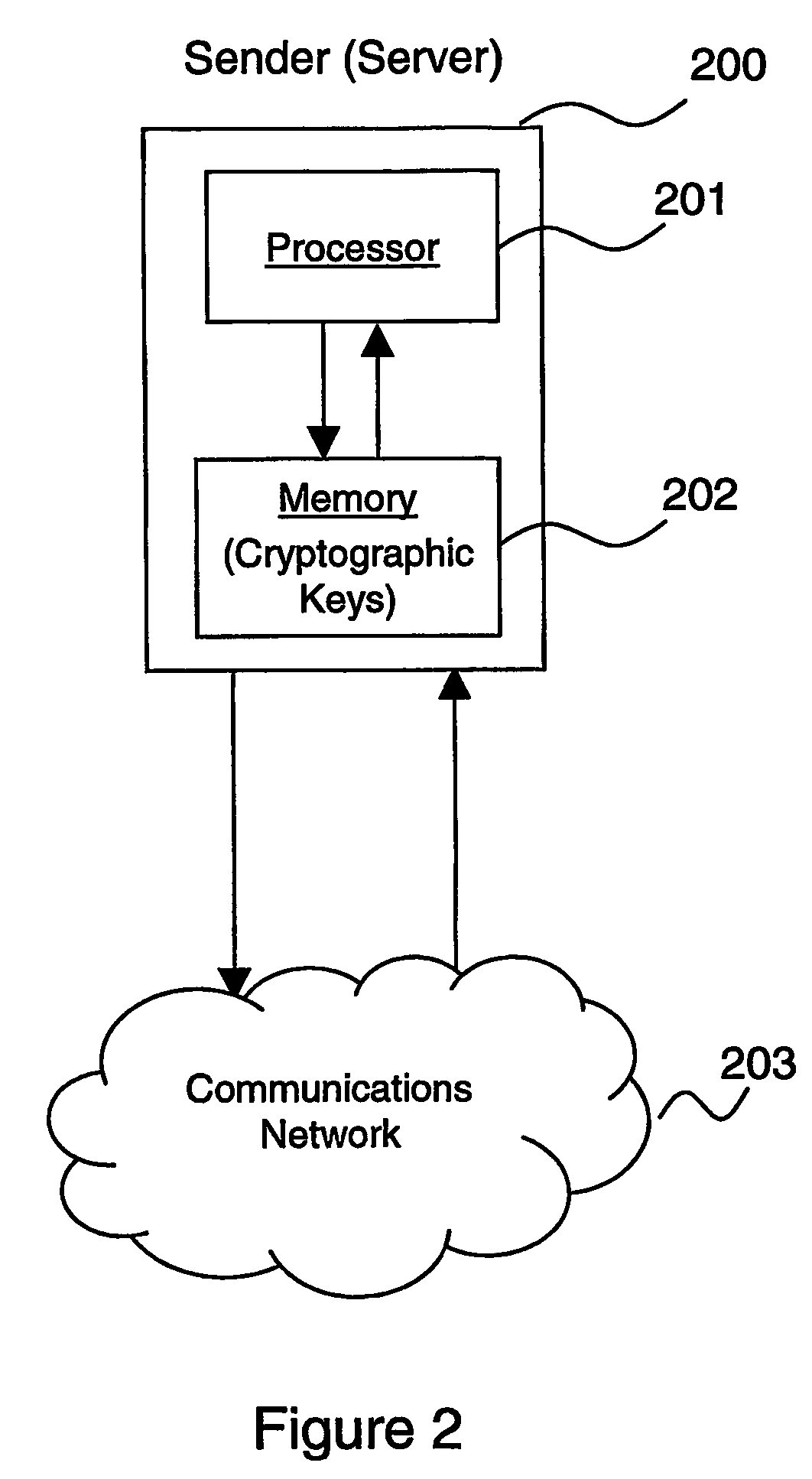
Method and apparatus for authentication of data streams with adaptively controlled losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
[0085] The scheme of the first embodiment permits the role of an intermediary which can adaptively and intelligently choose to remove any number of blocks without requiring knowledge of any cryptographic keying material. Moreover, the intermediary can be proximate to the receiver and can control the loss (and therefore the amount of hash information) dynamically. Furthermore, the authentication information can be verified in an online manner by the receiver. That is, the receiver can verify the authentication information as it receives the stream, and will not be required to do any form of extensive buffering. Also, the first layer hash computations are not required for any block that will not be dropped. For example, an MPEG I-frame or the base layer of a scalable coding scheme will not be intentionally dropped. For these blocks, only the second layer is required. In this instance, the first layer hash function for that block can be replaced with the identity function h(x)=x. In a ...
third embodiment
[0104] Now, assume the original sender S transmits k different streams M(1), M(2), . . . , M(k) simultaneously. Each stream consists of n blocks of length b, M(j)=M1(j), . . . , Mn(j). The scheme of the third embodiment allows the intermediate node not only to select one stream and retransmit it in an authenticated fashion, but also to “switch” to some other stream adaptively (at any point during block transmission). Of course, the receiver should be able to authenticate the resulting stream.
3.1 Signing
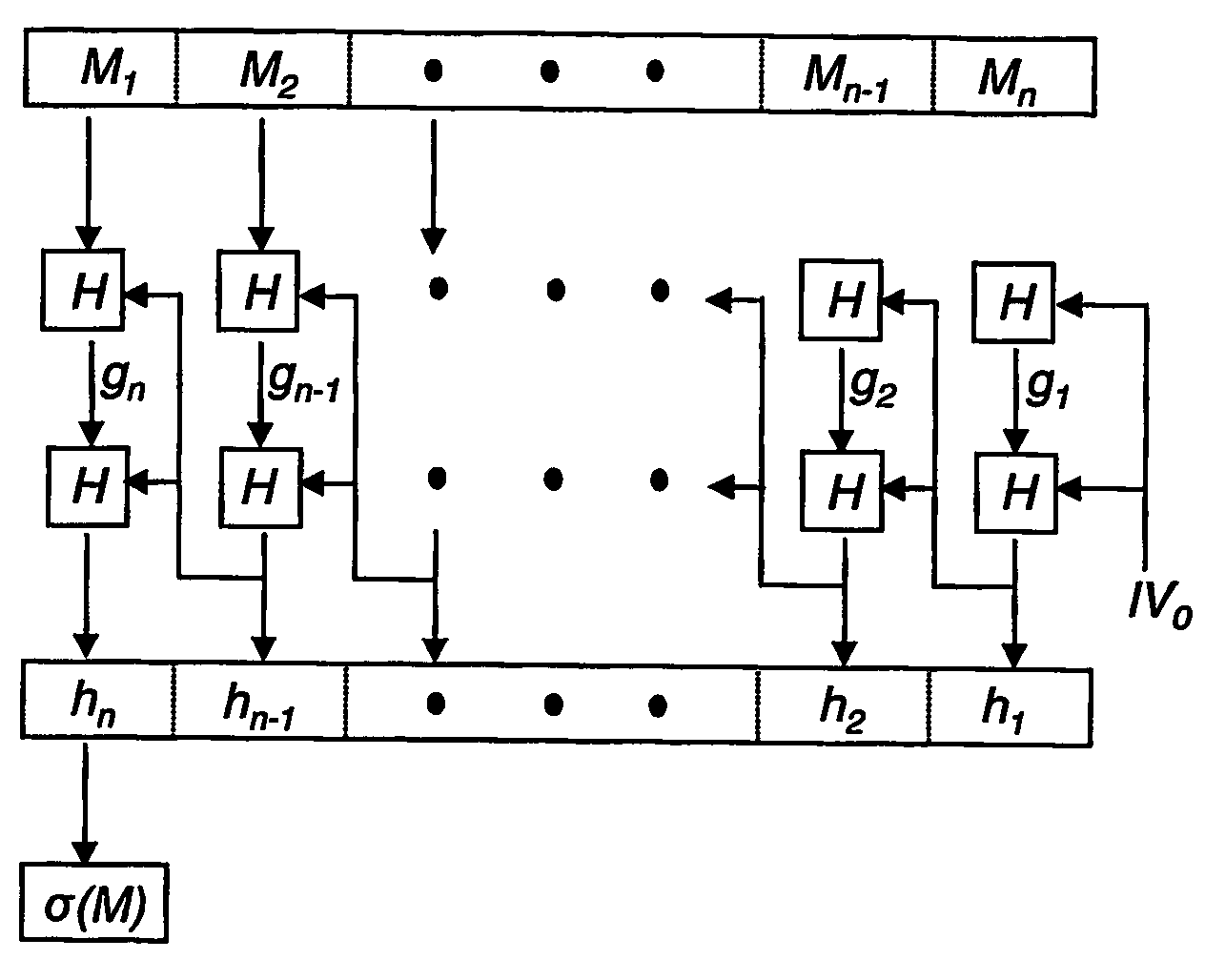
[0105]FIG. 9 shows a basic linear simulcast authentication scheme according to one embodiment of the present invention. Given a message M, signature generation follows the same approach as in the first and second embodiments, i.e., reverse iterated hash, but computing partial hashes of every block in each stream.
[0106] Given messages M(1), M(2), . . . , M(k), where M(j)=M1(j), M2(j), . . . , Mn(j), the scheme of the third embodiment of the present invention generates the partial ha...
fourth embodiment
[0119] the present invention is a scheme for authenticating subsequences using Merkle Trees. Like the linear subsequence authentication scheme, the tree-based scheme allows stream authentication even when arbitrary blocks from the message are removed. As long as the blocks sent by the intermediate node are a proper subsequence of the original message, the receiver can authenticate the stream. By exploiting certain aspects of the tree structure, the tree scheme is more efficient with respect to bandwidth than the linear scheme.
4.1 Signing
[0120]FIG. 10 illustrates a tree-based subsequence authentication scheme according to one embodiment of the present invention. Given a message M=M1M2 . . . Mn, the scheme of the fourth embodiment generates a Merkle tree shown in FIG. 6. If v denotes the root of the tree and x denotes the value associated with the root, then the initial sender transmits (M, σSk(x)).
4.2 Signature Update
[0121] If an intermediary wants to strip off k arbitrarily loc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com