Data safety management system
A management system and data security technology, applied in data processing applications, electrical digital data processing, special data processing applications, etc., can solve problems such as damage to security, information leakage, important information leakage, etc., to prevent illegal access to storage media Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
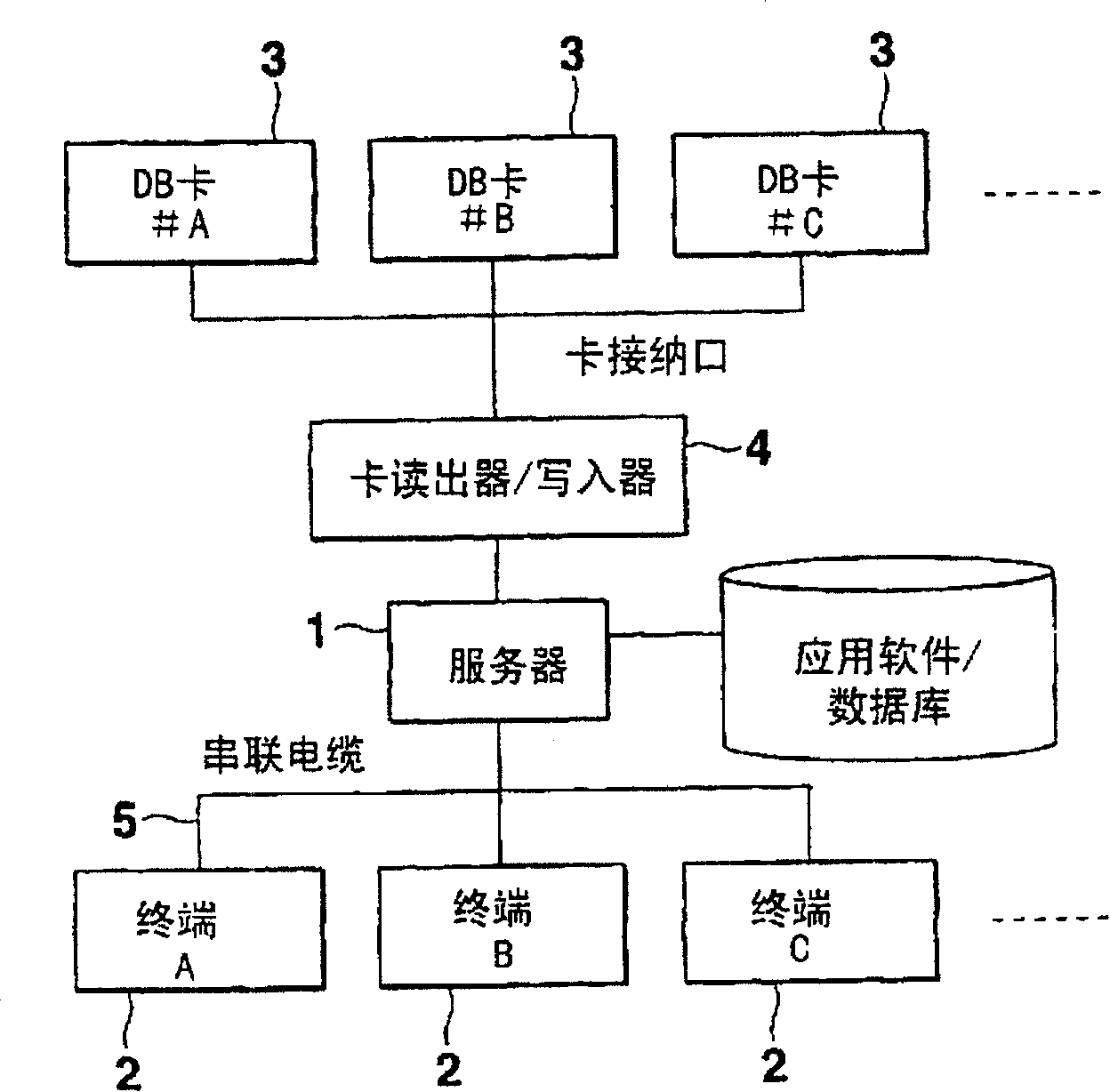
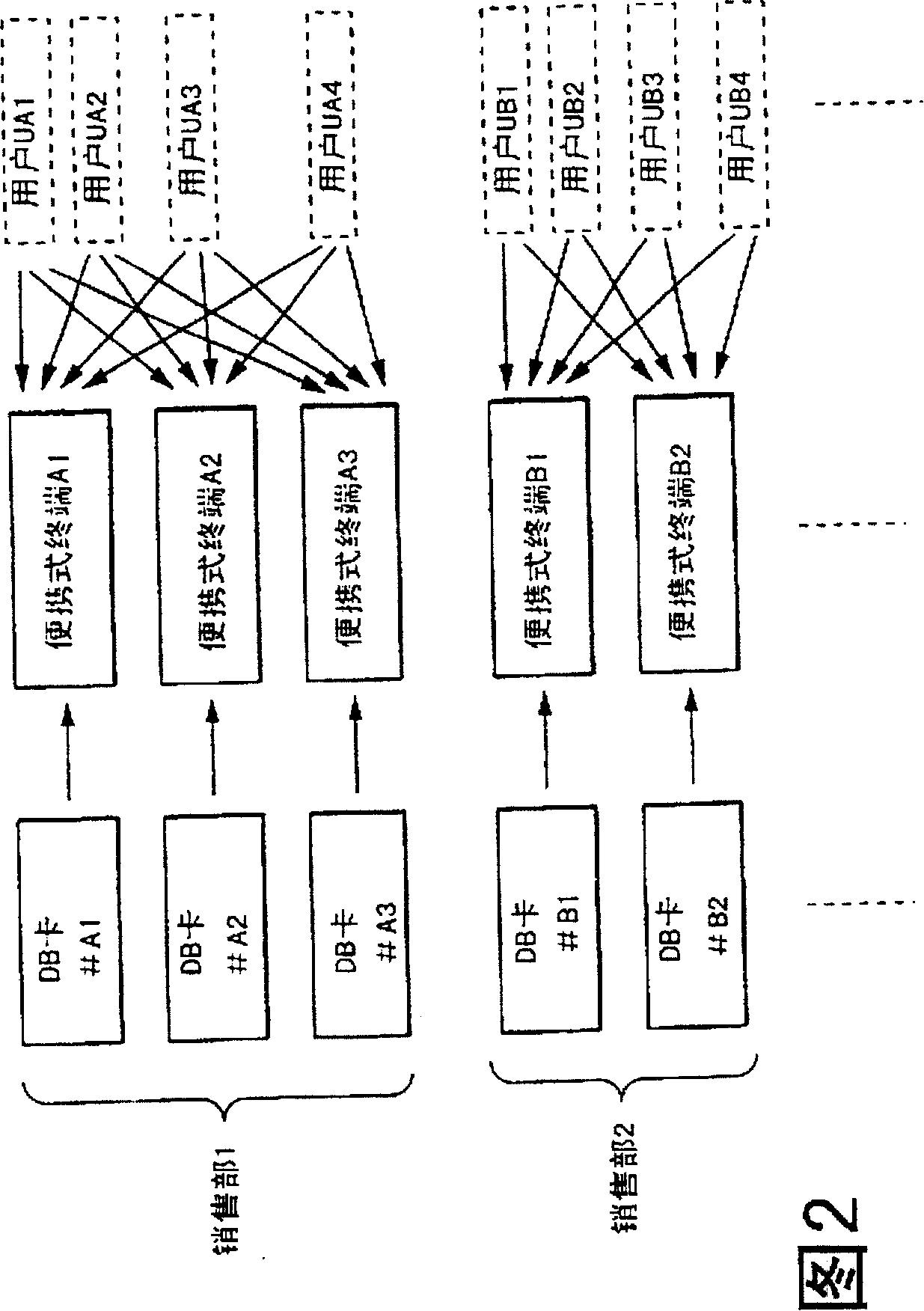
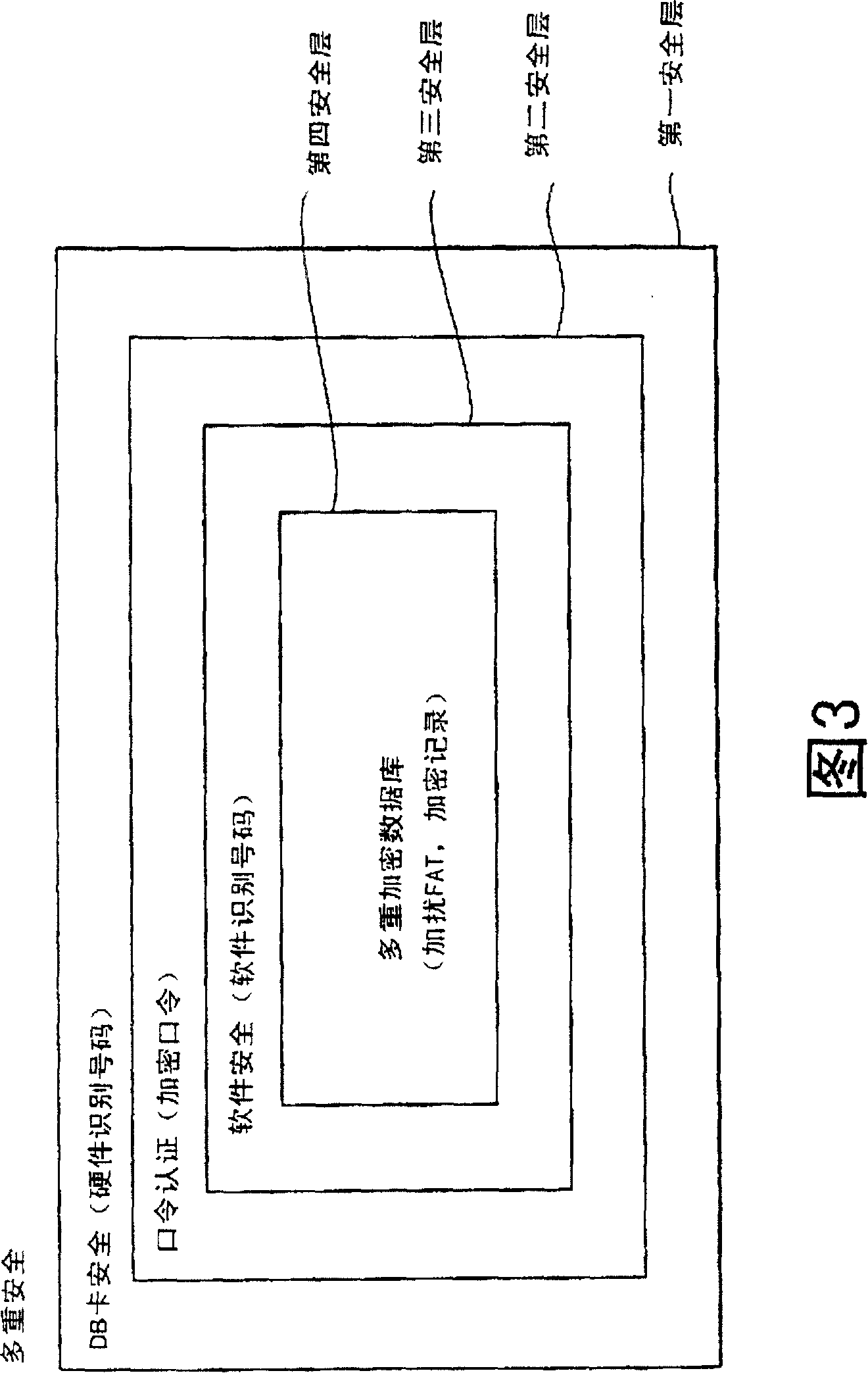
[0050] The following will refer to the attached Picture 1-1 4 illustrates a security management system as a preferred embodiment of the present invention. see figure 1 , the security management system includes: a server 1 such as installed in a company; a plurality of groups of movable or portable agent terminals 2, which are respectively carried by corresponding sellers, and connected in a detachable manner through serial cables 5 on the server 1; and a plurality of sets of portable storage media 3 respectively provided in corresponding portable terminals 2 for use.
[0051] The server 1 provides each group of terminals 2 with the application software / database stored in and managed by the server 1 through a set of corresponding storage media 3 . When server 1 writes database or other data on each storage medium 3 in each group and distributes these storage media to each terminal in this group, server 1 will send each terminal in this group by setting information Correspon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com