Method for implementing function test by safety chip under DOS
A security chip and function detection technology, which is applied in the field of computer information security, can solve the problems that there is no convenient detection method for security chips, and there is no method and device for rapid detection of production lines, so as to reduce workload and improve production efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
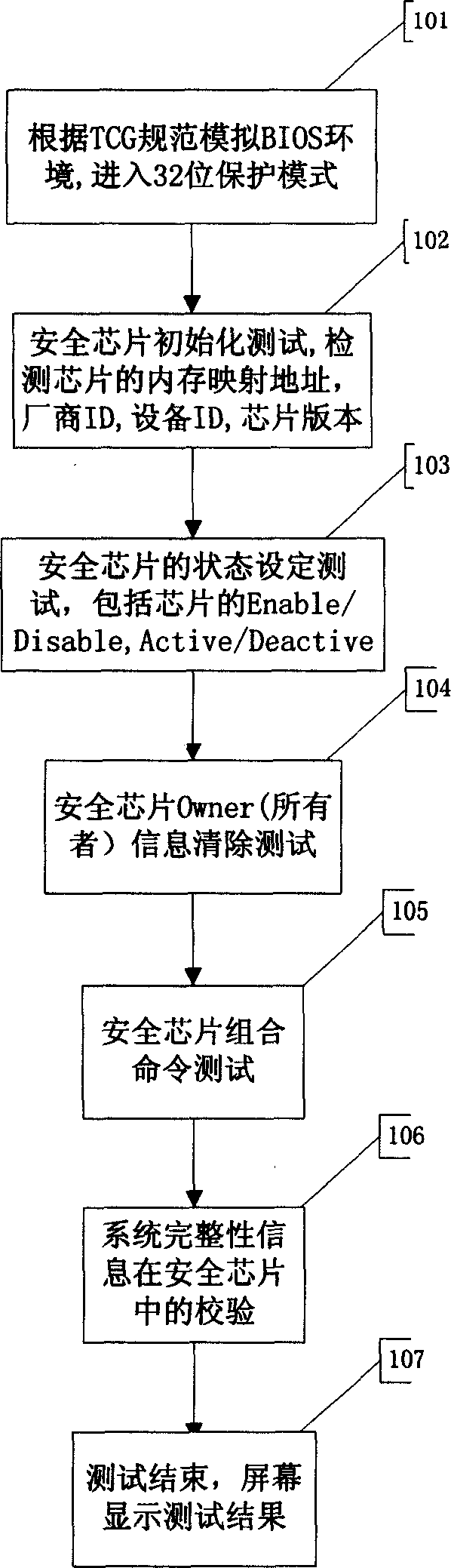
[0029] The method for realizing the function detection of the security chip under DOS of the present invention, its test program first establishes a DOS test environment, which is established according to the TCG specification and belongs to the 32-bit protection mode; under this mode, the test program calls the security chip manufacturer Released MP (Memory Present) driver for testing. This driver is directly provided to the BIOS manufacturer, and is used for the BIOS to perform various settings and information interaction interfaces for the security chip during the power-on self-check process.
[0030] The test idea of the method of the present invention is to simulate the system BIOS environment of the motherboard manufacturer, that is, to communicate with the security chip under the 32-bit protection mode environment defined by the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com