Network data isolation system and data transmission method
A technology that isolates systems and network data, applied in the field of network security, and can solve problems such as attacking network systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
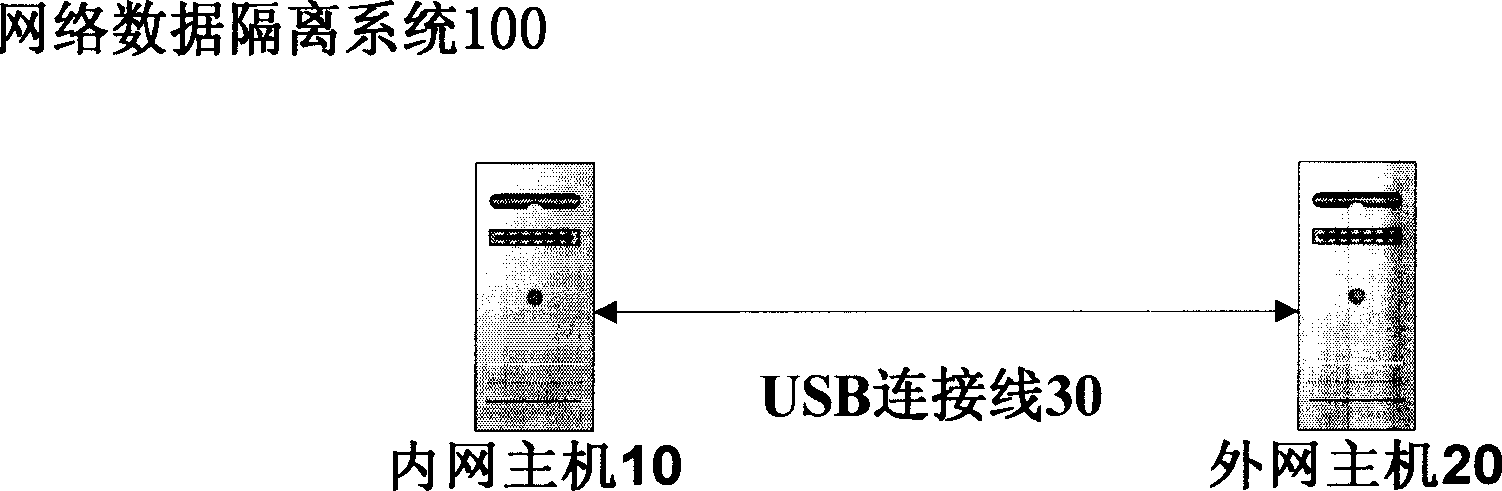
[0015] A network data isolation system 100 includes an internal network host, an external network host, and a serial interface connector, wherein the serial interface connector is respectively connected to the serial interface of the internal network host and the serial interface of the external network host.
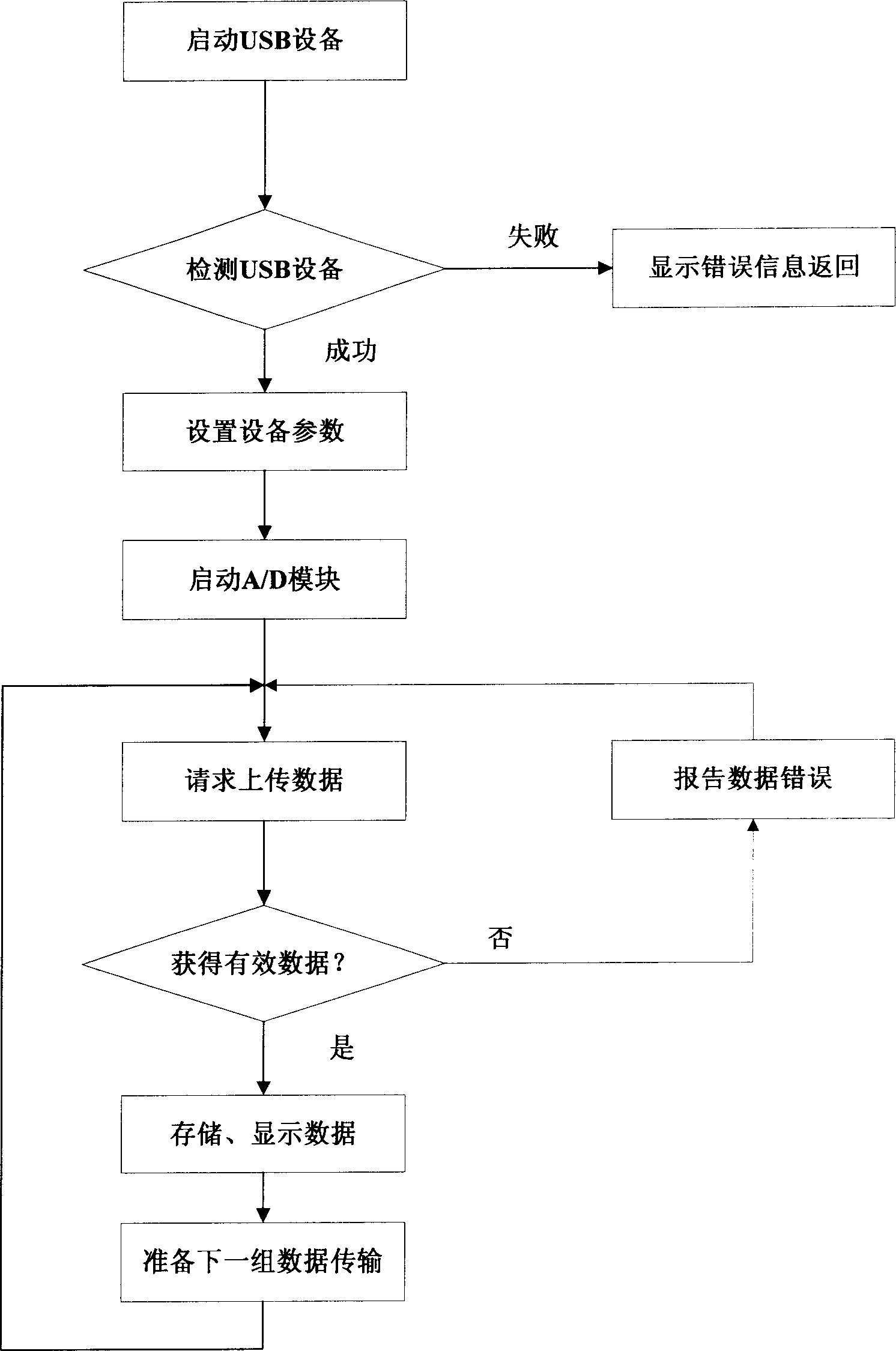
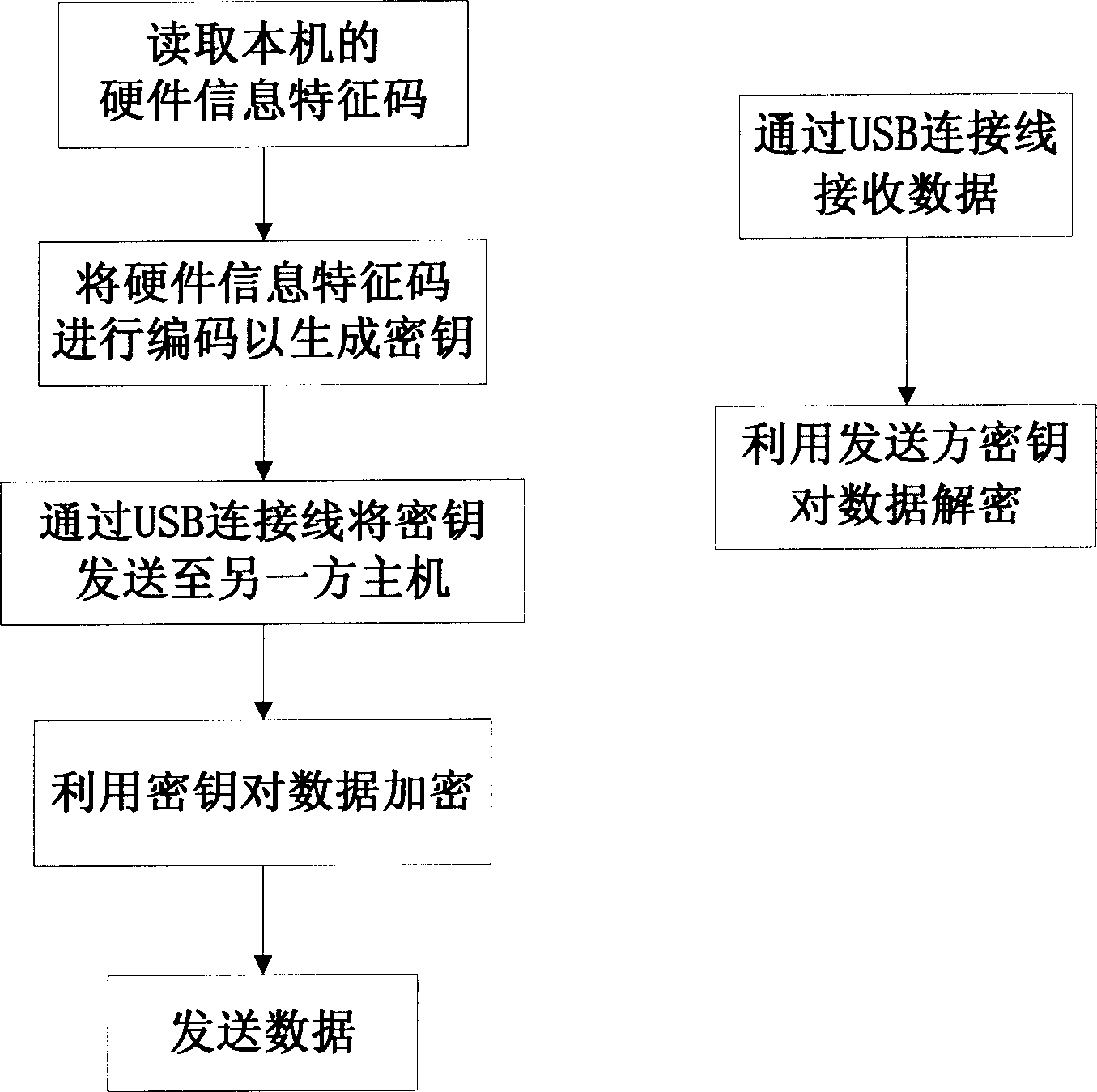
[0016] figure 1 is a schematic diagram of a network data isolation system 100 according to an embodiment of the present invention. Two hosts (i.e., an internal network host 10 and an external network host 20) are used to control data exchange between the internal network and the external network. The internal network host 10 and the external network host 20 can be desktop computers or servers. The internal and external network hosts do not share any data of each other, nor do they have the right to log in or control the other party's system, but only receive and send data through a specific serial interface connector (ie, a USB cable). The serial interface connector i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com