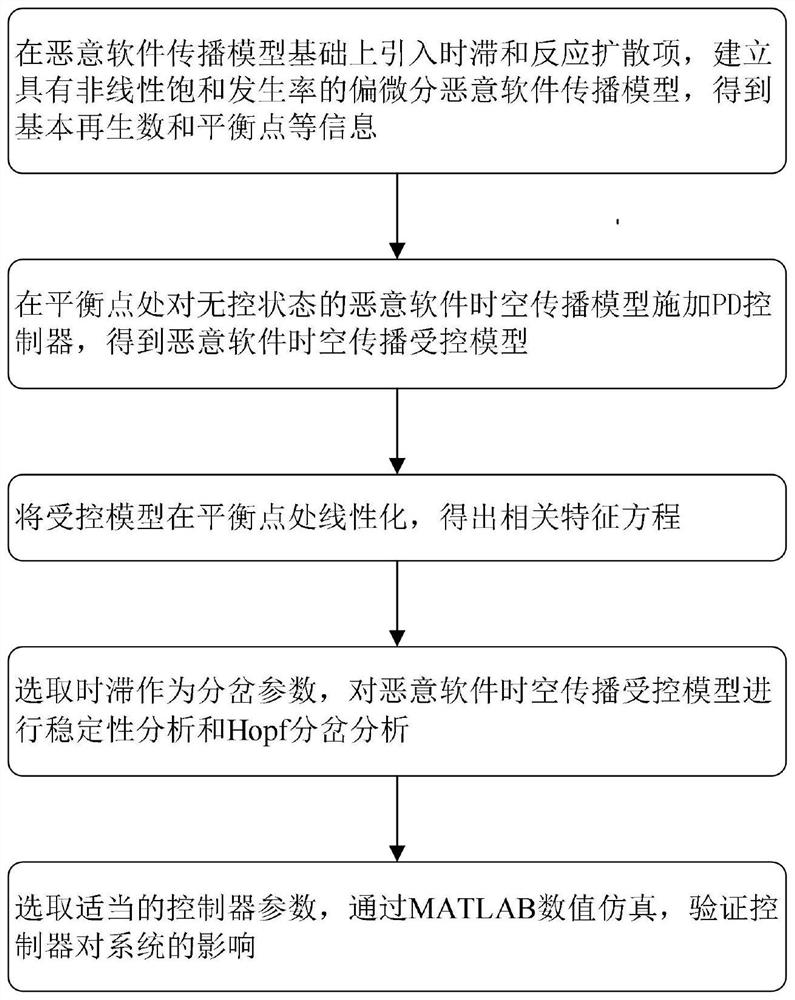
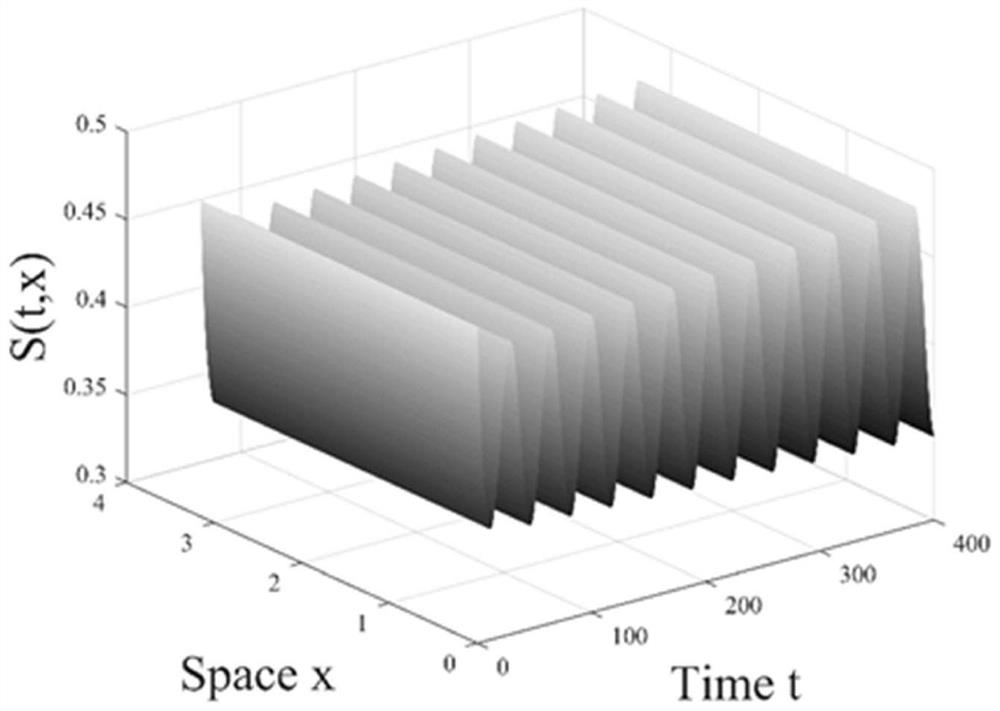
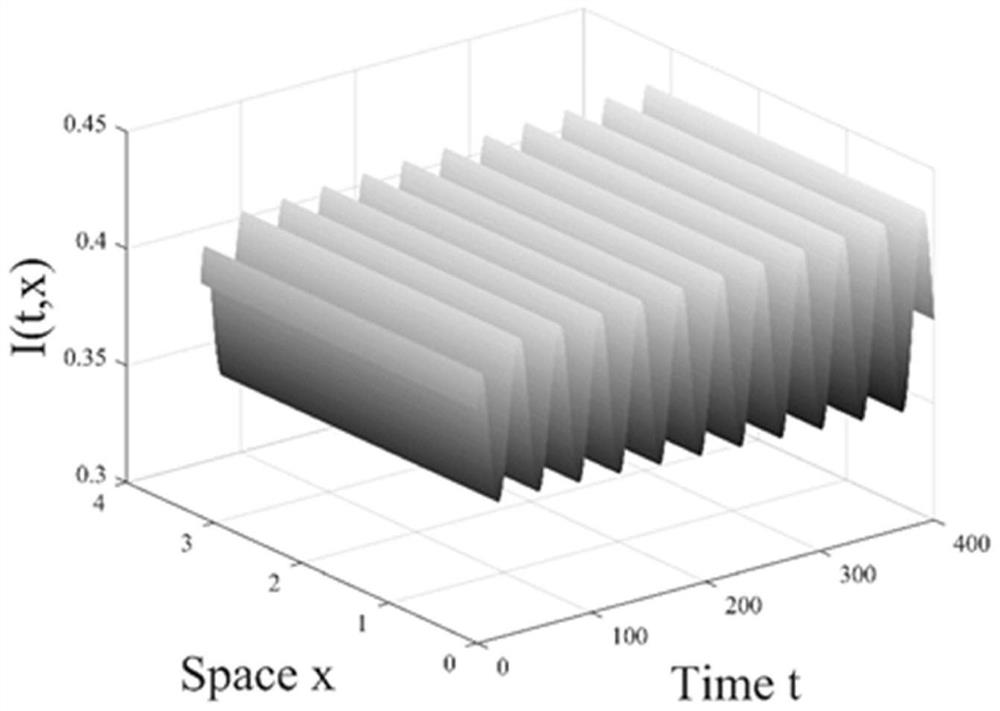
[0066] The present invention is a PD controller design method based on a malware spatiotemporal propagation model, and the method comprises the following steps:
[0067] Step 1: Introduce time delay and reaction-diffusion terms on the basis of the malware propagation model, establish a partial differential malware propagation model with nonlinear saturation occurrence rate, and obtain information such as the basic reproduction number and equilibrium point.
[0068] The described malware-based spatiotemporal propagation model is expressed as:
[0069]
[0070] where t>0, x∈Ω.
[0071] The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com