User authentication method and user authentication system
A technology of user authentication and authentication system, applied in the field of user authentication system, can solve problems such as difficult to effectively prevent illegal access to the system, password leakage to third parties, and password peeking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
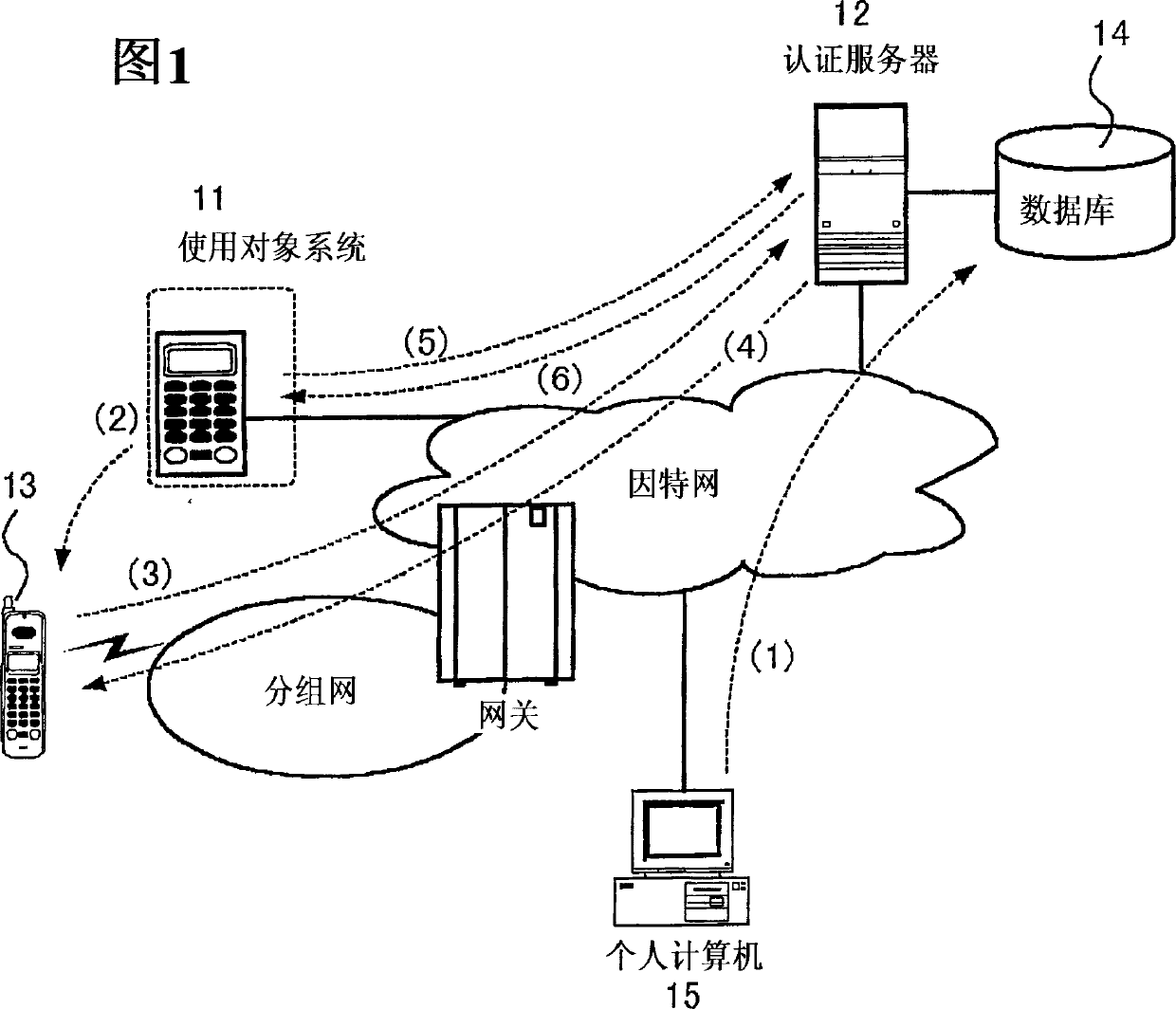
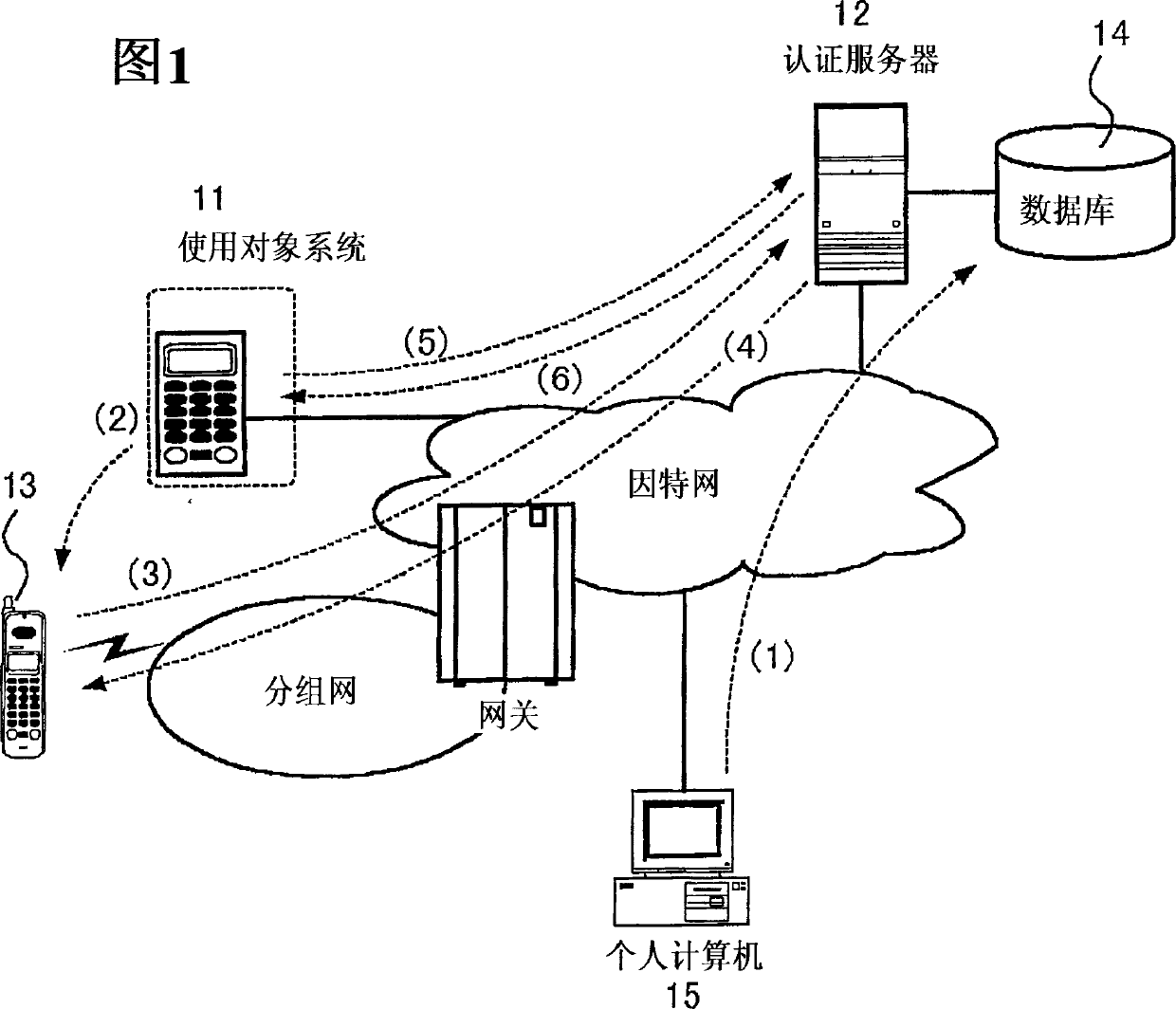
[0054] FIG. 1 is a schematic diagram illustrating an overall scheme of a user authentication method according to the present embodiment. As shown in the figure, the system 11 to be used is connected to the authentication server 12 through a communication line. Here, a case where the target system 11 is connected to the authentication server 12 via the Internet is exemplified. The use target system 11 is a system that requires user authentication when the user uses it. The use target system 11 permits use only to users judged to be legitimate through user authentication processing described later. Typical application examples of the application target system 11 are, for example, a lock switch system for a safe room, a credit card payment terminal device, etc., and it can also be used for a membership site on the Internet realized as a virtual space.
[0055] Such a use target system 11 stores a unique system ID (system identification information) in an internal ROM. And the ...
no. 2 approach
[0106] This embodiment is a modification of the first embodiment, and is characterized in that a password for user authentication is input through the mobile phone 13 instead of the system 11 to be used. Furthermore, in this embodiment, instead of the fixed system ID, when using the use target system 11, a newly generated use ID is used.
[0107] FIG. 15 is an explanatory schematic diagram of an overall scheme of the user authentication method according to the present embodiment.
[0108] First, the user uses the personal computer 15 to register in advance his own password derivation pattern for the use target system 11 in the authentication database 14 ((1) in the figure). When the user actually uses the usage target system 11, in order to obtain the usage ID, the user operates the user interface of the usage target system 11 to display the usage ID ((2) in the figure). The use target system 11 acquires the time information of the operation, applies a random number generatin...
no. 3 approach
[0113] This embodiment relates to a login method using a password derivation mode using a mobile phone 13, and is characterized in that: the authentication server 12 presents candidates for a password derivation mode to the mobile phone 13, and the user selects from the presented candidates for a password derivation mode .
[0114] FIG. 16 is a diagram showing an example of a password derivation mode login screen displayed on the mobile phone 13 . Like the above-mentioned embodiment, for example, when logging in the user account to the target system 11, the authentication server 12 sends an email including the URL of the page data constituting the login screen to the user's mobile phone 13 by email, and the user who receives the email By selecting the URL in the contents of the mail displayed on the mobile phone 13, the login screen is provided to the mobile phone 13.
[0115] That is, when the authentication server 12 receives a password derivation pattern registration reque...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com