Compiling executable code into a less-trusted address space
a technology of executable code and address space, which is applied in the direction of memory address/allocation/relocation, multi-programming arrangements, instruments, etc., can solve the problems of application program development complicating various aspects of the above-mentioned security management approach, malicious parties can trick the jit compiler into generating harmful instructions that are executed, etc., to avoid security violations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
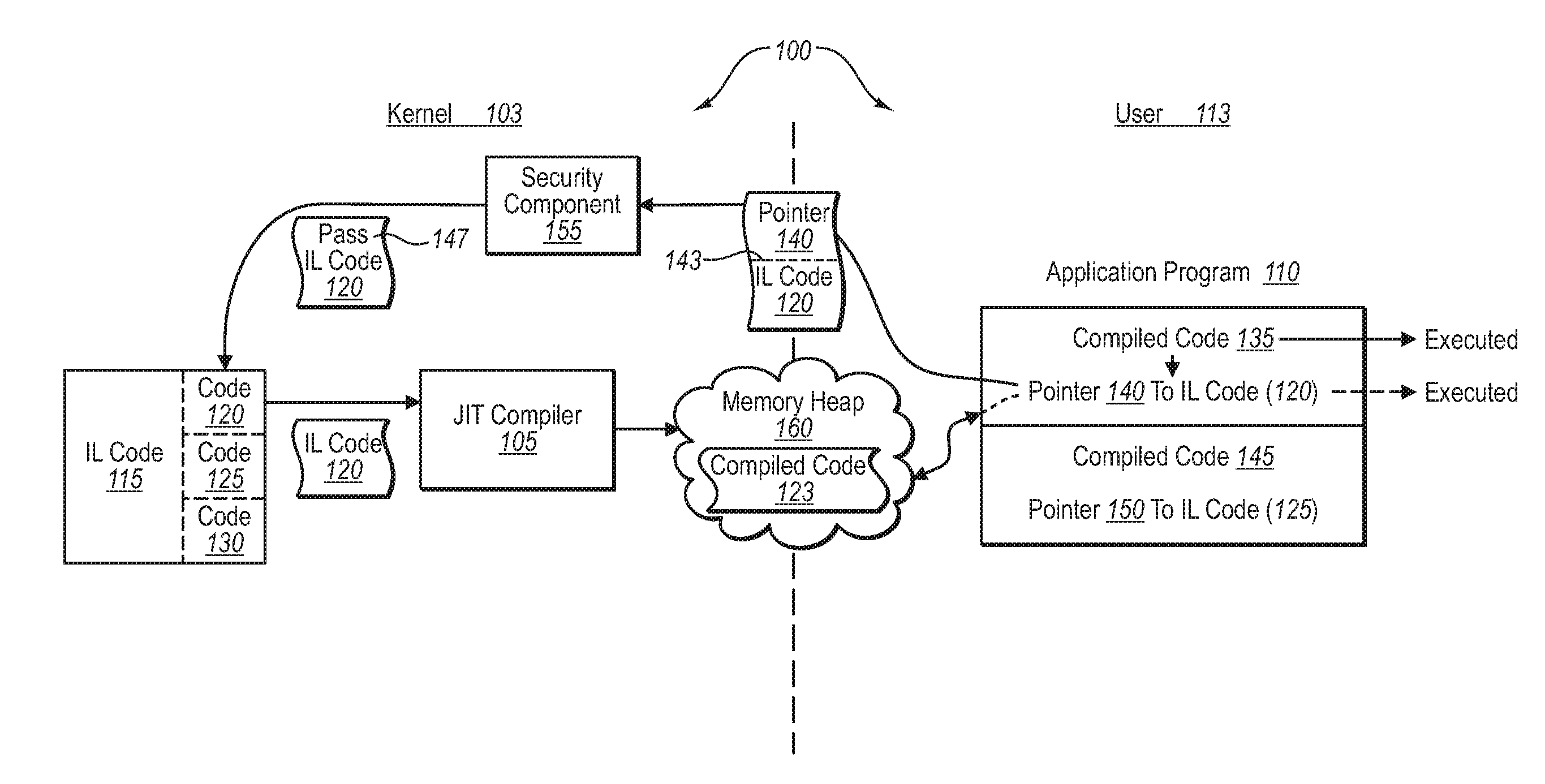
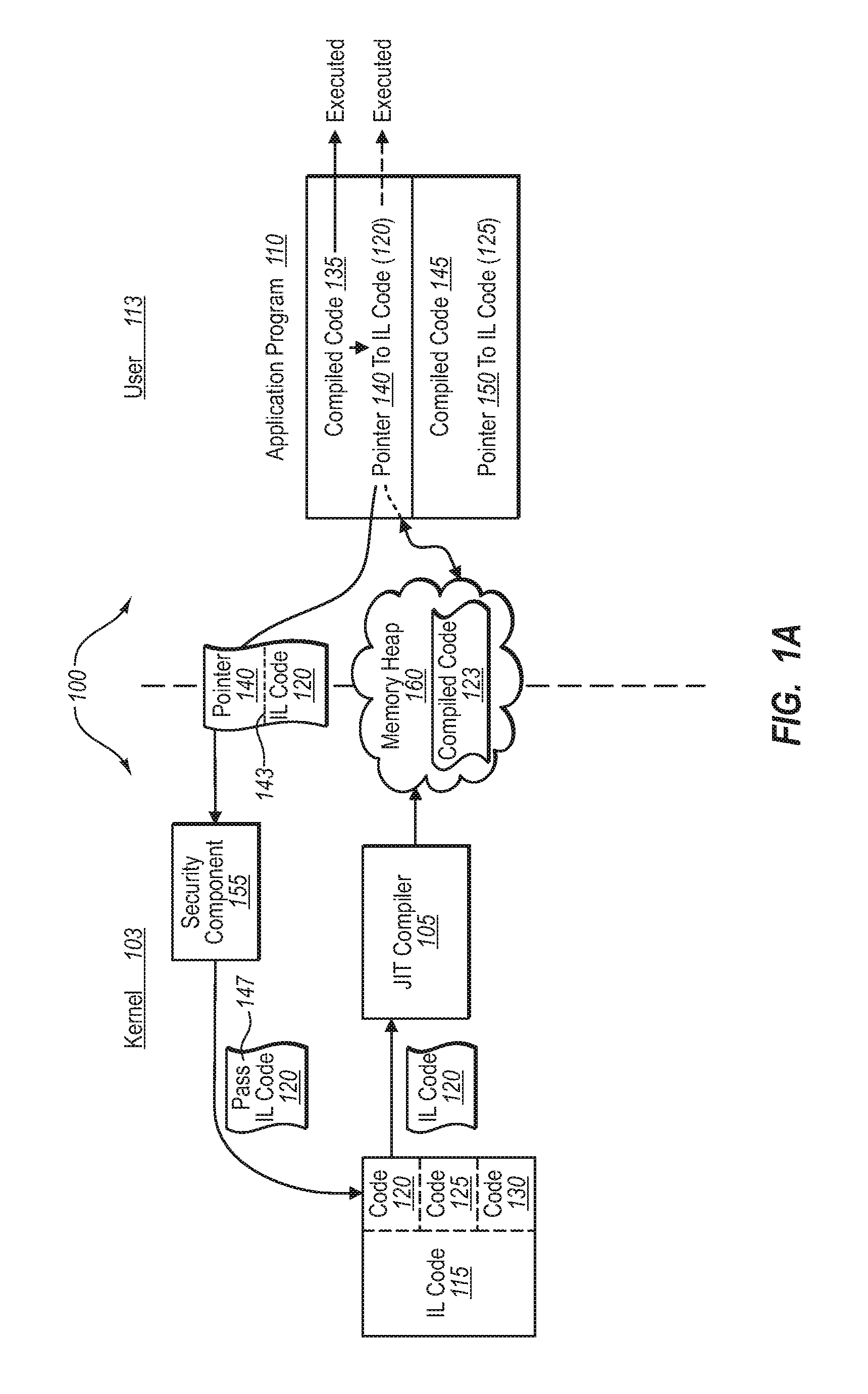
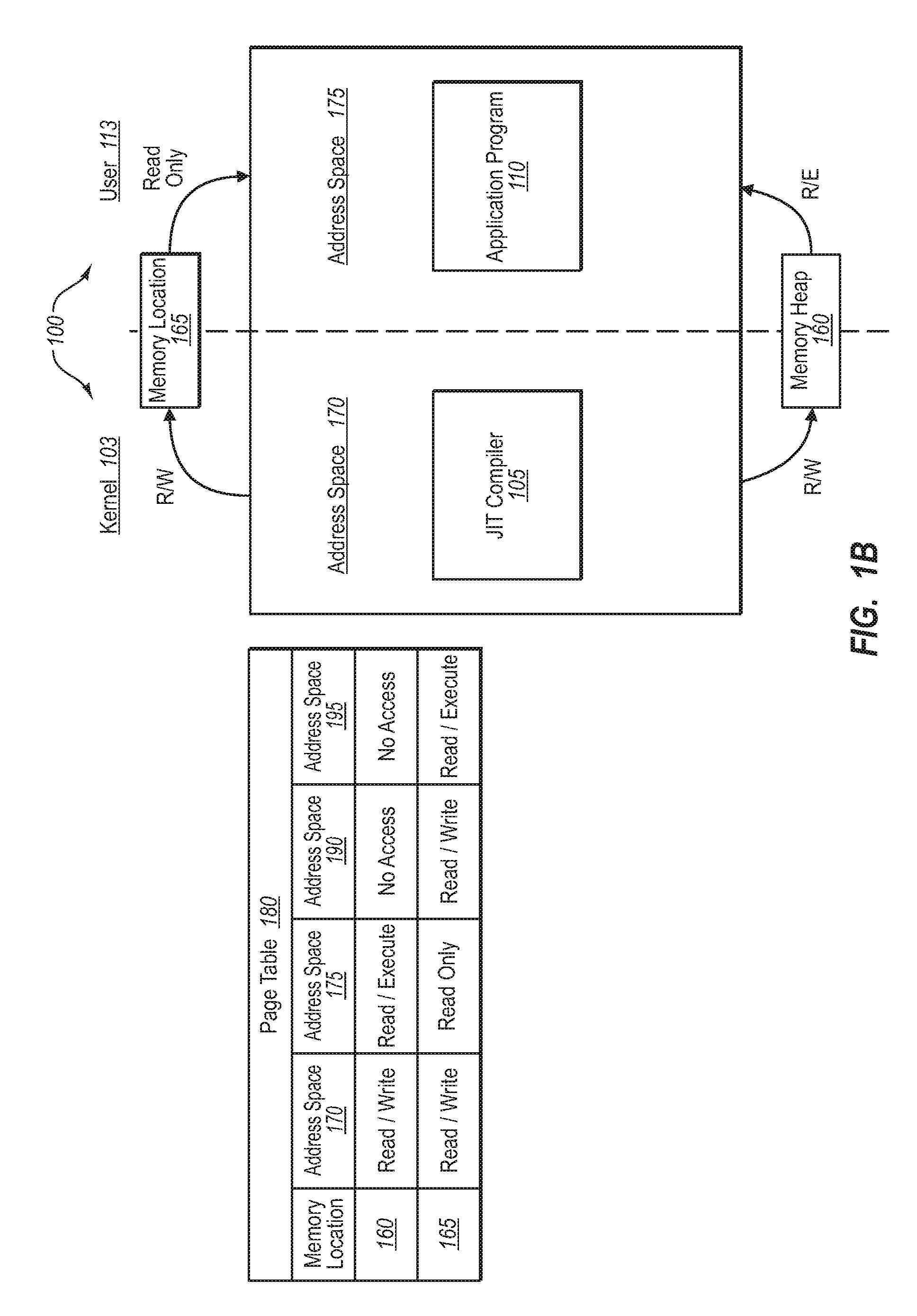
[0021]Implementations of the present invention extend to systems, methods, and computer program products configured to allow for the use of managed code in an operating system, where the managed code may not necessarily conform to any particular code standard. In one implementation, for example, an operating system provides access to a memory location in two different address spaces, and sets the permissions in the address spaces, such that the memory location is accessible with different permissions from the two different address spaces. In one implementation, a JIT compiler operating in one address space passes compiled code into a shared memory heap. Executable program code, in turn, accesses the compiled code from the memory heap, and executes it in the other memory address space.
[0022]As will be understood more fully herein, implementations of the present invention can provide a secure system without necessarily needing to verify that the generated code does not violate the sec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com