Detection method and device for DDoS attack
A distributed denial and attack detection technology, applied in the network field, can solve problems such as missed detection, achieve the effect of not easy to miss detection and improve efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
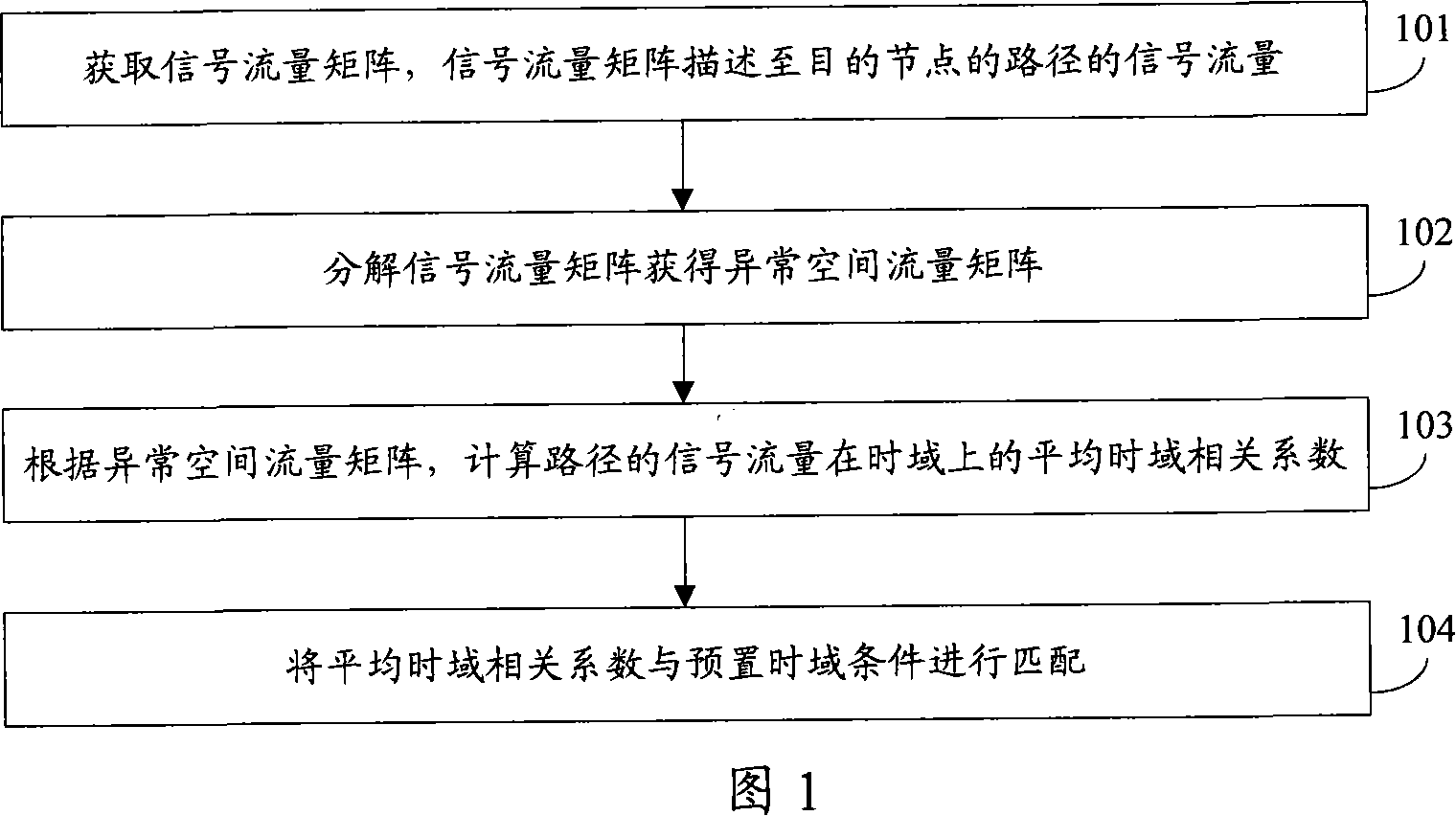
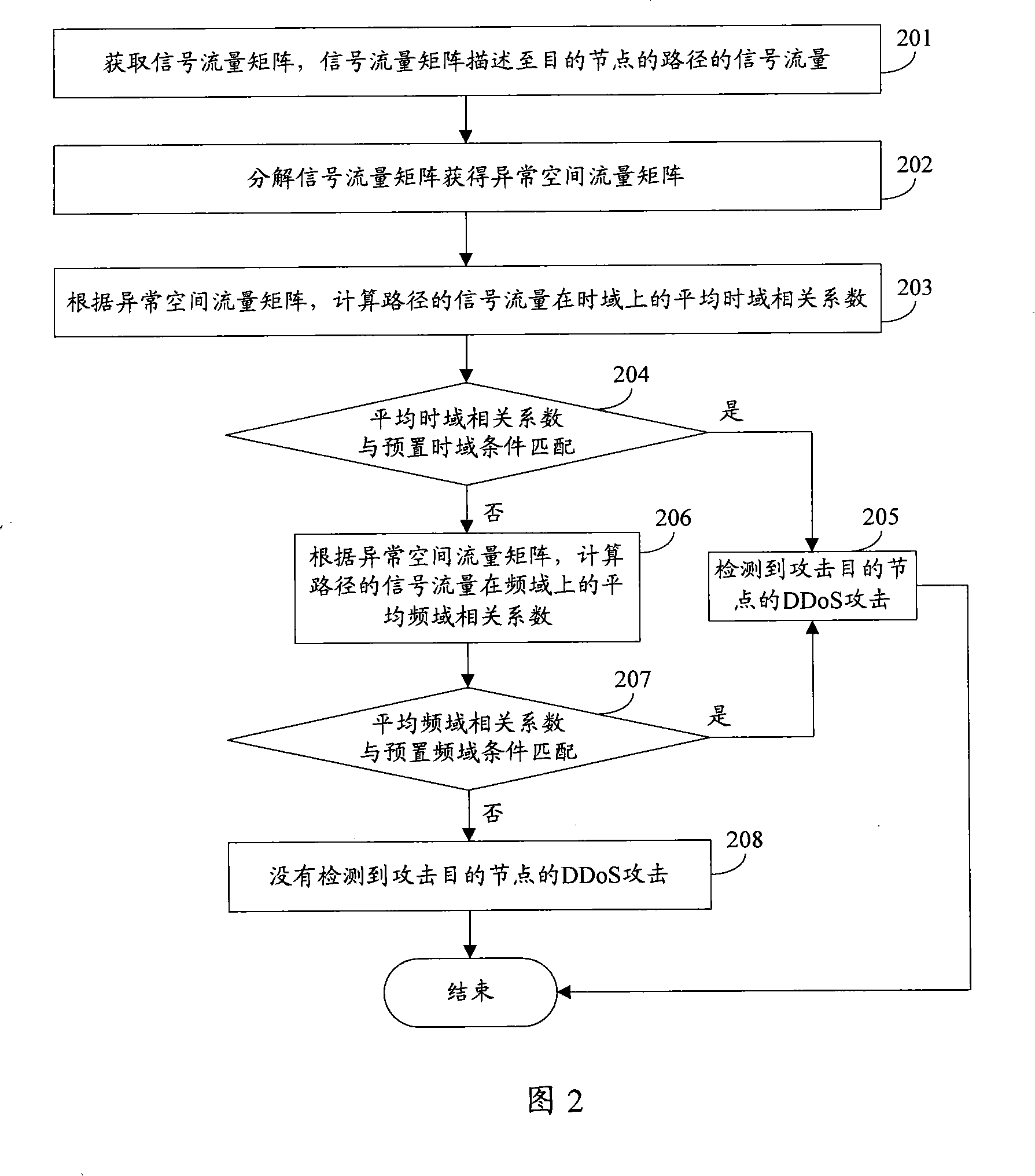
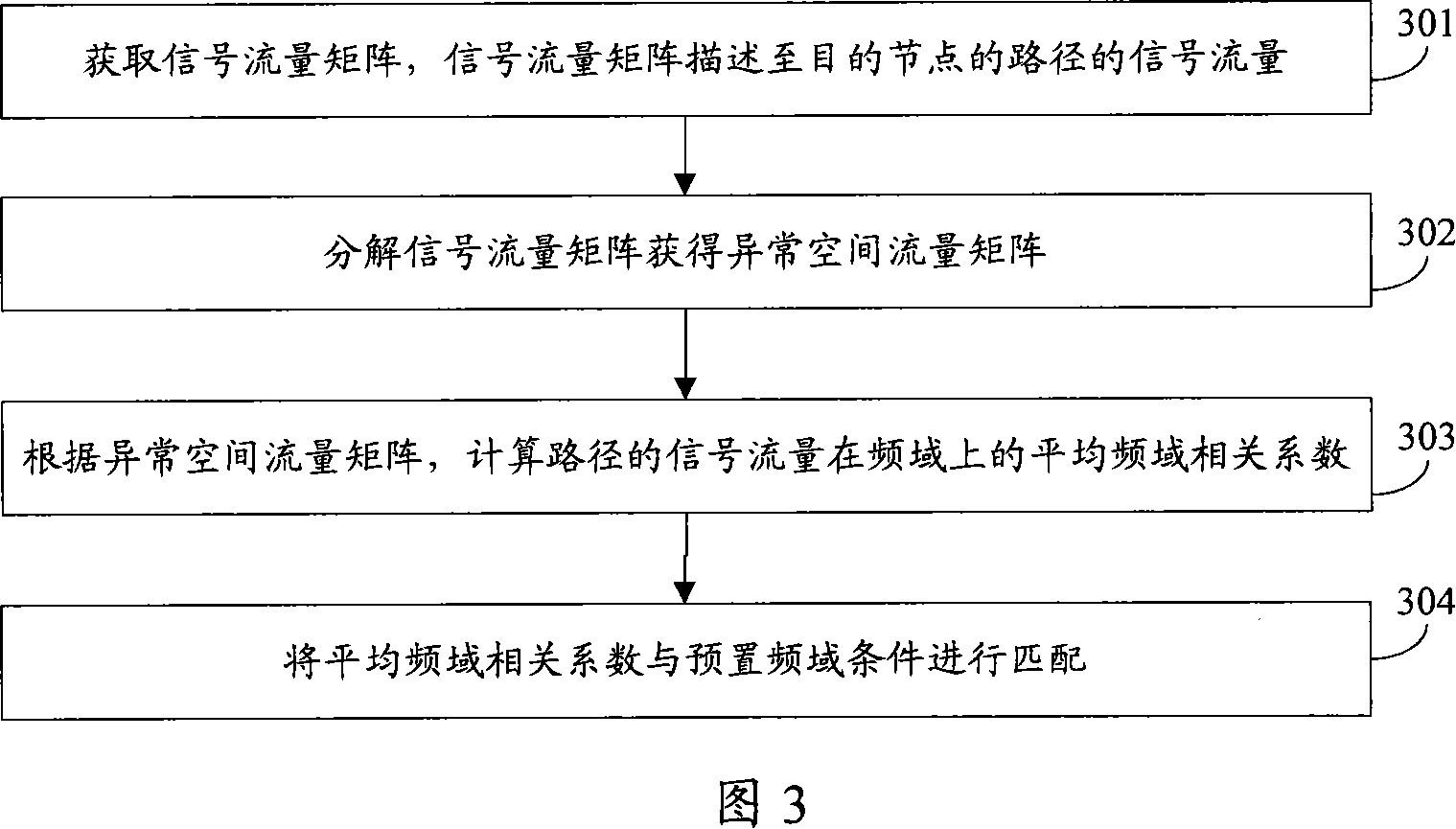
[0069] Embodiment 1 uses the link signal flow matrix to realize the present invention. In practical application, the embodiment of the present invention can further use the origin-destination (OD: Origin-Destination) flow flow matrix to realize the present invention, and the OD flow is a specific starting point The flow between the destination pair can contain multiple intermediate nodes. In a network with a fixed number of nodes, the number of OD flows is far greater than the number of links, and the traffic on a link often includes multiple OD flows with different starting node pairs. When using the OD flow flow matrix, the above paths are OD flows. Each row of the OD flow flow matrix represents the flow of one OD flow in the network, and the entire flow matrix describes the distribution of network flow among each OD flow. Wherein, the starting point and end point of the OD flow are different according to the specific situation, for example, it can be a link, a router, a ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com