Method and system for establishing a communication using privacy enhancing techniques
A communication and data communication technology, applied in transmission systems, digital transmission systems, payments involving neutral parties, etc., to achieve the effect of solving technical obstacles
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
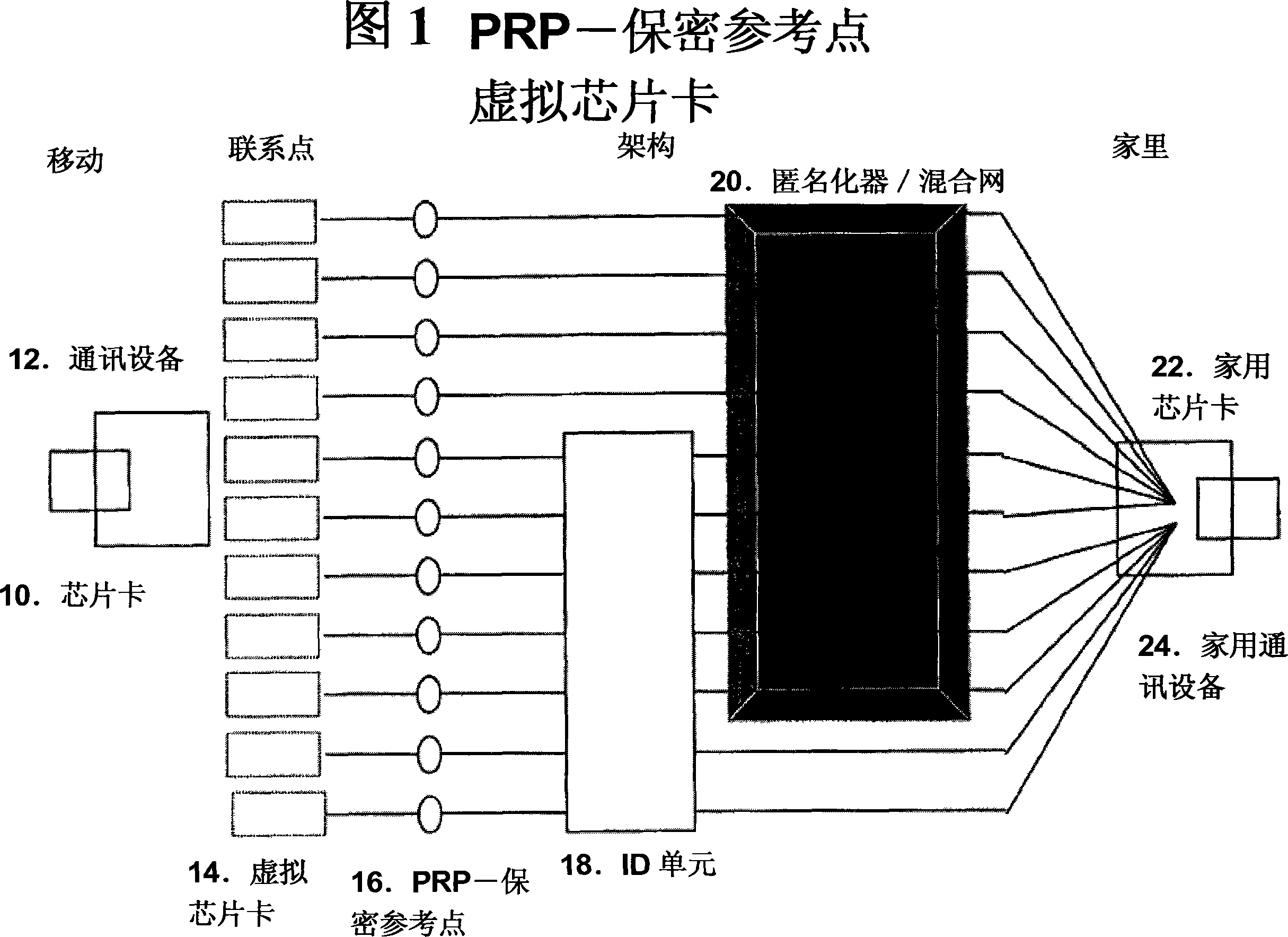
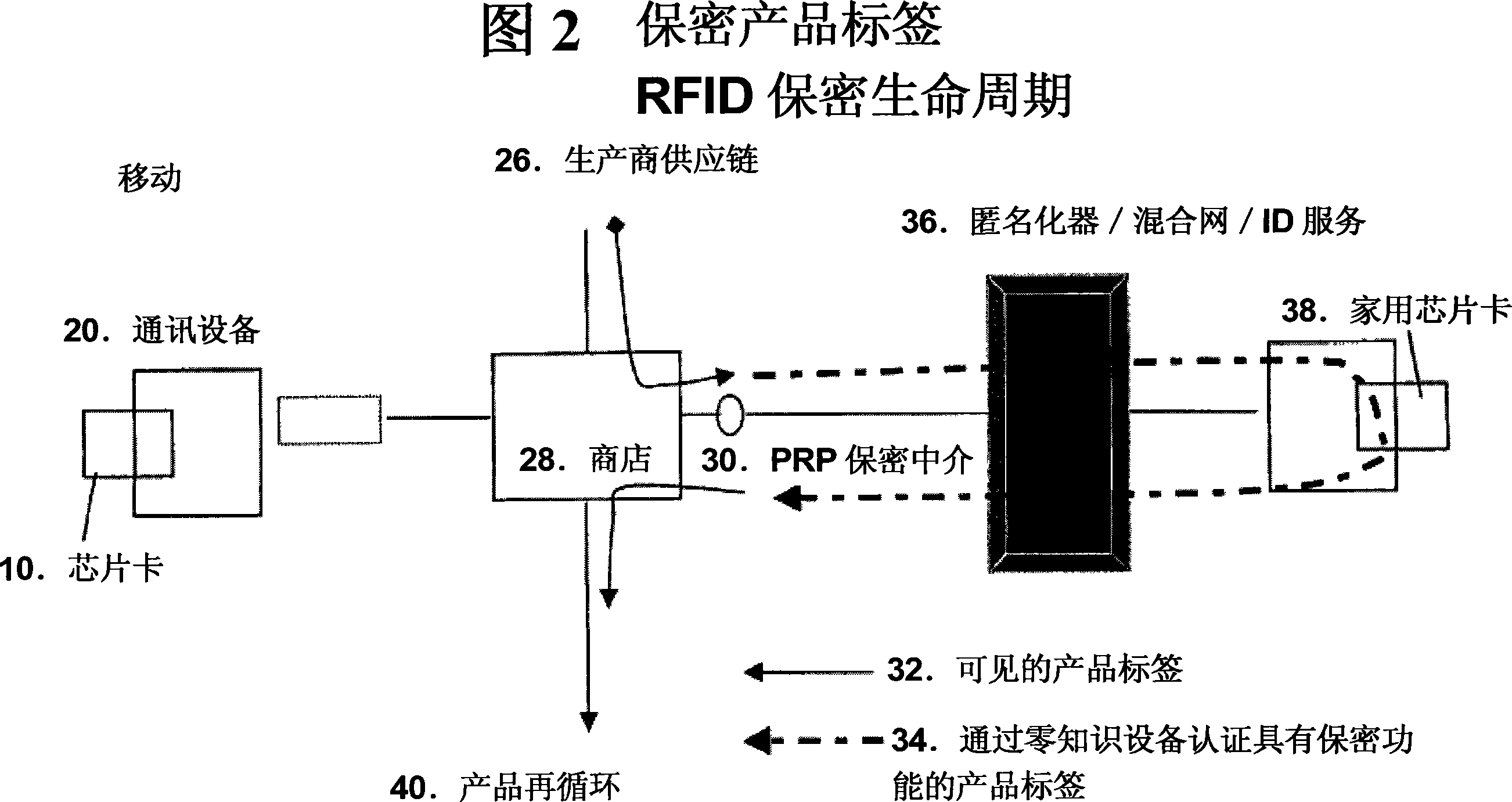
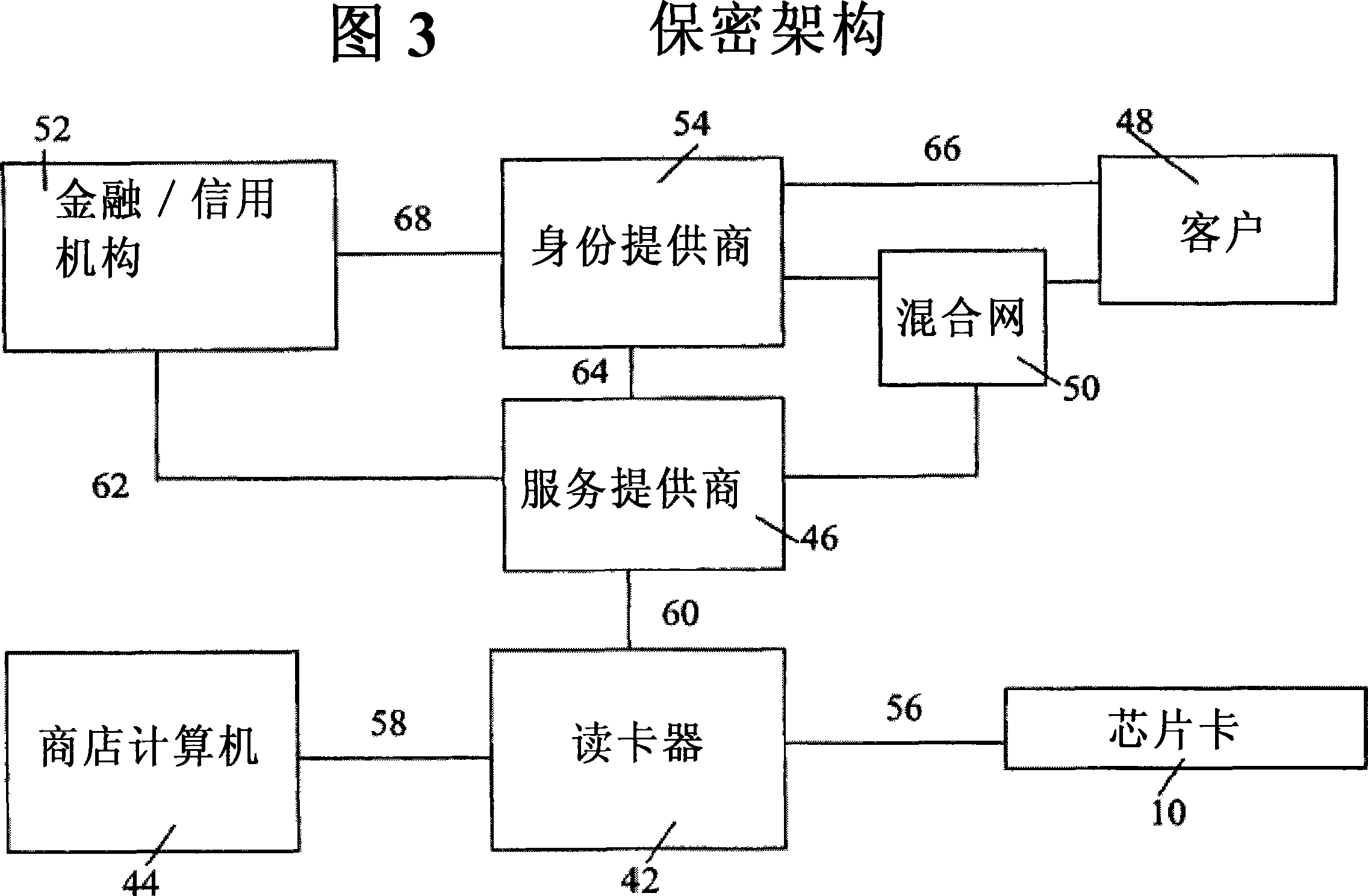
[0070] Figure 3 shows a preferred configuration of a multi-application chip card infrastructure. The chip card 10 communicates with the card reader 42 via the communication channel 56 over an IP connection of a fixed network or over another compatible open protocol, such as a wireless channel, with the card reader 42 . The card reader is connected to the merchant computer 44, in another embodiment the card reader is directly linked using eg a wireless communication protocol. This one-time reference is forwarded to the service provider 46 together with the instructions encrypted in the chip card. Clients link from their client base station 48 to control transactions through a mixnet or other anonymous network 50 or identity provider 54 / pseudonym unit through either communication channel 66 without revealing their true identity. Depending on the encrypted instructions, the service provider 46 can work with the financial institution 52 to directly verify the anonymous payment o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com