Triangulation for k-anonymity in location trajectory data
a technology of location trajectory and triangulation, applied in relational databases, database models, instruments, etc., can solve problems such as unquestionable use of such publishing, unintended consequences, harm to the safety and security of contributors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
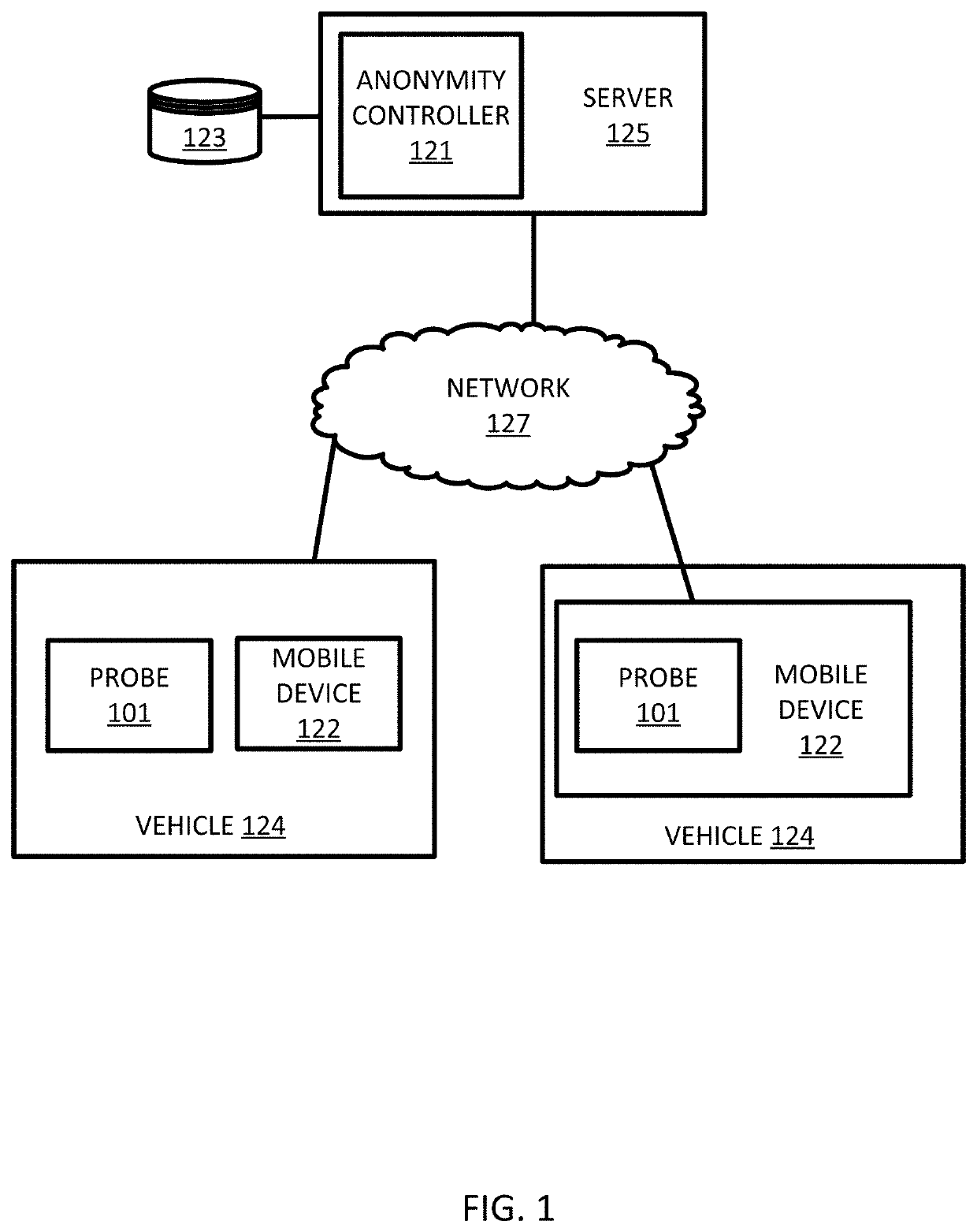
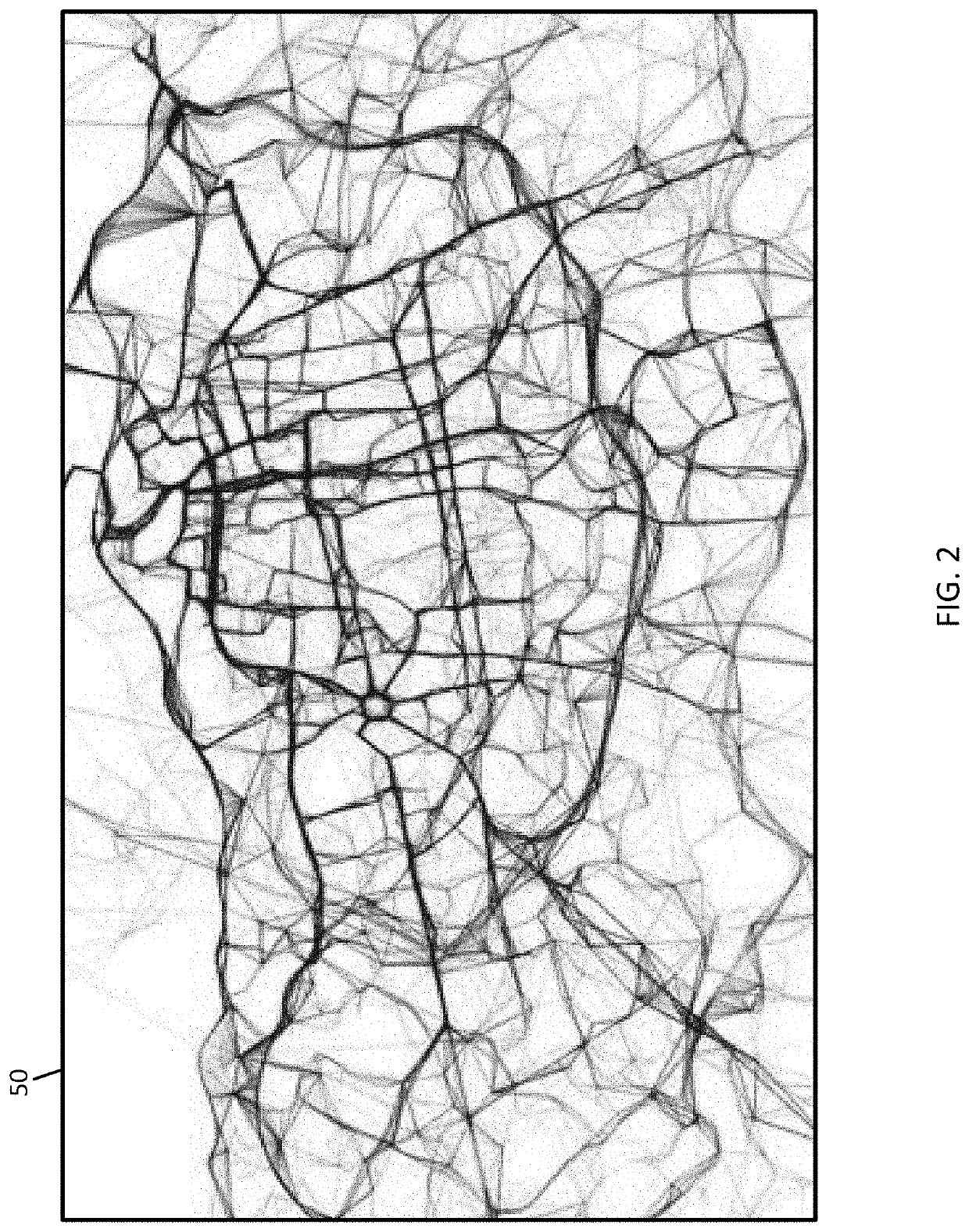
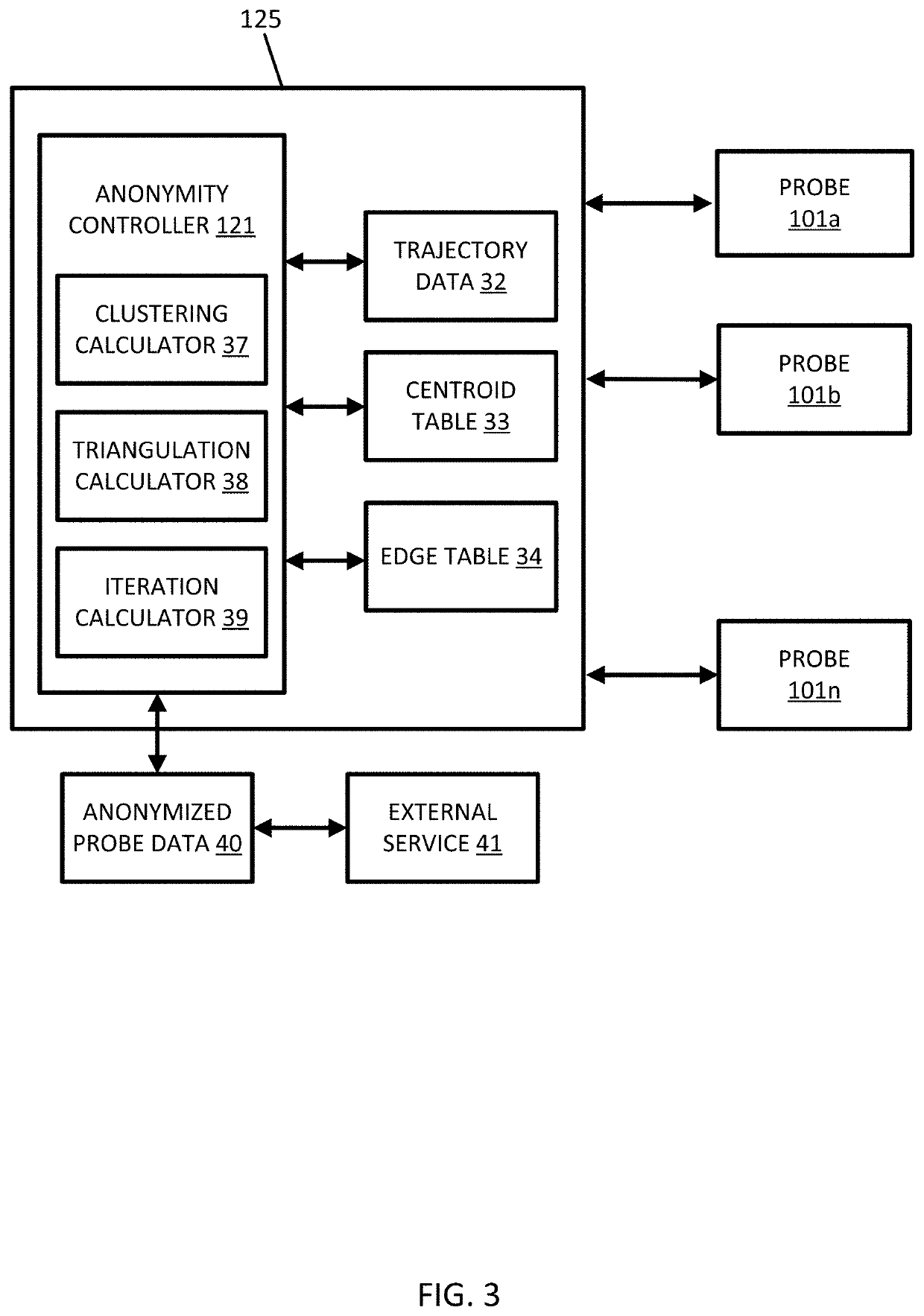
[0063]The anonymity controller 121 is configured to cluster the trajectory data. Throughout this discussion the manipulation of the trajectory data may be done on the point level (e.g., sampled points 51) or on the sequences of sampled points, which are referred to as trajectories. The anonymity controller 121 executes a clustering technique such as K-means clustering with the constraint that each cluster has at least K members. The clustering technique may also include modifications to suit the special requirements of spatial clustering. The modifications may be spatial properties, density variation, or other considerations. The characterization and clustering phase of the first embodiment is not tuned optimally to underlying data and is sensitive to user parameters. The density variation is minimized with minimal user input.
[0064]The K-means clustering, or another type of initial clustering, may include an initial clustering technique. The anonymity controller 121 is configured to...
embodiment 1
[0209]The following example embodiments of the invention are also disclosed:[0210] A method for providing anonymity in geographic data for probe devices in a geographic region for a location-based service, the method comprising:
[0211]receiving trajectory data based on sequences of sensor measurements of the probe devices;
[0212]calculating, by a processor, a plurality of triangles from the trajectory data, wherein each of the plurality of triangles is defined by vertices;
[0213]calculating, by the processor, a similarity score for the vertices based on trajectory data associated with adjacent vertices;
[0214]modifying at least one vertex in response to the similarity score;
[0215]calculating, by the processor, a centrality score for each of the plurality of triangles in response to the at least one vertex;
[0216]assigning geographic locations to the trajectory data according to the centrality score; and
[0217]providing the geographic location to the location-based service.[0218]Embodiment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com