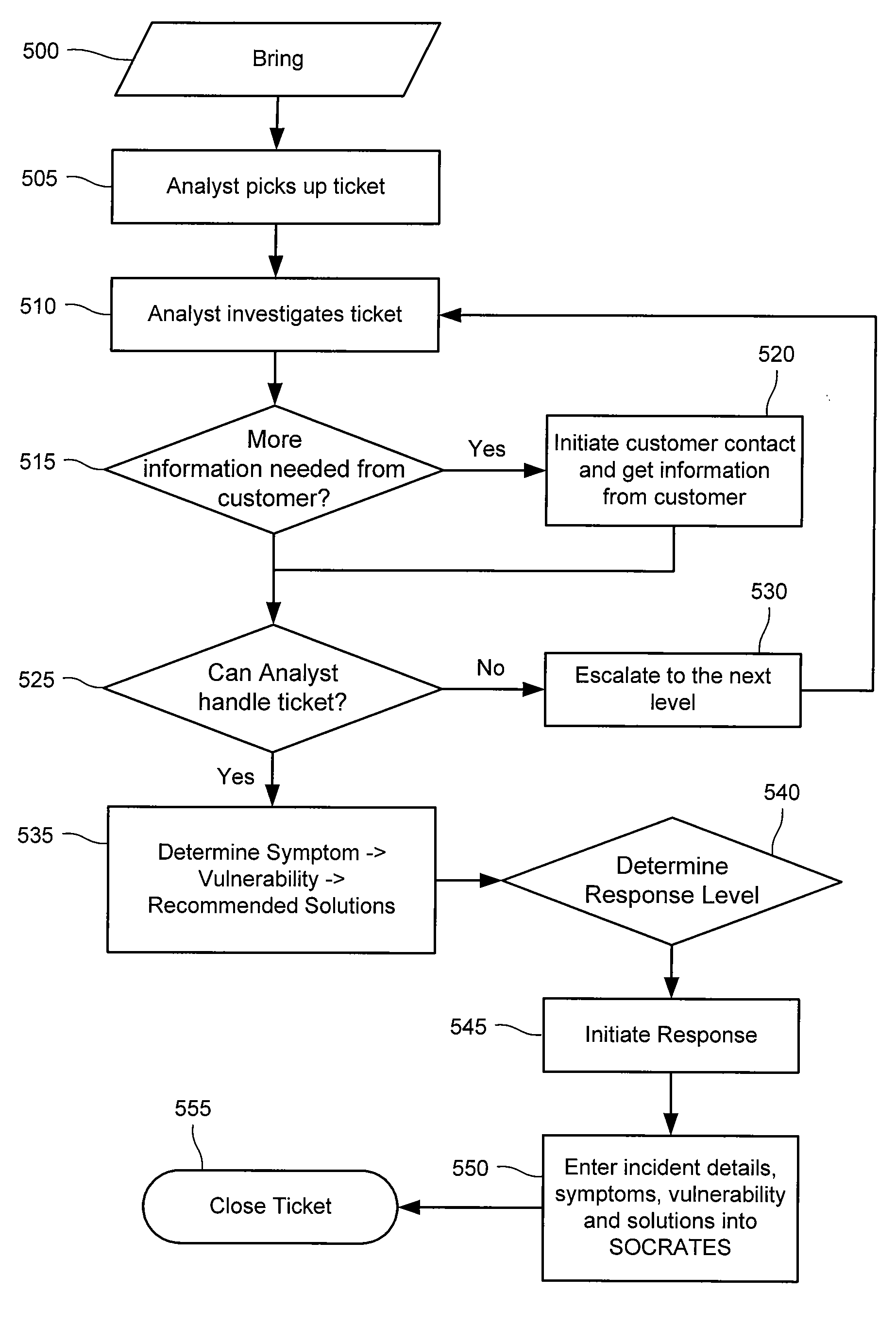
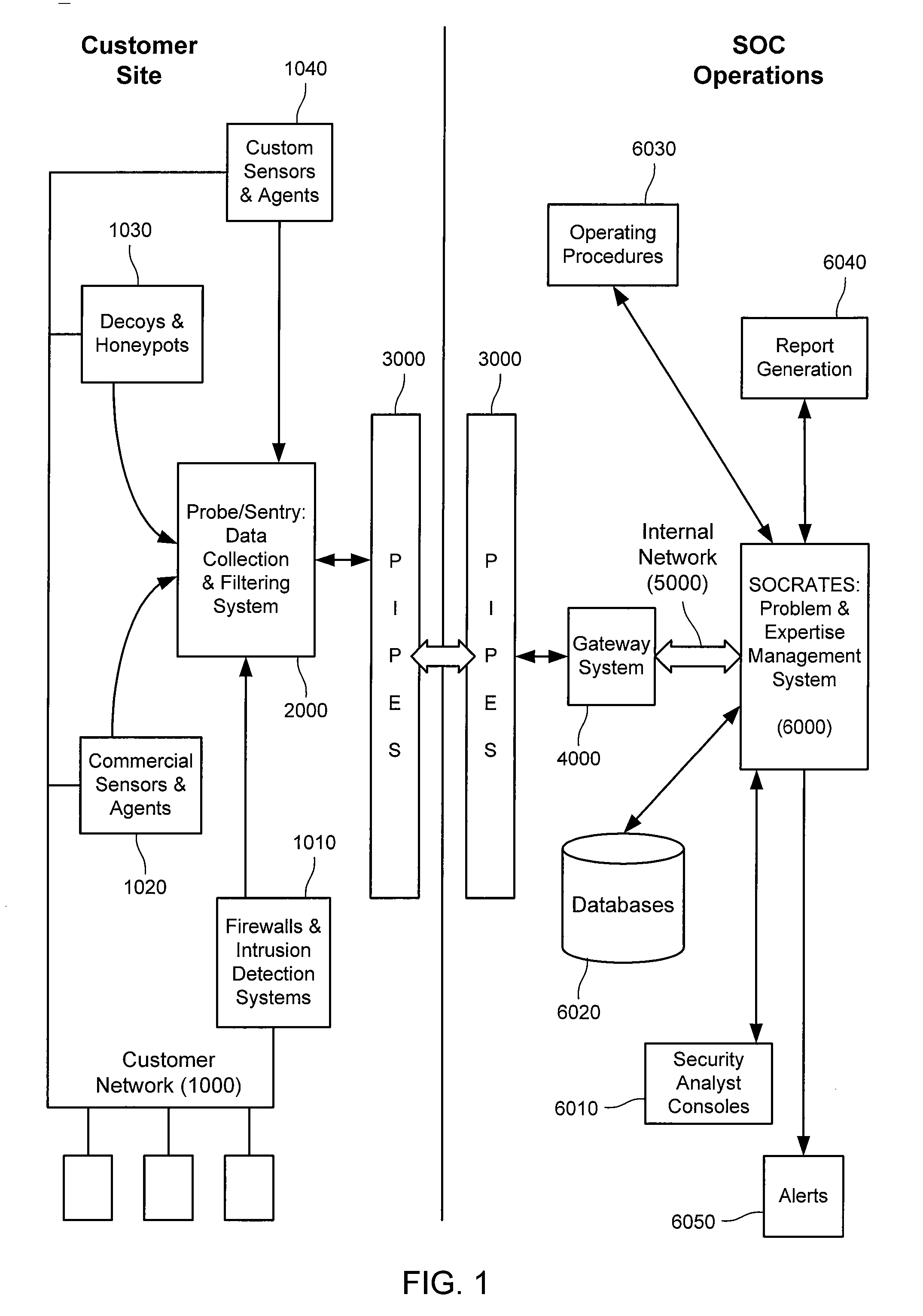
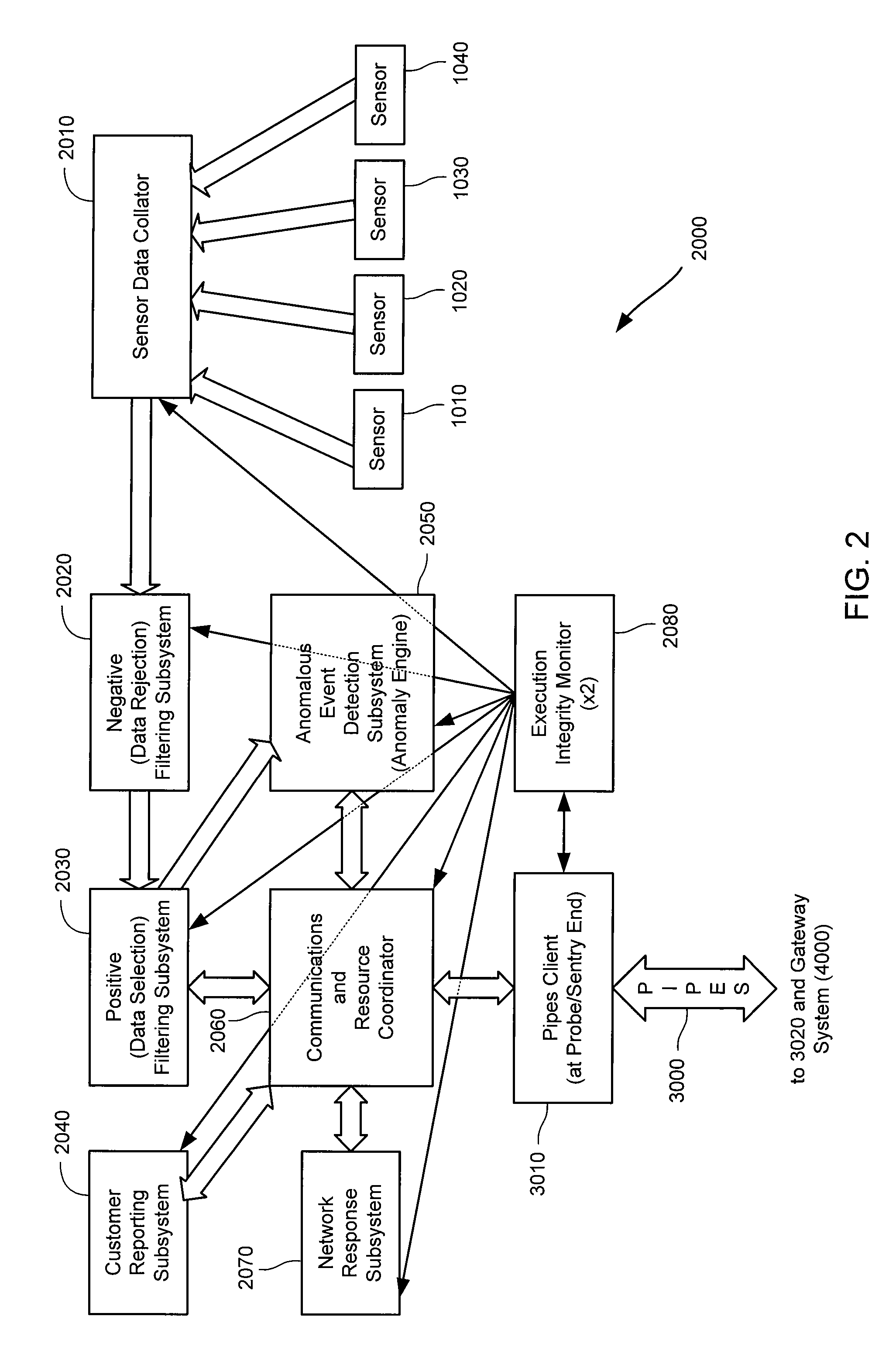
Method and System for Dynamic Network Intrusion Monitoring, Detection and Response
a dynamic network and intrusion detection technology, applied in the field of network security, can solve problems such as system administrators who do not have the time or ability to read through large amounts of constantly updated audit information, and cannot be continuously monitored by hackers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example message
“001f 00003333 1111 2222X ALRT 12345678”
Notes [0125] 1. All the above fields should have spaces between them. [0126] 2. The first four-digit group is the length of everything after it (LENGTH) (the space through the end of “12345678”). [0127] 3. The second four-digit group is the revision field (REVISION). [0128] 4. The third four-digit group is the probe / sentry number, which identifies a particular probe / sentry (“3333” in the example). [0129] 5. The fourth four-digit group is the reference number defined by the probe / sentry system (REFNUM)(“1111” in the example). [0130] 6. The fifth four-digit group is the status number defined by the probe / sentry system (STATUS) (“2222” in the example). [0131] 7. The next one-digit field (“X”) is the keyed Media Access Control (KMAC) value, if present. If not present, the value should be an “X.”[0132] 8. The next field is the op code (OPCODE). For filter-related messages, it is always “ALRT.”[0133] 9. The portion of the message after the space af...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com