Authentication system
An authentication system and object technology, applied in the field of authentication systems, can solve the problem that the authentication execution device cannot obtain distance information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 Embodiment approach
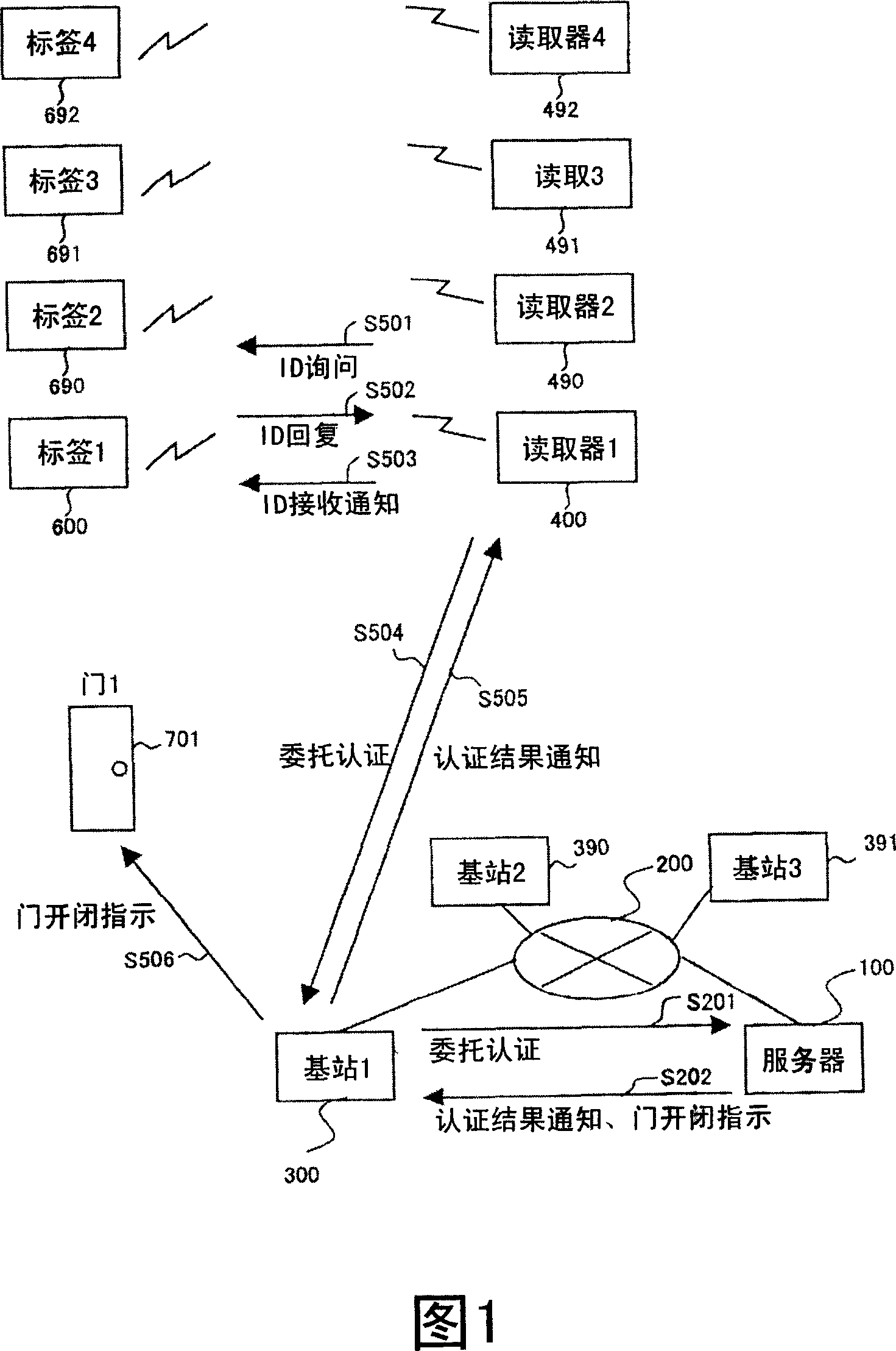
[0059] FIG. 1 is a block diagram showing a configuration example of an authentication system according to a first embodiment of the present invention.
[0060] The authentication system of the first embodiment includes a server 100 , a network 200 , a base station 300 , an authentication execution device (reader) 400 , an authentication target device (tag) 600 , and a control target (gate) 701 . Furthermore, there is no limit to the number of base stations, readers, tags and gates, there may be more than one. Therefore, in the structural example shown in FIG. 1 , in addition to the base station 300, there are base stations 390 and 391; in addition to the reader 400, there are also readers 490, 491 and 492; Labels 690, 691 and 692.
[0061] The structure of the base station 300 and other base stations 390 and 391 may be the same. The structure of reader 400 and other readers 490, 491 and 492 may be the same. In addition, the structures of the tag 600 and the other tags 690, ...
Embodiment approach 1
[0136] In addition, it is possible to perform distance measurement with high accuracy compared with the conventional method using GPS. According to Embodiment 1 of the present invention, an accuracy of tens of centimeters can be realized compared to the accuracy of several meters of GPS. In addition, GPS is difficult to use indoors where radio waves from satellites cannot be received, but the first embodiment of the present invention can be easily used indoors.
[0137] In addition, in the first embodiment, unlike the conventional technology using an acceleration sensor, initial setting is not required.
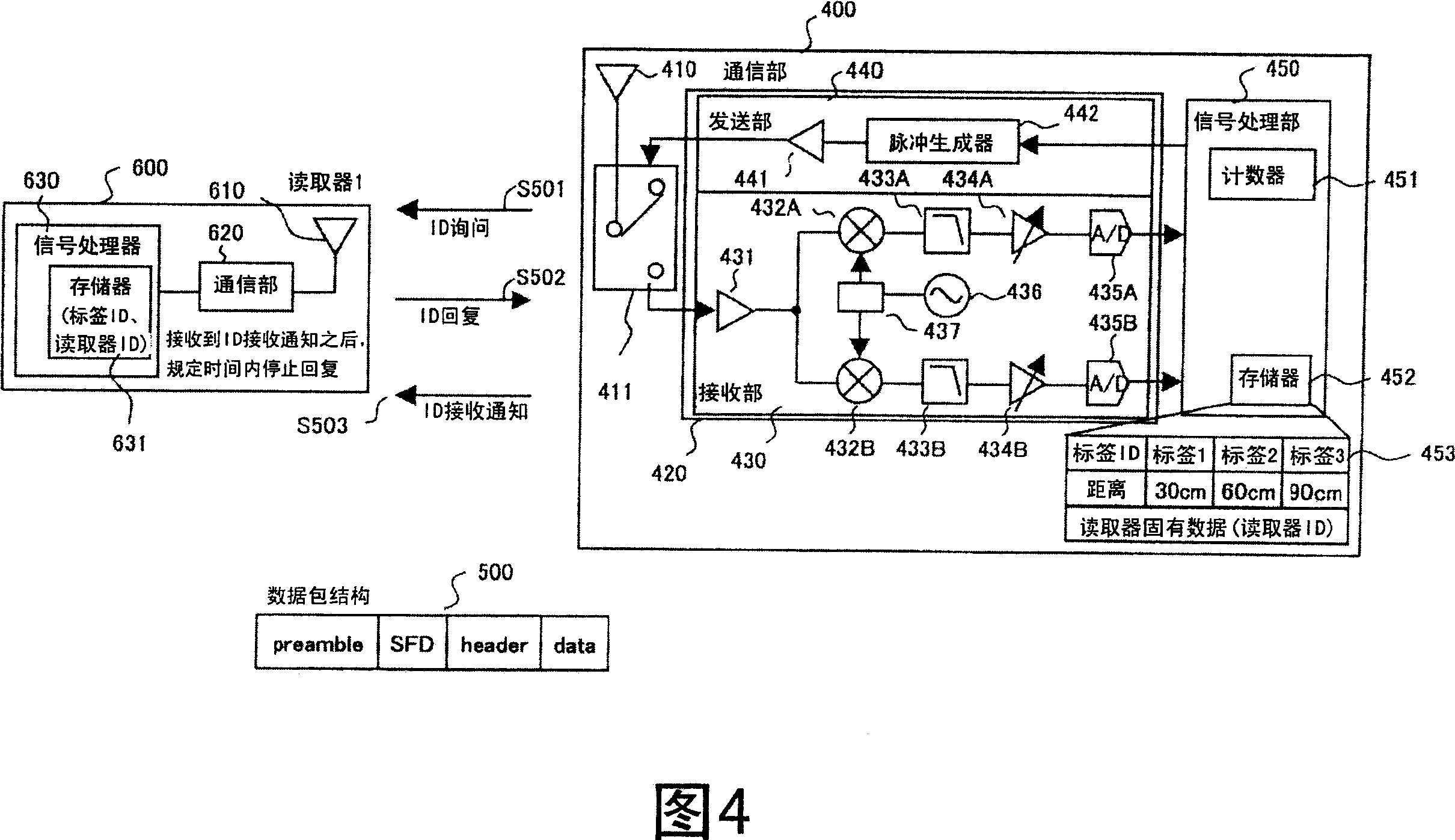
[0138] Furthermore, in the existing method of ranging by a tag, at least 2 communications are required between the tag and the reader. In contrast, in the first embodiment, at least one communication between the tag and the reader is sufficient.
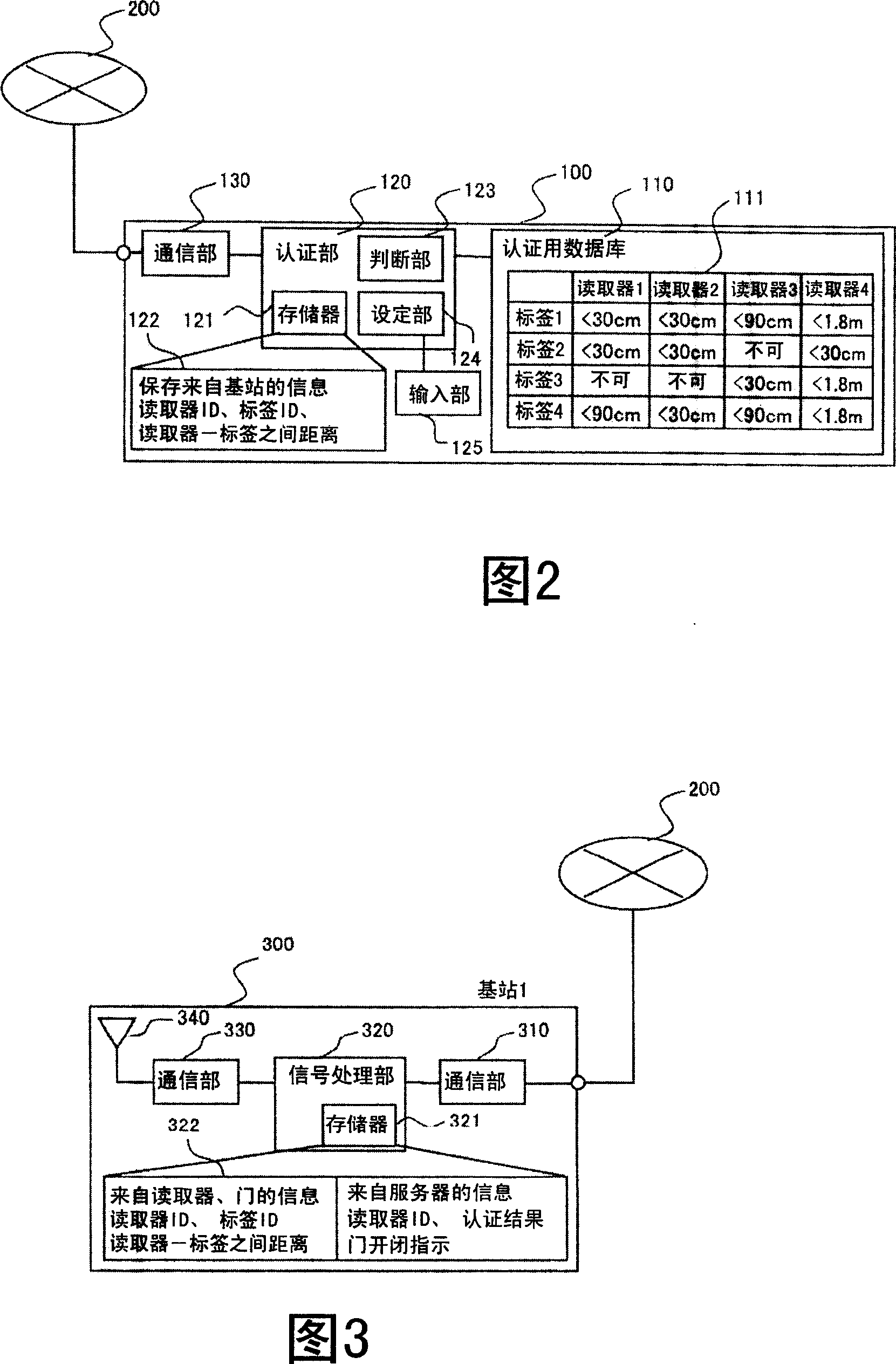
[0139] Moreover, when the authentication data 111 is set appropriately, when the tag 600 tries to unlock the door 701, it is pos...
no. 2 Embodiment approach
[0143] Next, a second embodiment of the present invention will be described. In the first embodiment described above, the distance between the tag and the reader was used as the authentication condition, but in the second embodiment, the authentication condition also includes the direction in which the tag exists.
[0144] The authentication system of the second embodiment includes a server 100 , a network 200 , a base station 300 , an authentication execution device (reader) 400 , an authentication target device (tag) 600 , and a control target (gate) 701 . In the second embodiment, the configurations of the server 100, the base station 30, and the reader 400 are different from those of the first embodiment described above. In addition, the same code|symbol is attached|subjected to the same structure as said 1st Embodiment, and description is abbreviate|omitted.
[0145] The server 100 is connected to the base station 300 through the network 200 . The base station 300 is co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com