Public key cryptography algorithm based on problem of classical decomposition of matrix over integral ring
A technology of public key cryptography and cryptographic algorithms, applied in the field of fast public key cryptography algorithms, can solve the problems of unfavorable information security systems and high prices, and achieve the effects of improving decryption efficiency, low cost, and high information security strength
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
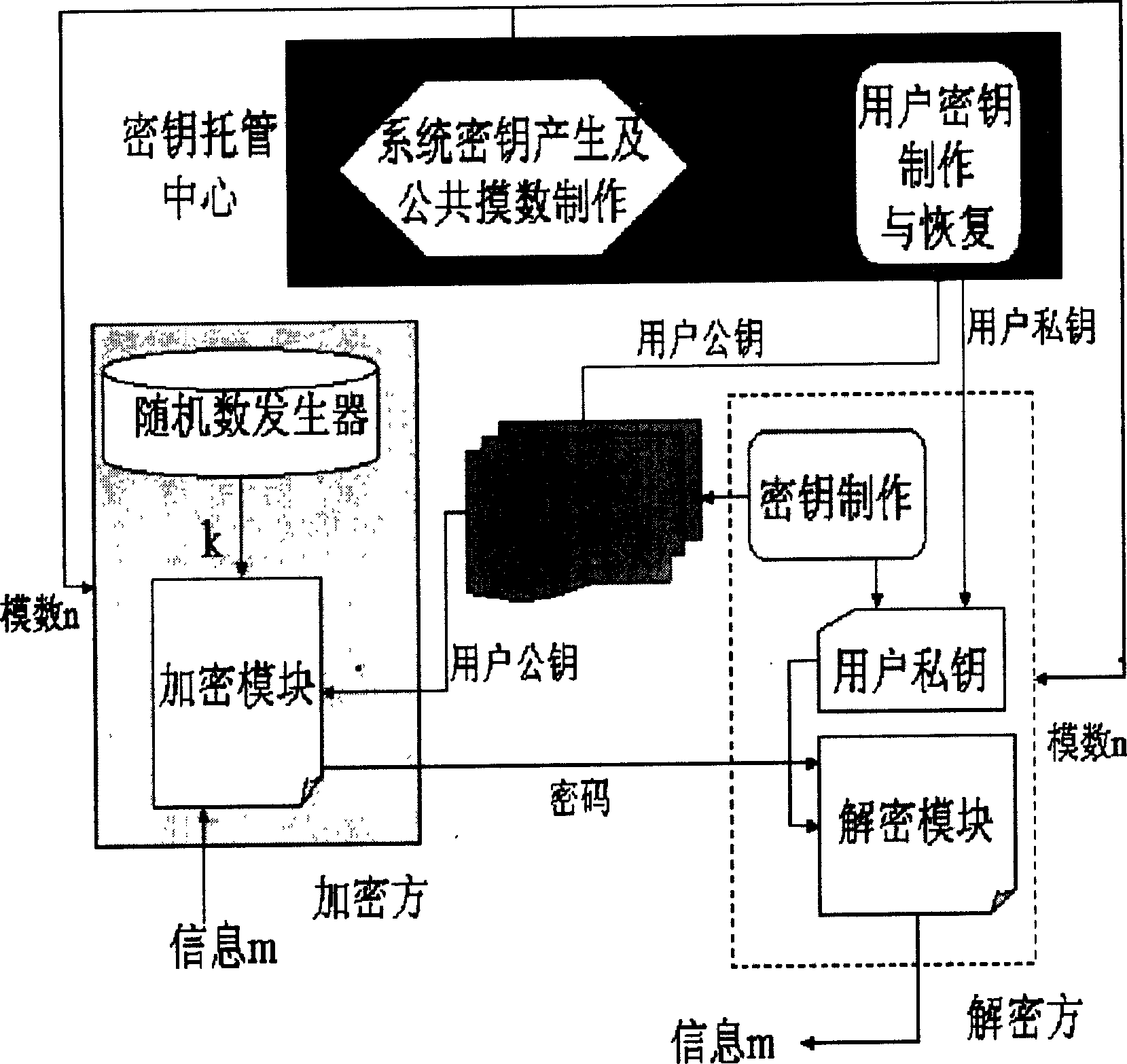
[0020] The specific implementation method of the present invention will be further described below in conjunction with the accompanying drawings.
[0021] (1) System key generation and public modulus production. This module generates the secret primes p and q, and computes the public modulus n=pq. Operation of this module should be carried out under close supervision. The system key is kept by the key escrow center.
[0022] (2) User key creation. First, a random number generator is used to generate a secret random number λ 1 ,λ 2,r , and calculate the user public key σ according to the following formula 1 , σ 2,r ,
[0023] σ 1 =(λ 1 +λ 2 +...+λ r )(mod n), (7)
[0024] σ 2 =(λ 1 lambda 2 +λ 1 lambda 3 +..... 1 lambda r lambda 2 lambda 3 +..... 2 lambda r +..... r-1 lambda r )(mod n), (8)
[0025] σ 3 =(λ 1 lambda 2 lambda 3 +λ 1 lambda 3 lambda 4 +..... 1 lambda r-1 lambda r +λ 2 lambda 3 lambda 4 +..... 2 lambda r-1 lambda r +..... ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com