Method for preventing key share attacks
a key share and attack technology, applied in the field of key share attack prevention, can solve the problems of inability to prevent on-line attacks, protocol variants that cannot be considered minor variants of sts, and protocol security attributes that are lacking, so as to minimize an on-line uks attack against a responder
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
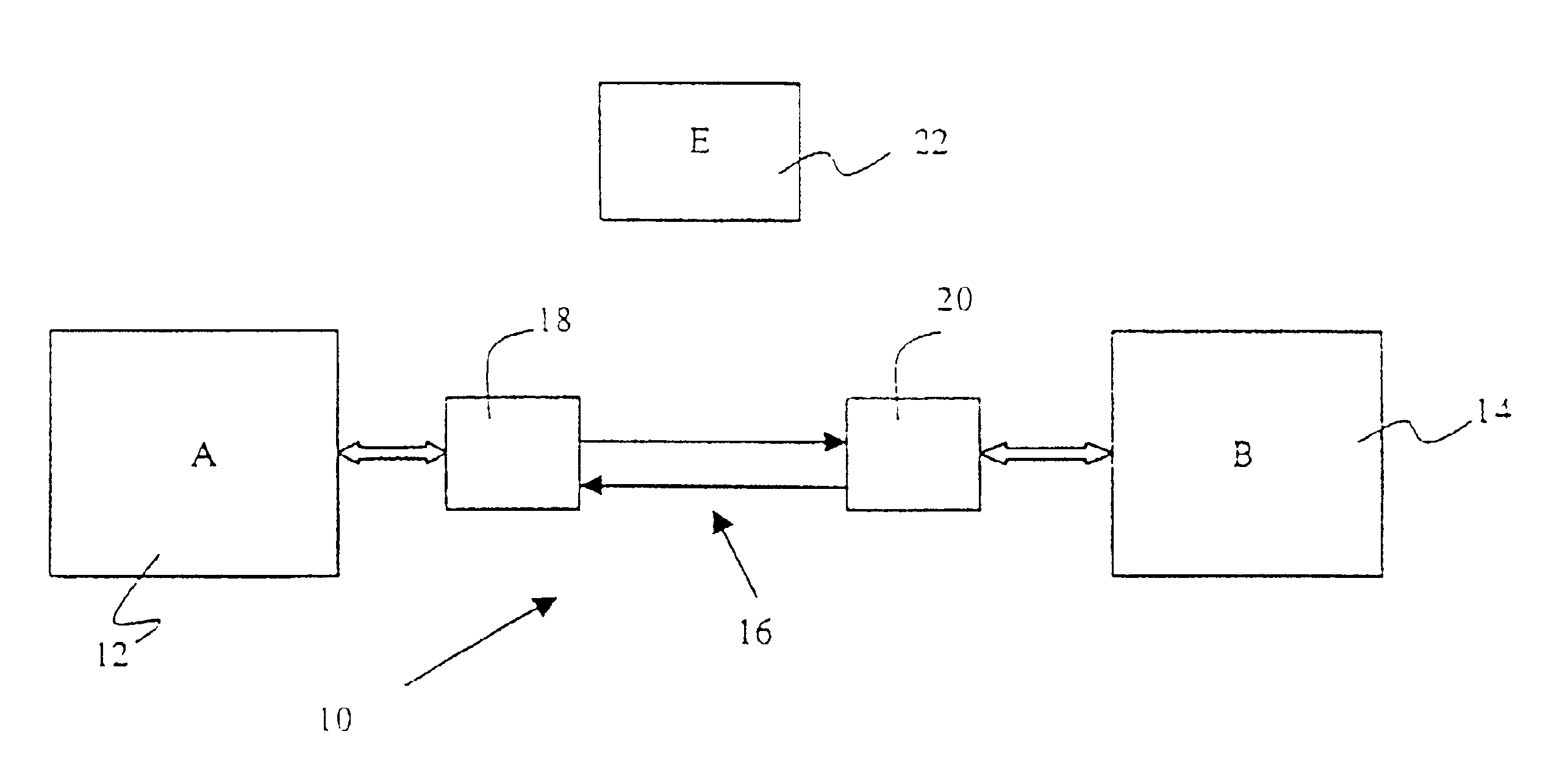
Referring to FIG. 1, an electronic communication system 10 includes a pair of correspondents, A and B, designated as a sender 12 and recipient 14, connected by a communication channel 16. Each of the correspondents 12 and 14 includes an encryption unit 18 and 20 respectively that may process information and prepare it for transmission through the channel 16. A third entity 22 is depicted as the adversary.
In a key establishment / agreement protocol, according to the embodiment of the present invention, the following flow of messages take place between the entities:
Item 1.
(1) A→E A,αrA (2) A←B CertB, αrB,SB(2,B,A,αrB,αrA),MACK(SB(2,B,A,αrB,αrA))(3) A→B CertA, SA(3,A,B,αrA,αrB),MACK(SA(3,A,B,αrA,αrB))
In the original STS-MAC protocol described in the background section and the modification presented above, the agreed key K is used as the MAC key for the purpose of providing explicit key confirmation. A passive adversary now has some information about K, namely the MAC of a known message u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com