System for automatically shadowing encrypted data and file directory structures for a plurality of network-connected computers using a network-attached memory with single instance storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
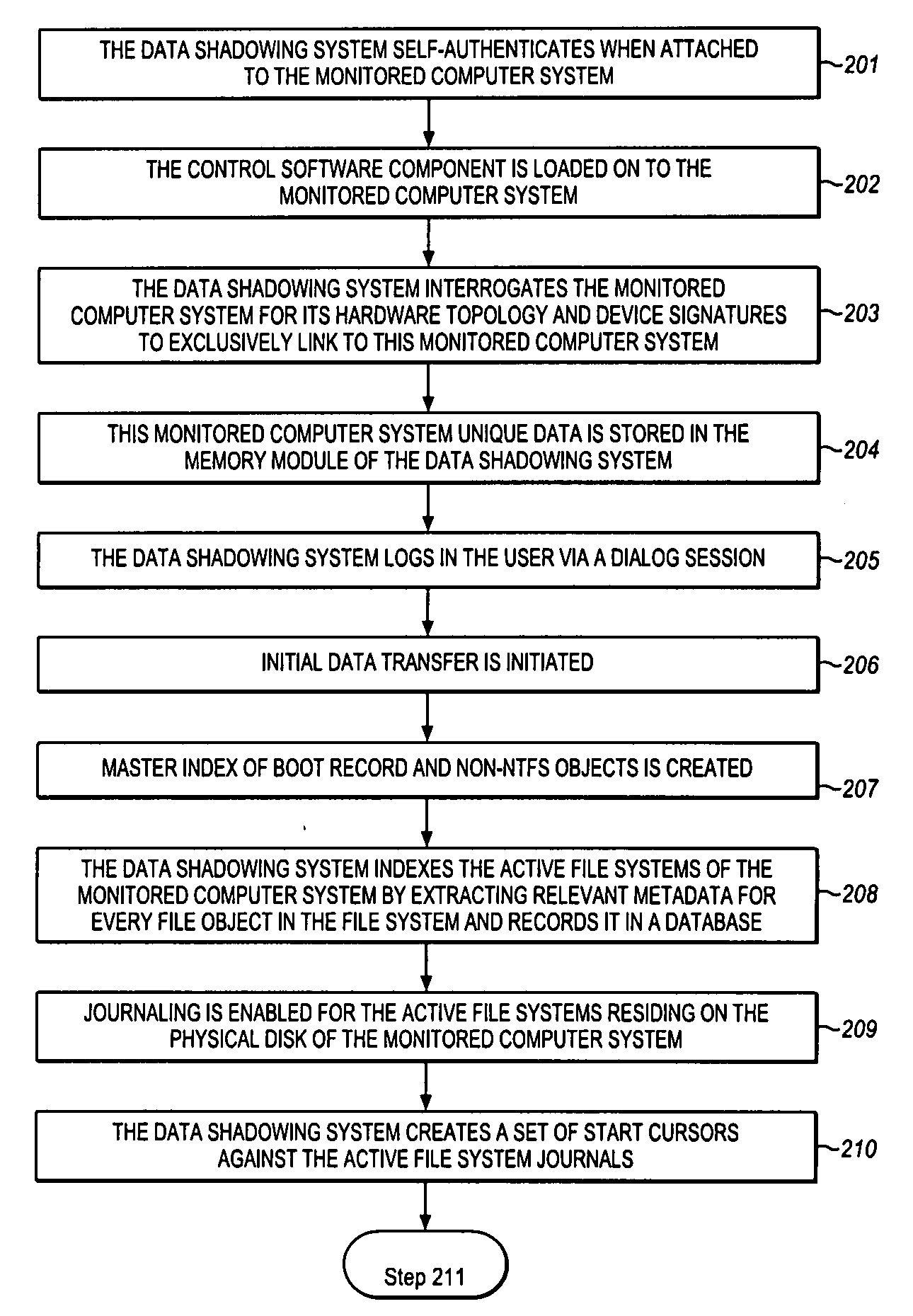
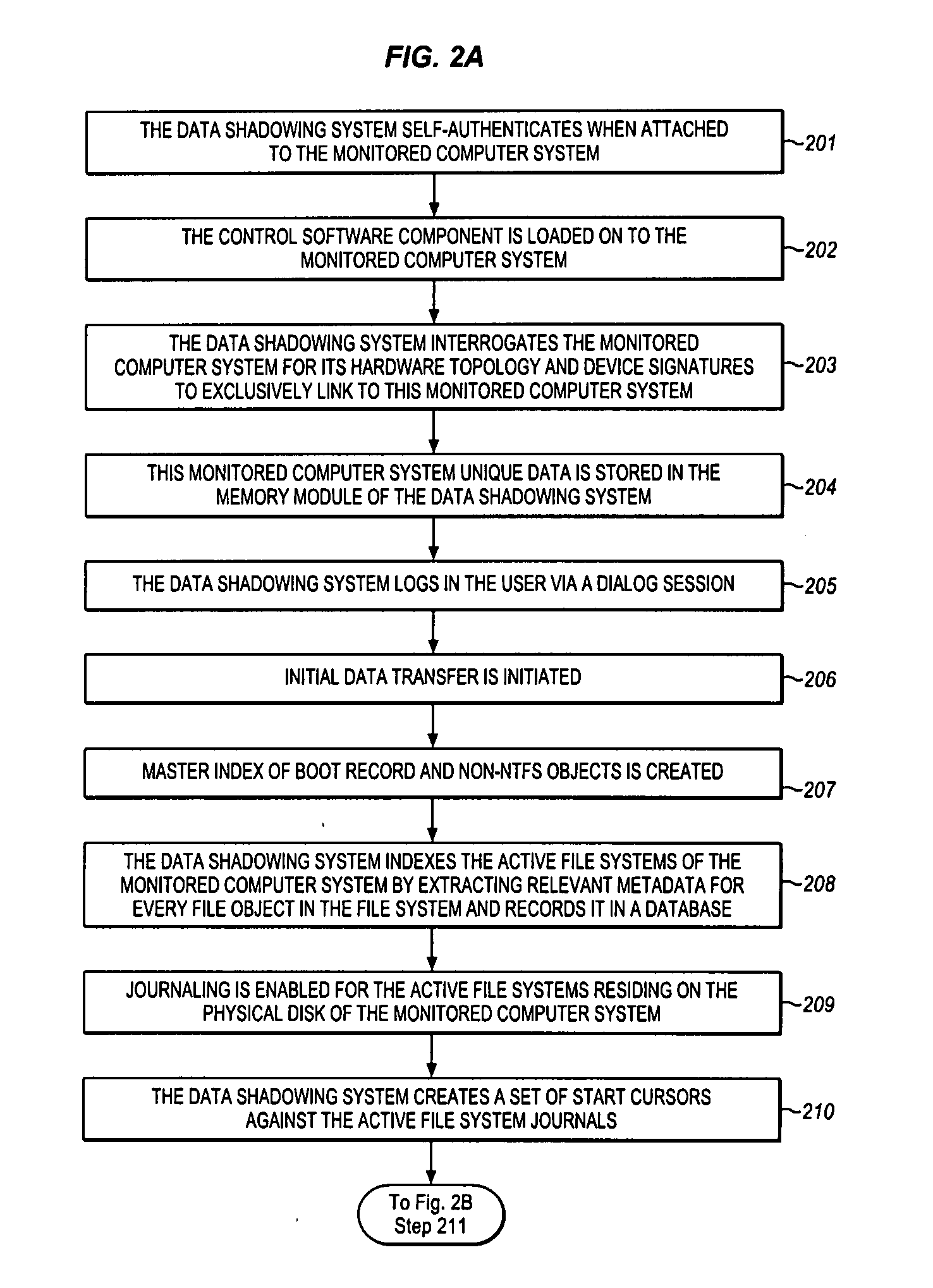
Method used
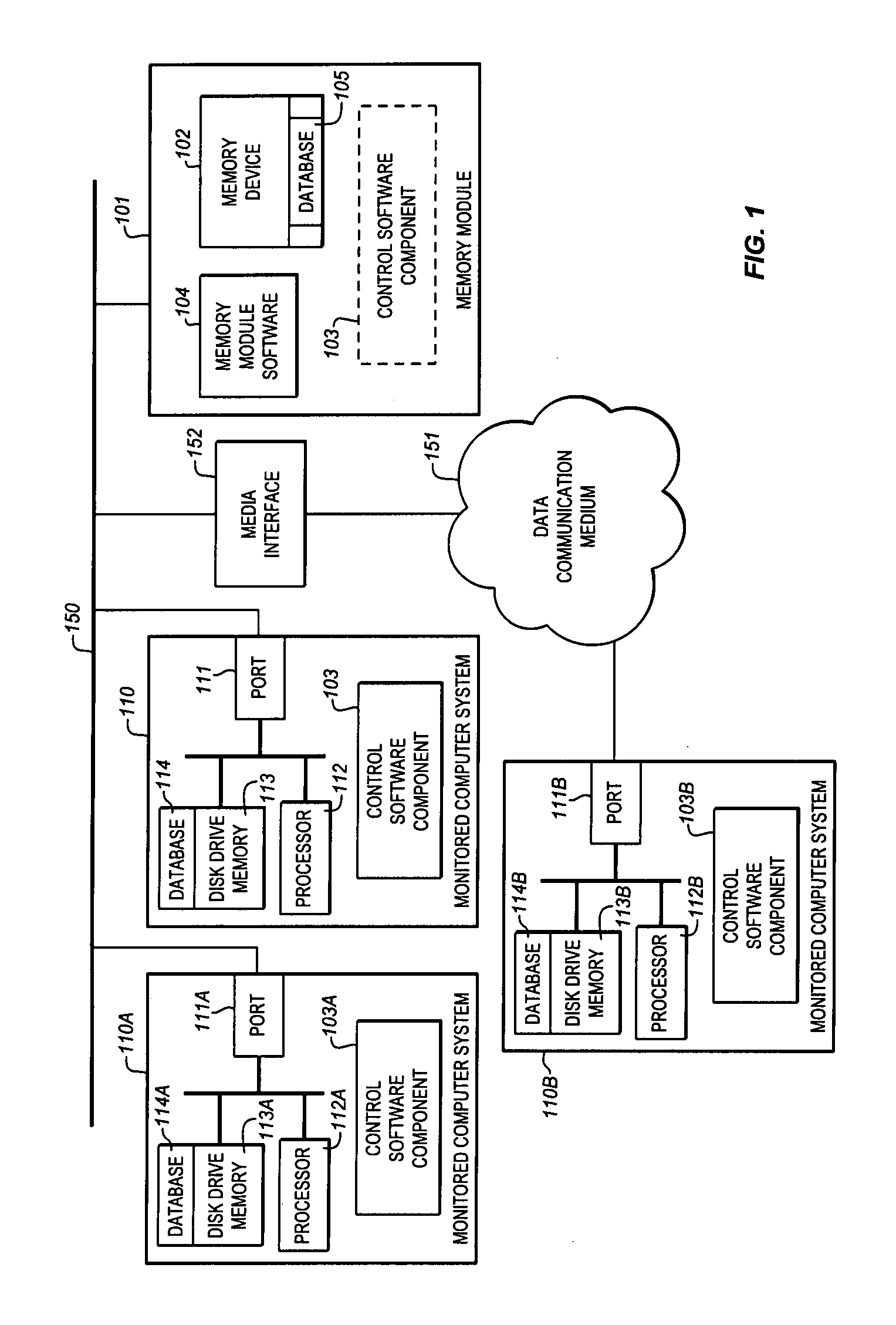
Image
Examples
Embodiment Construction
Definitions
[0028]The following terms as used herein have the following meanings.
[0029]“File system”—the system utilized by the computer operating system to organize, store, and access information contained in the computer system memory.
[0030]“File navigation system”—the textual, hierarchical navigation interface used by the computer operating system to provide a user with an organized manner of storing, identifying, locating, and operating on files for user operations contained in the computer system memory.
[0031]“Change journal”—a computer operating system provided system to identify and track any file changes, creations, deletions, or relocations.
[0032]“Meta file”—an indirect means of storing information about a related file (e.g., file size and creation date for a data file).
[0033]“Page file”—a computer operating system defined and created file which is specific to the present session running on the computer system; the page file represents short-lived data that is not valid or m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com