Radio mesh re-authentication method based on the WLAN secure standard WAPI
A technology of wireless local area network and wireless mesh network, which is applied in the direction of radio/inductive link selection arrangement, user identity/authority verification, data exchange through path configuration, etc. It can solve the problem of prolonged re-authentication, complex base key list, Low efficiency and other issues, to achieve the effect of fast movement, shortened delay time, and simple implementation process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be described in further detail below in conjunction with the accompanying drawings.
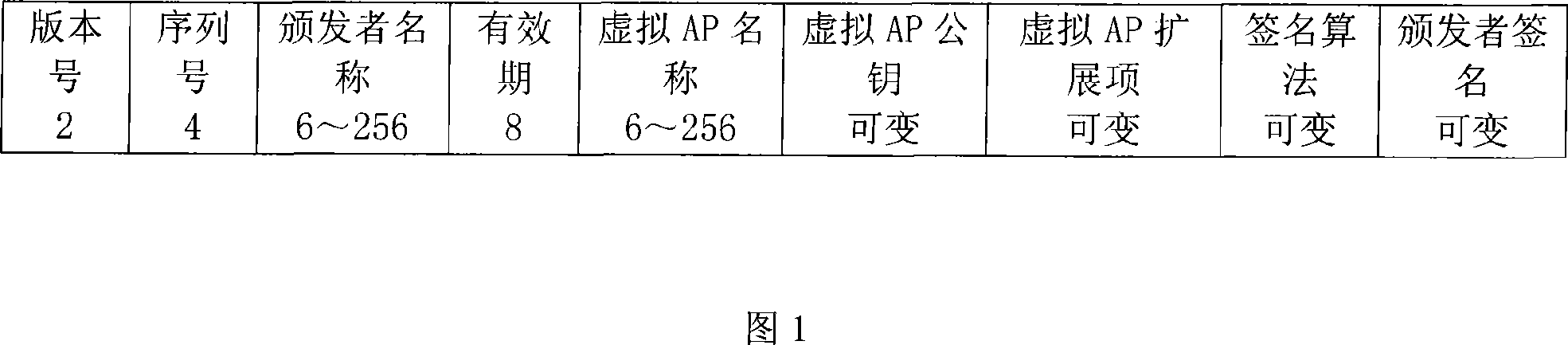
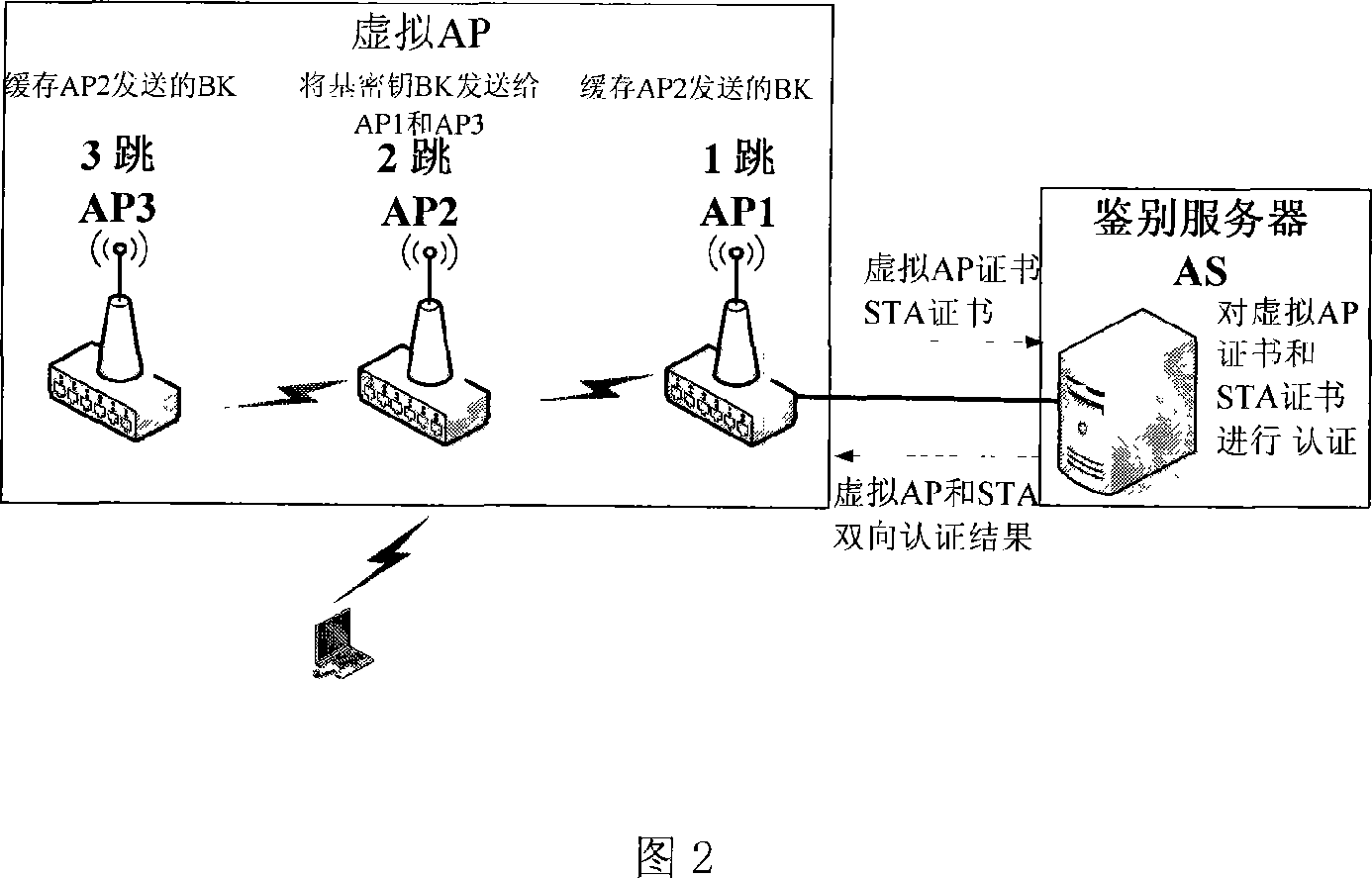
[0027] FIG. 1 is a schematic diagram of a WAPI application structure in a wireless mesh network. Virtualize several adjacent physical APs in the wireless mesh network into the same virtual AP, and install the same virtual AP certificate in these physical APs (distribution, management and installation of certificates are not within the scope of the present invention). When a STA connects to any physical AP in the network, it is equivalent to connecting to this virtual AP, and the connected physical AP realizes the function of a virtual AP.
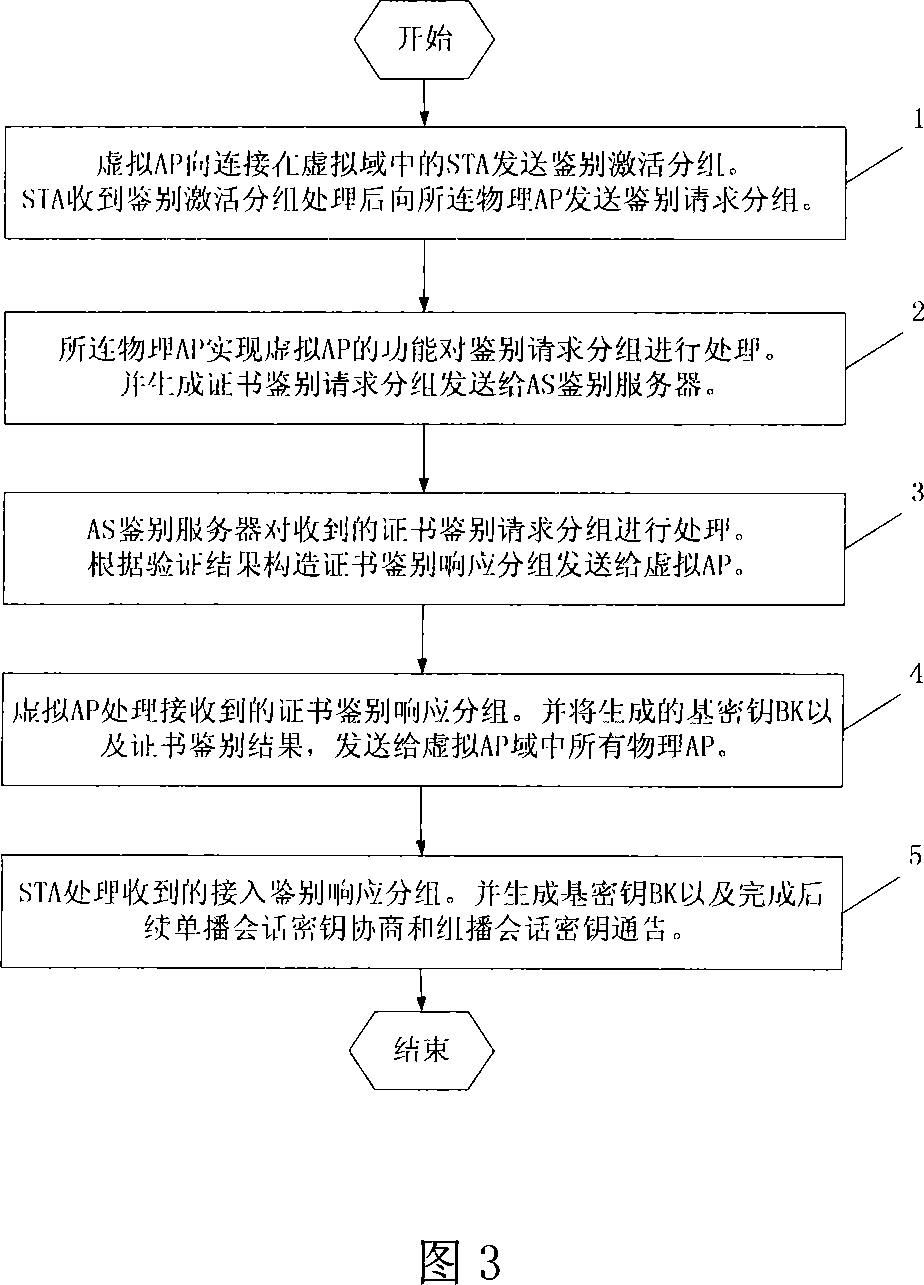
[0028] Fig. 2 is a flow chart of authentication for a STA connecting to a wireless mesh network for the first time. When the STA connects to the wireless mesh network for the first time, the WAPI authentication process based on the virtual AP is as follows:
[0029] Step 1: The virtual AP sends an authentication activati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com