Special processor software encryption and decryption method
An encryption method and processor technology, which are applied in the fields of electrical digital data processing, instruments, program/content distribution protection, etc., can solve problems such as inconvenience and impracticality, and achieve the effect of simple function, smart structure, and difficult to break.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
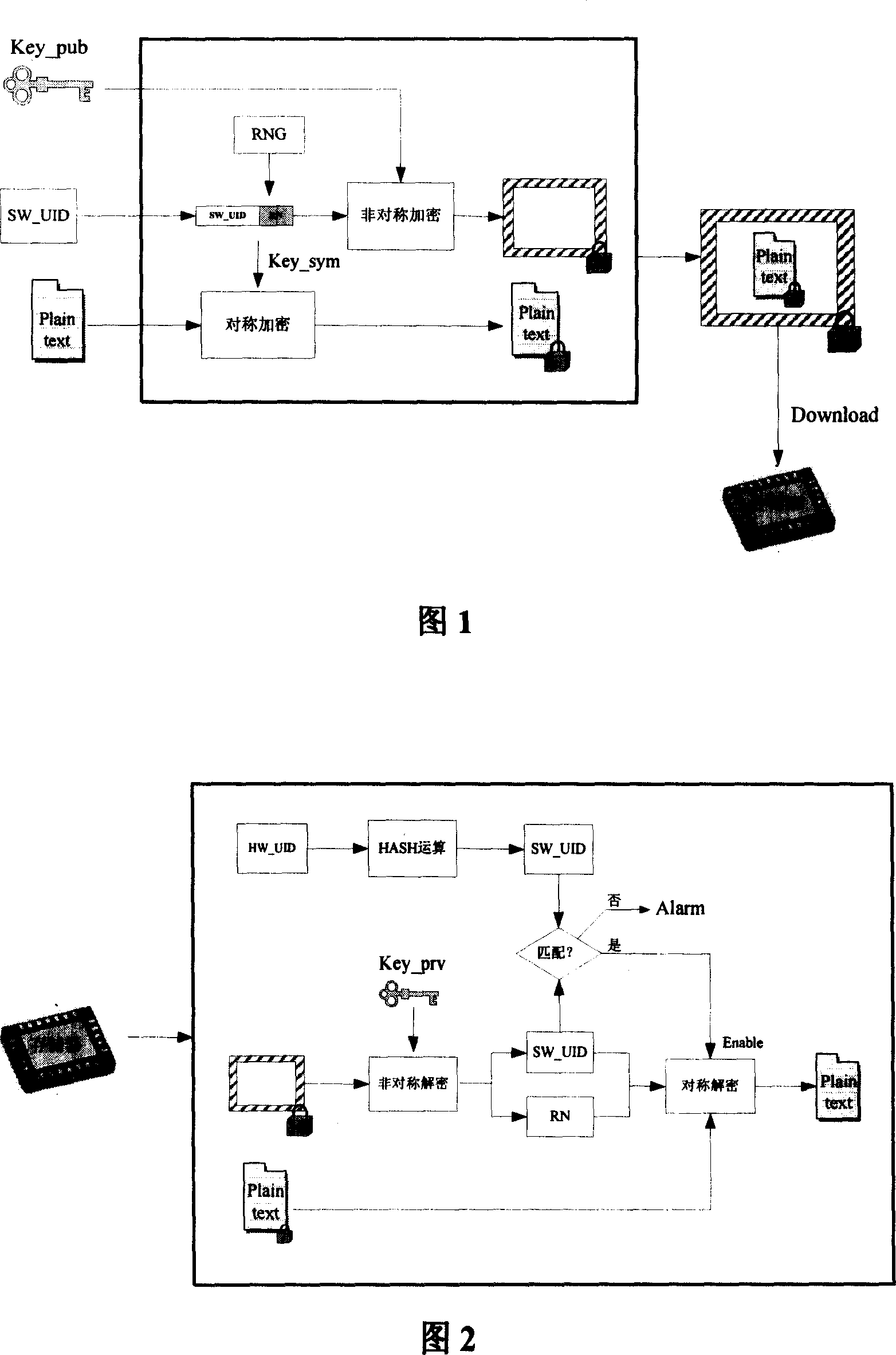
[0034] This embodiment provides an encryption and decryption method of special processor software. First, there is a unique serial number HW_UID that represents the identity of the chip stored in the chip of the dedicated processor. The length of the serial number is determined by the manufacturer itself, but it must not be repeated. The following will introduce in detail how to use this unique serial number to realize the encryption and decryption process of the special processor software from two aspects of encryption and decryption.
[0035] In this example, the implementation process of the encryption terminal is shown in Figure 1. Among them: Key_pub represents the public key, which is used for asymmetric encryption; Key_sym represents the symmetric key, which is used for symmetric encryption; Plain text represents the plaintext of the software to be encrypted; SW_UID represents the unique serial number of the software, which is HW_UID through the hash function Obtained ...
Embodiment 2
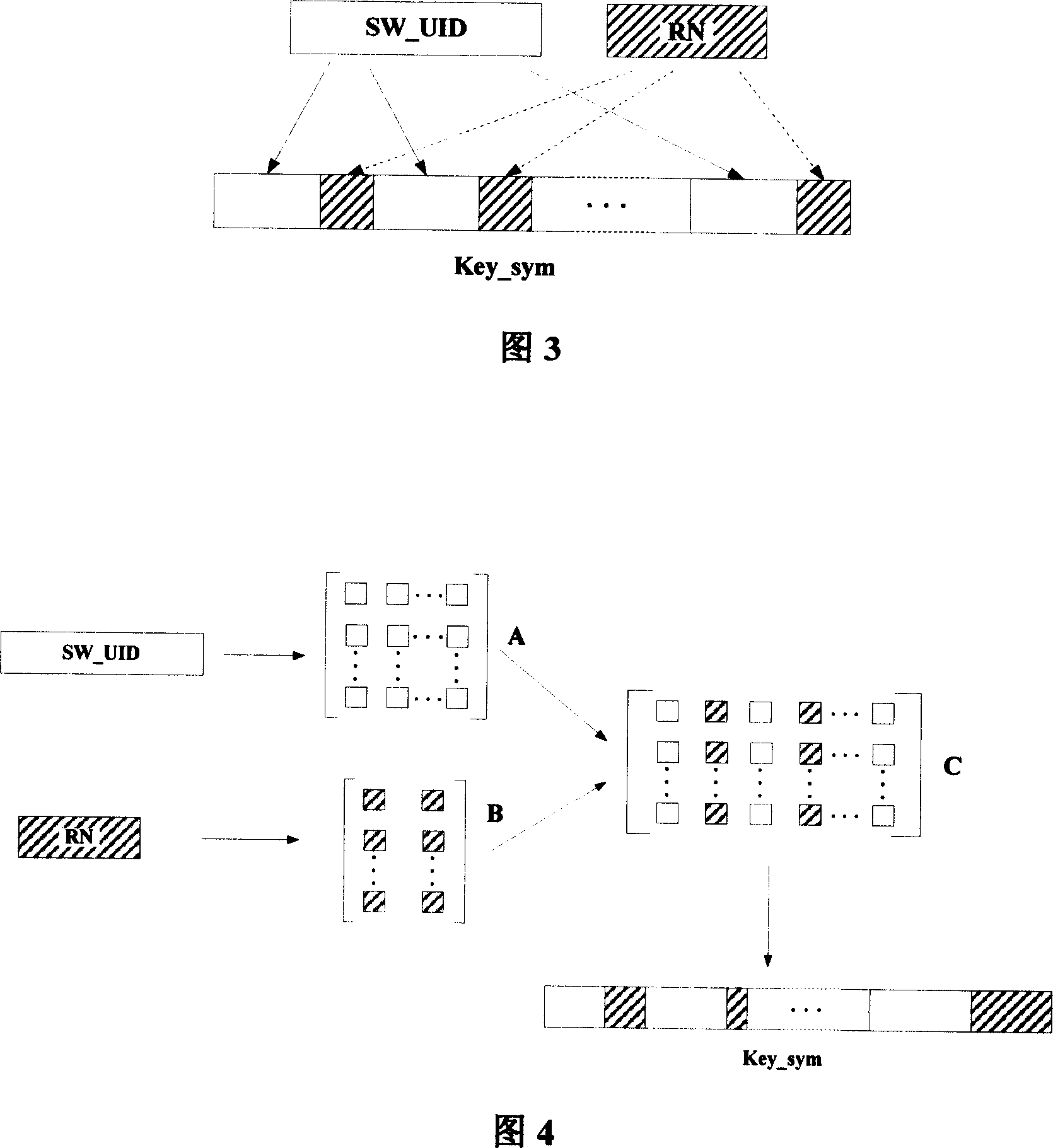
[0048] This embodiment provides an encryption and decryption method for special processor software, the steps of the encryption and decryption method are basically the same as those in Embodiment 1, the difference lies in the composition of Key_sym. As shown in Figure 3: what RN and SW_UID adopt is to divide the two sequences into the same number of shares, and then perform interpolation to form Key_sym, such as inserting M (M=2, 3...) SW_UID values into N ( N=1, 2...) RN values.
Embodiment 3
[0050] This embodiment also provides an encryption and decryption method for special processor software, the steps of the encryption and decryption method are basically the same as those in Embodiments 1 and 2, the difference lies in the composition of Key_sym. As shown in Figure 4: it adopts the method of interleaving and combining, first decomposing the sequences SW_UID and RN into matrices A and B respectively, then combining A and B into matrix C, and finally matrix C according to certain rules (such as by row or column readout) into a sequence to form Key_sym.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com