Secondary door access system adopting biological character identification technology and control method
A biometric identification and biometric technology, which is applied in the field of access control and biometric identification, can solve problems such as unsolved problems, and achieve the effect of increasing the time for handling police, flexible and simple operation, and ensuring safety and legality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
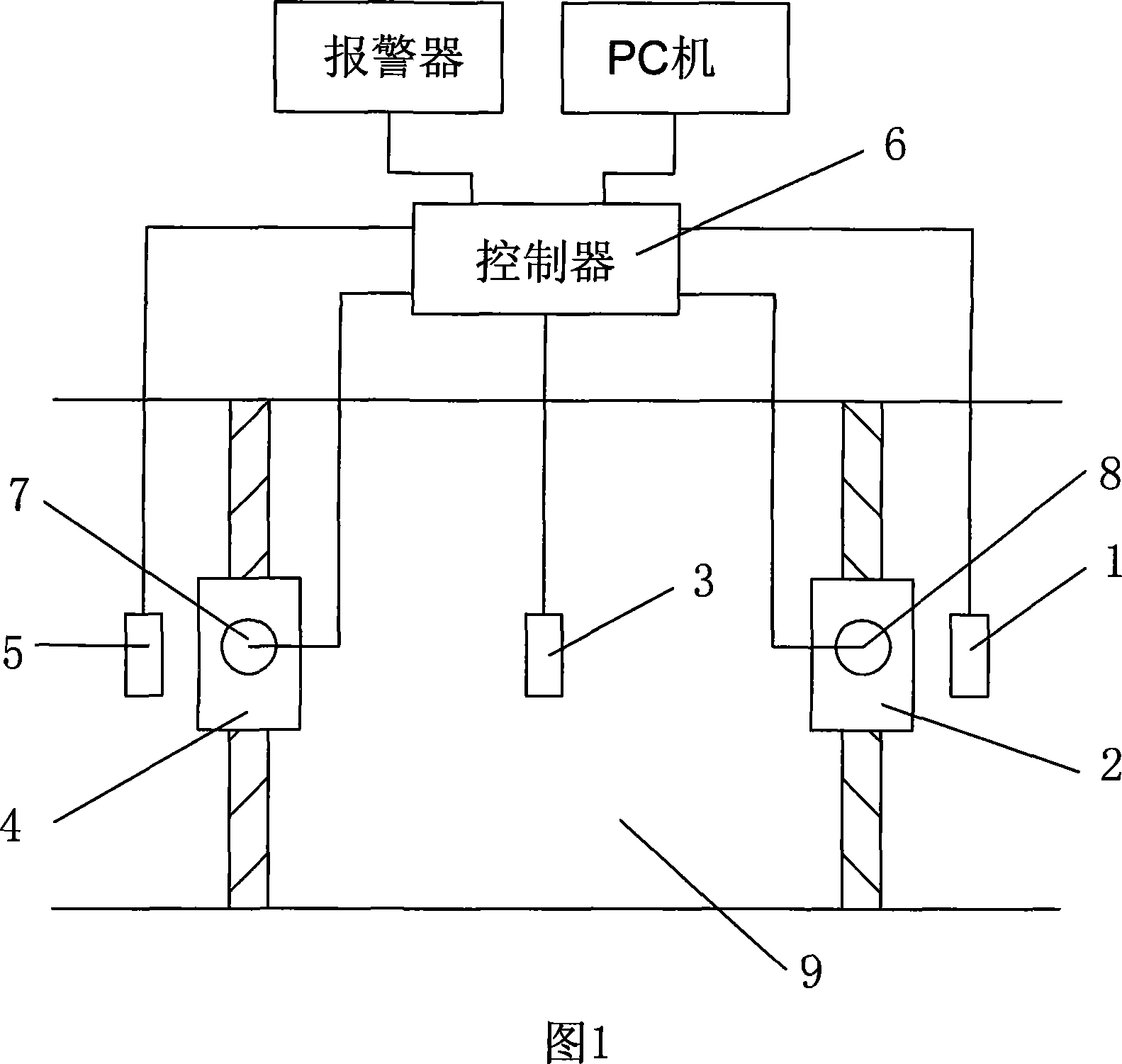
[0057] Embodiment 1: In this embodiment, fingerprints are used as biometric features. The system includes fingerprint access control equipment, a controller, an electric lock, a switch box, a fingerprint information registration terminal, and an access control system server, as shown in Figures 4 and 5:
[0058] The fingerprint access control device is mainly used to complete the collection, transmission and comparison of fingerprint data, and send the door opening application to the controller for the authorized fingerprint. The device further includes: a fingerprint sensor, a fingerprint processing module, a data storage unit, a main processing unit, a keyboard, and an LCD. in:
[0059] 1) Fingerprint sensor for detecting and collecting fingerprints;
[0060] 2) fingerprint processing module, used for processing, searching and comparing the collected fingerprint data;
[0061] 3) data storage unit, used to store user information, feature data, user belonging group informat...
Embodiment 2
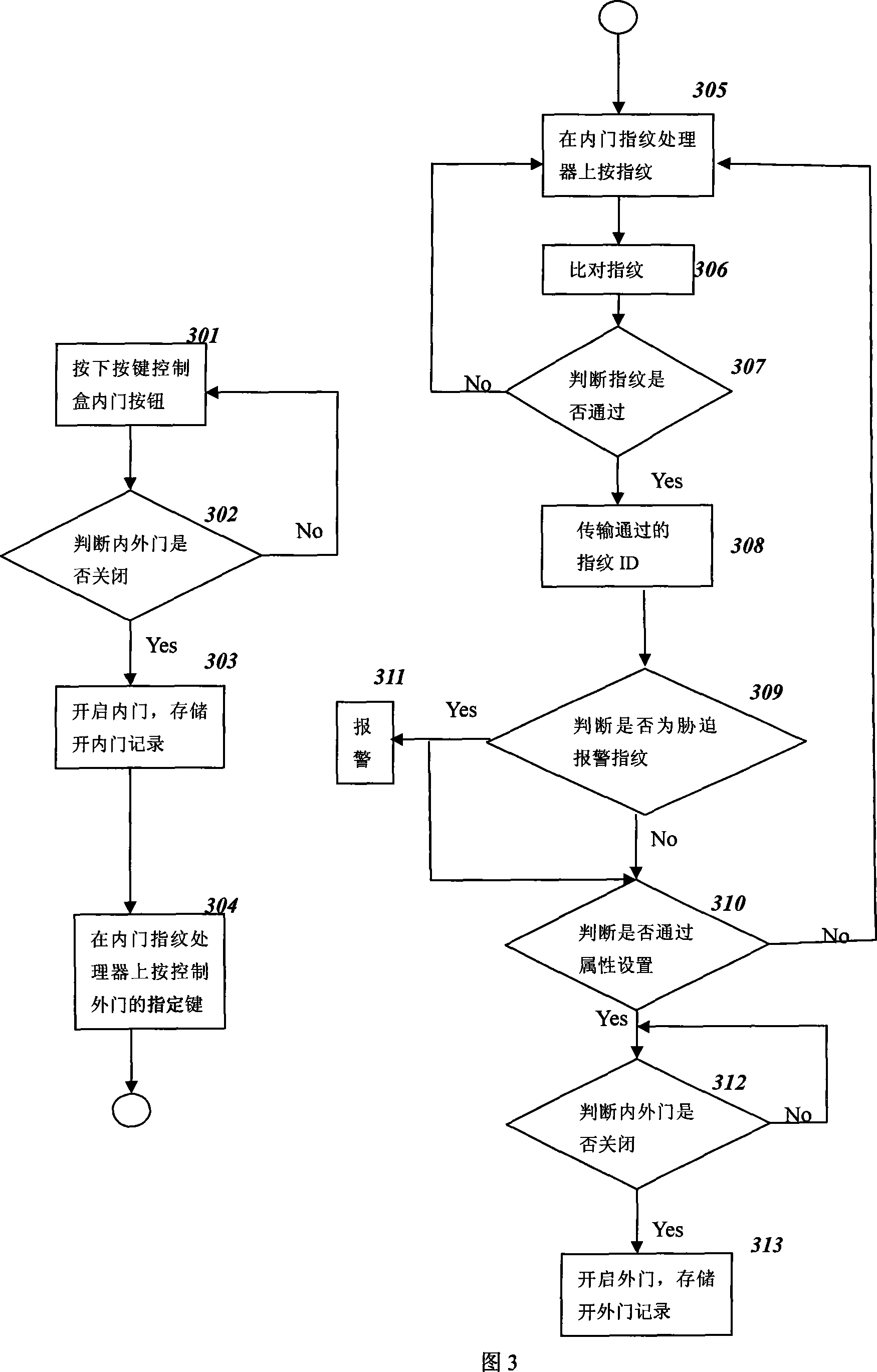
[0070] Embodiment 2: When the staff wants to go out from the inside of the business point through the second door, they can pass in the following way, as shown in Figure 3:
[0071] As in step 301, the staff activates the button on the switch box 5, and then judges whether the inner door 4 and the outer door 2 are closed, as in step 302. After receiving the door closing report, the controller 6 sends an electrical signal to open the inner door 4 to the electric control lock 7 of the inner door, opens the inner door 4, and stores the record of the inner door 9, as in step 303. The staff walks into the isolation area 9 of the second door and closes the inner door 4 . After entering the isolation area, the staff performs fingerprint verification operation on the fingerprint access control device 3 in the isolation area. First press the specified key of opening the outer door 2 such as step 304, send the operation report of the outer door 2, and then perform fingerprint verificat...
Embodiment 3
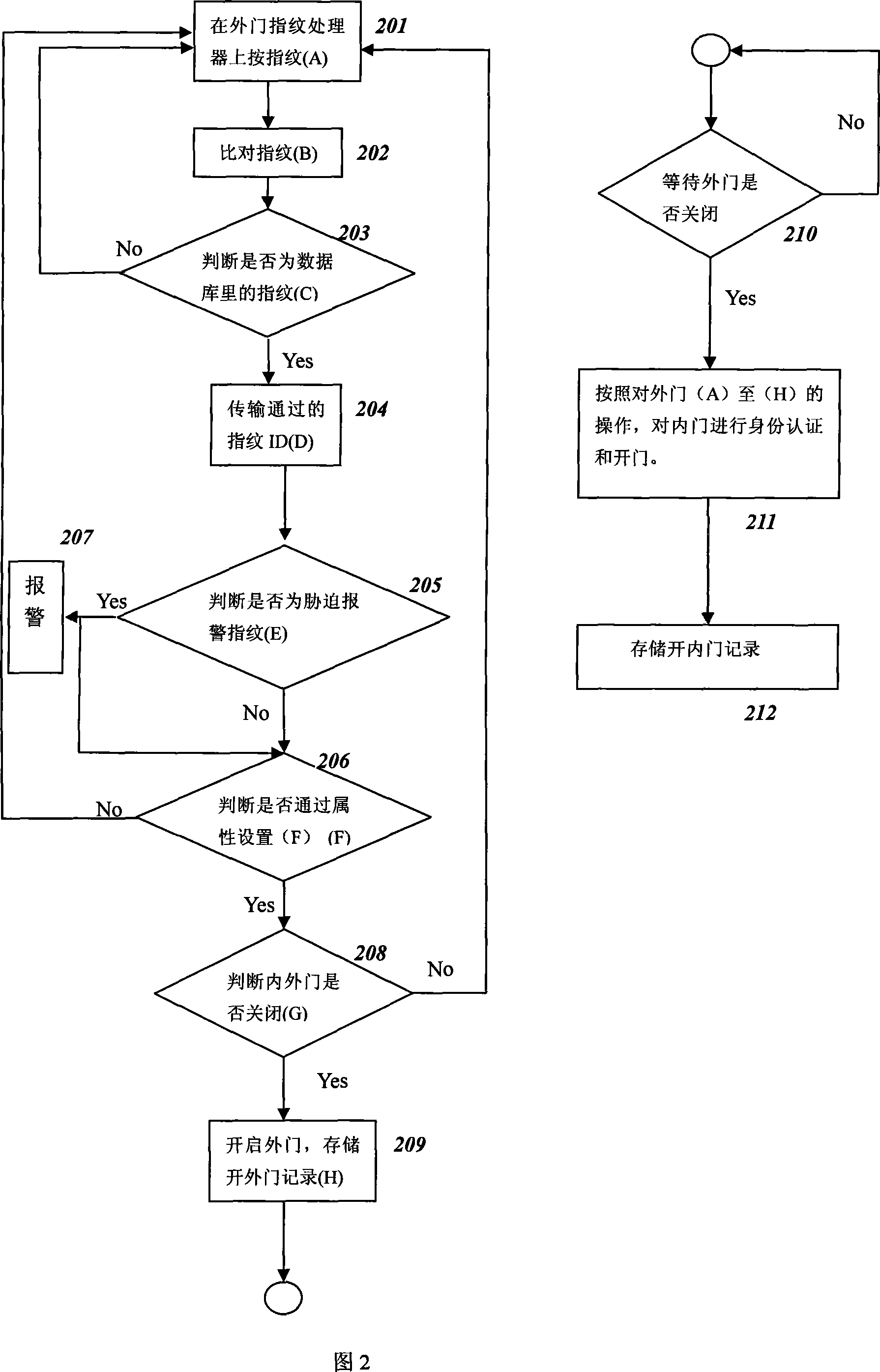
[0072] Embodiment 3: When the staff enters from the outside of the business point through the second door, a gangster raid occurs temporarily. Facing the threat of gangsters, the staff operates as follows, as shown in Figure 2,
[0073] The staff directly presses the threat alarm fingerprint, as in step 201. The fingerprint access control device detects and receives fingerprint information, and extracts and compares the fingerprint information, such as steps 201 to 205. After the duress alarm fingerprint is verified, an alarm signal is sent to the controller 4 at the same time, as in step 207, the controller 4 directly outputs an alarm after receiving the signal. While performing step 207, continue to interrupt the door opening application, and detect whether the inner door 4 and the outer door 2 are currently closed, as in step 208. After satisfying the condition of closing at the same time, the controller 4 outputs an electric signal to open the outer door 2 to the electri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com