Secret information setting device and secret information setting method
A technology for secret information and setting device, applied in key distribution, can solve the problem of no consideration, and achieve the effect of maintaining security and preventing leakage of secret information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 Embodiment approach
[0102] Figure 11 It is a diagram showing a configuration example of a communication system to which the secret information setting method according to the first embodiment of the present invention is applied. exist Figure 11 In the above, it is assumed that there are the following mobile dedicated terminals, etc., equipped with a home gateway connected to the home network 303 - the network home appliance terminal 301; equipped with a network camera connected to the home network 303 - the network home appliance terminal 302; The secret information setting device 100 is an LSI programmed in the function of generating and setting secret information.
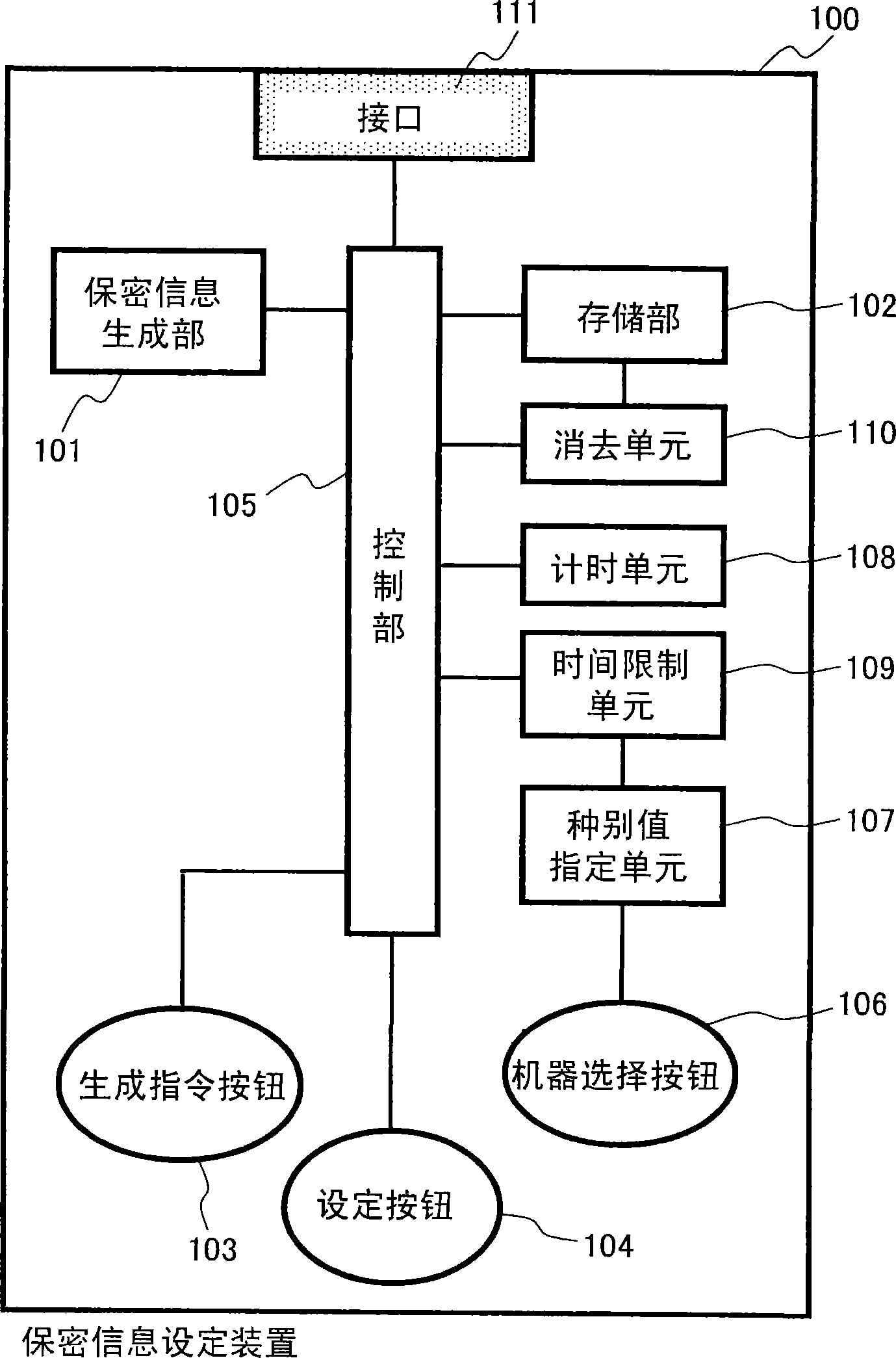
[0103] in addition, figure 1 It is a functional block diagram showing the configuration of the confidential information setting device 100 employed in the first embodiment of the present invention.
[0104] exist figure 1 Among them, the confidential information setting device 100 has: an interface 111 for sending and receiv...
no. 2 Embodiment approach
[0135] Next, a second embodiment of the present invention will be described.
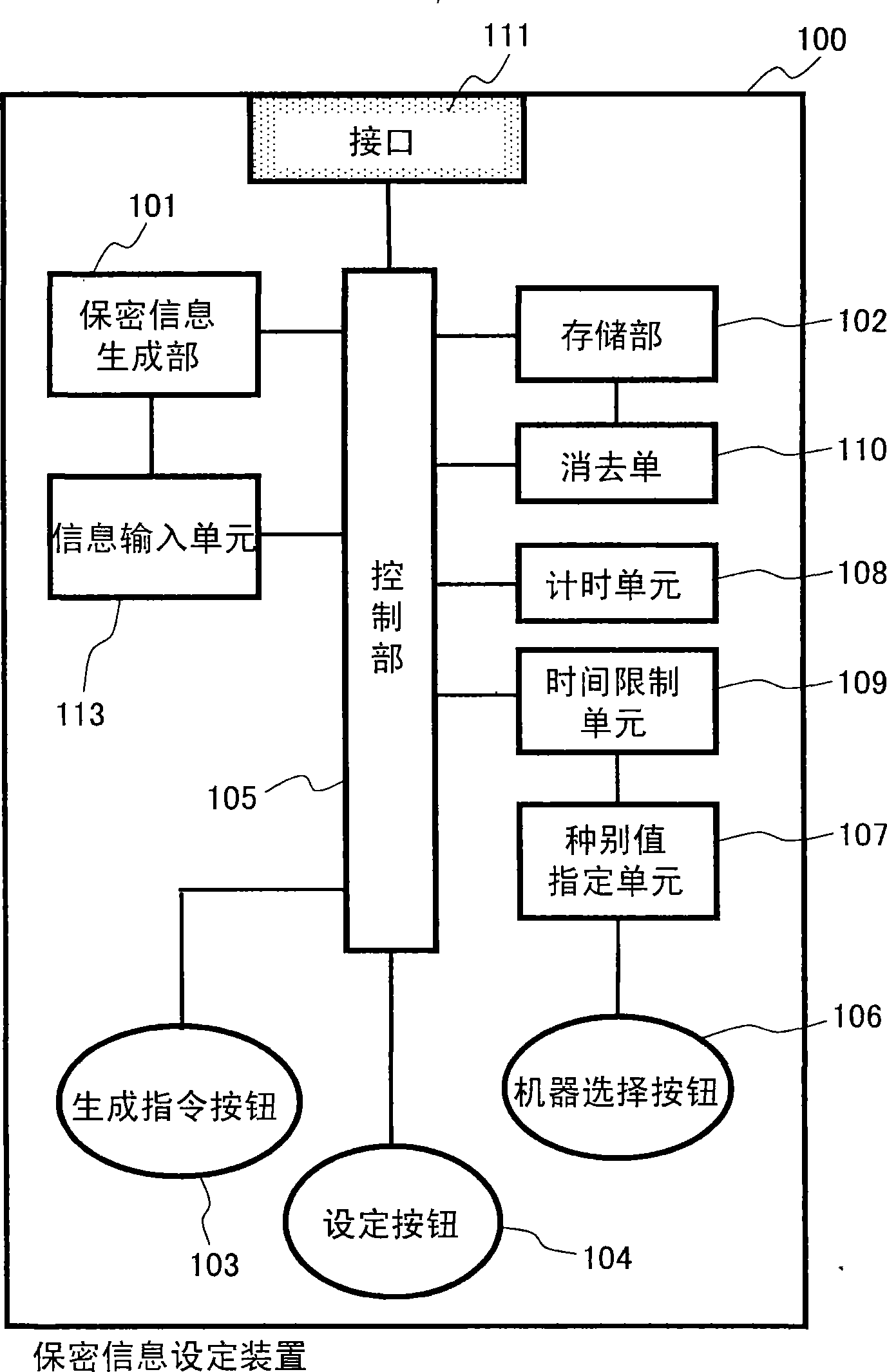
[0136] In the first embodiment described above, a configuration is adopted in which confidential information is automatically generated inside the confidential information setting device 100 when the generation command button 103 is pressed. In contrast, in the second embodiment, an information input unit 113 for inputting confidential information or elements of the confidential information is further provided, receives external information input from the outside, and generates confidential information based on the external information.
[0137] image 3 It is a functional block diagram showing the configuration of the confidential information setting device 100 according to the second embodiment of the present invention. image 3 shown in the functional block diagram, with figure 1 The functional block diagram shown is different in that an information input unit 113 is provided. other constitue...
no. 3 Embodiment approach
[0151] Next, a third embodiment of the present invention will be described.
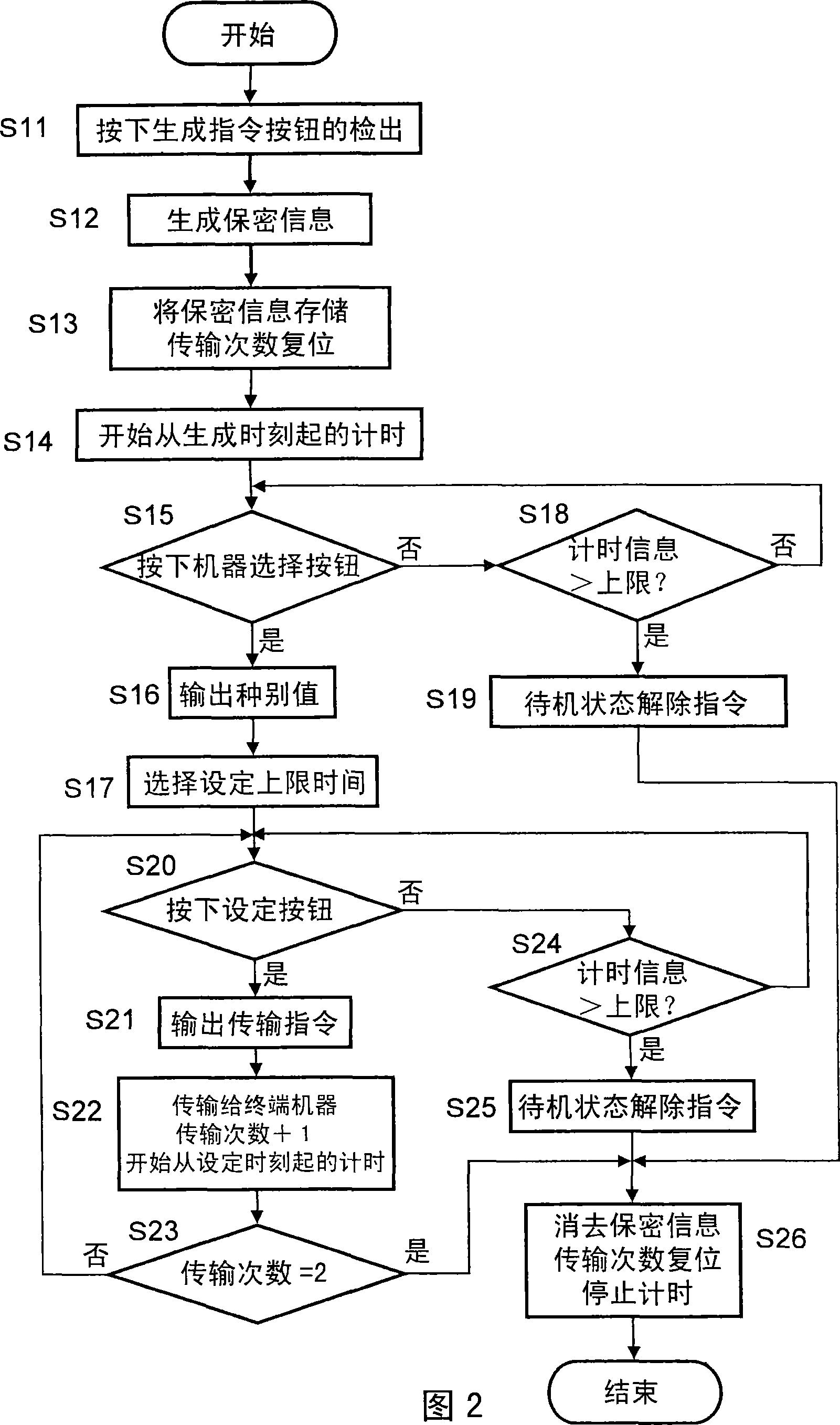
[0152] As described above, in the first embodiment, after the predetermined upper limit time expires, the confidential information is deleted. On the other hand, in the third embodiment, the upper limit time can be extended.
[0153] Figure 5 It is a functional block diagram showing the configuration of the confidential information setting device 100 according to the third embodiment of the present invention. Figure 5 shown in the functional block diagram, with figure 1 The illustrated functional block diagram differs in that an extension command button 114 is provided. other constituent elements, and figure 1 same, so yes and figure 1 The same constituent elements are given the same symbols, and will not be repeated here.
[0154] exist Figure 5 Among them, the confidential information setting device 100 has: an interface 111, a confidential information generating unit 101, a storage un...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com