Dual-protocol based VPN implementing method
An implementation method and dual-protocol technology, applied in the field of information security, can solve problems such as poor security, slow speed, and low function integration, and achieve the effect of avoiding major security risks, improving security and speed, and reducing forwarding and calling links
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
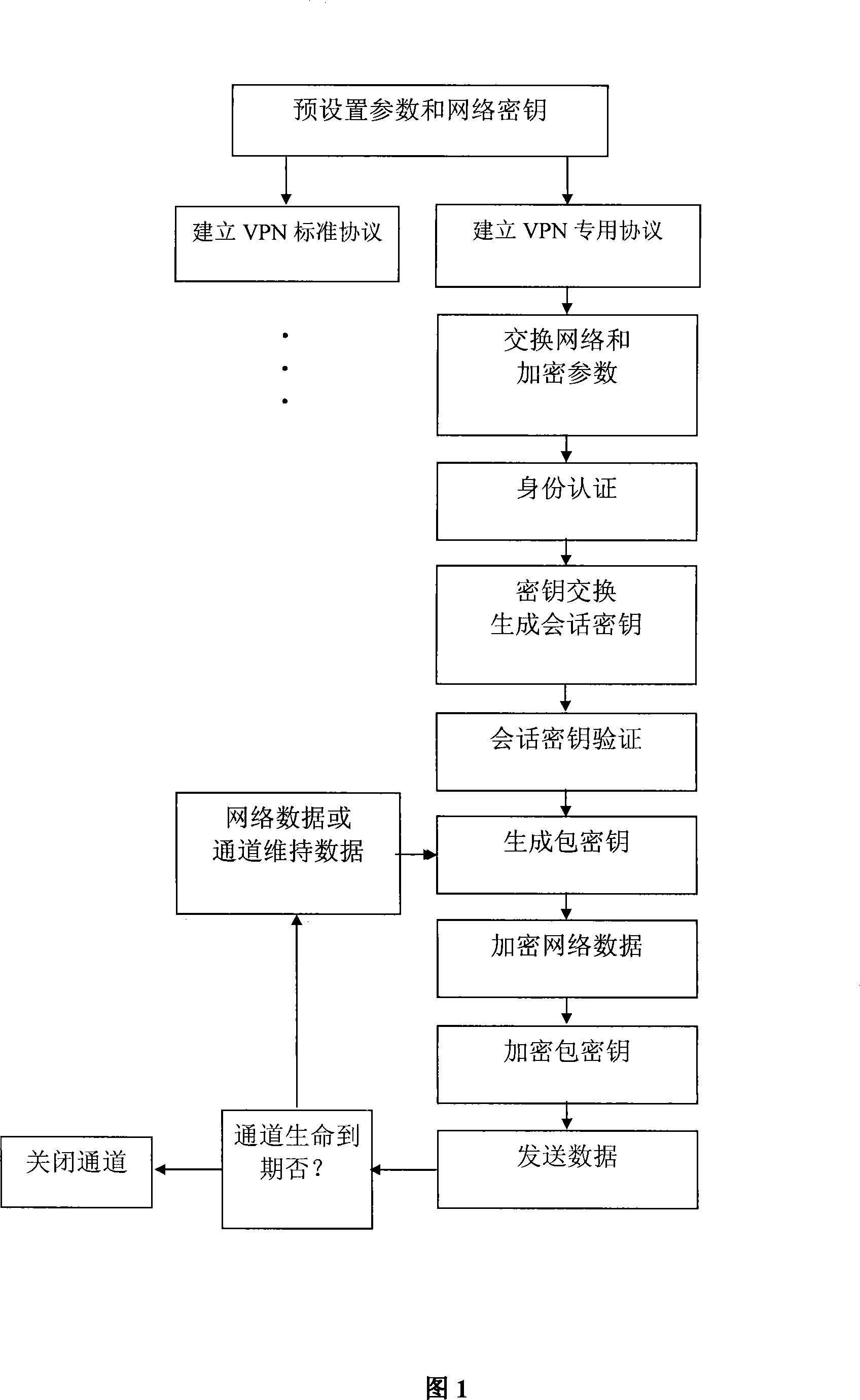
[0026] The implementation steps of the VPN protocol are illustrated below in conjunction with the accompanying drawings:
[0027] Figure 1: Illustrates the process of establishing a VPN dual protocol:
[0028] The first step is to pre-set parameters and network keys: pre-set communication protocols, network keys, and key length parameters;
[0029] The second step is to establish an IPSec standard encryption tunnel, namely: VPN standard protocol (omitted);
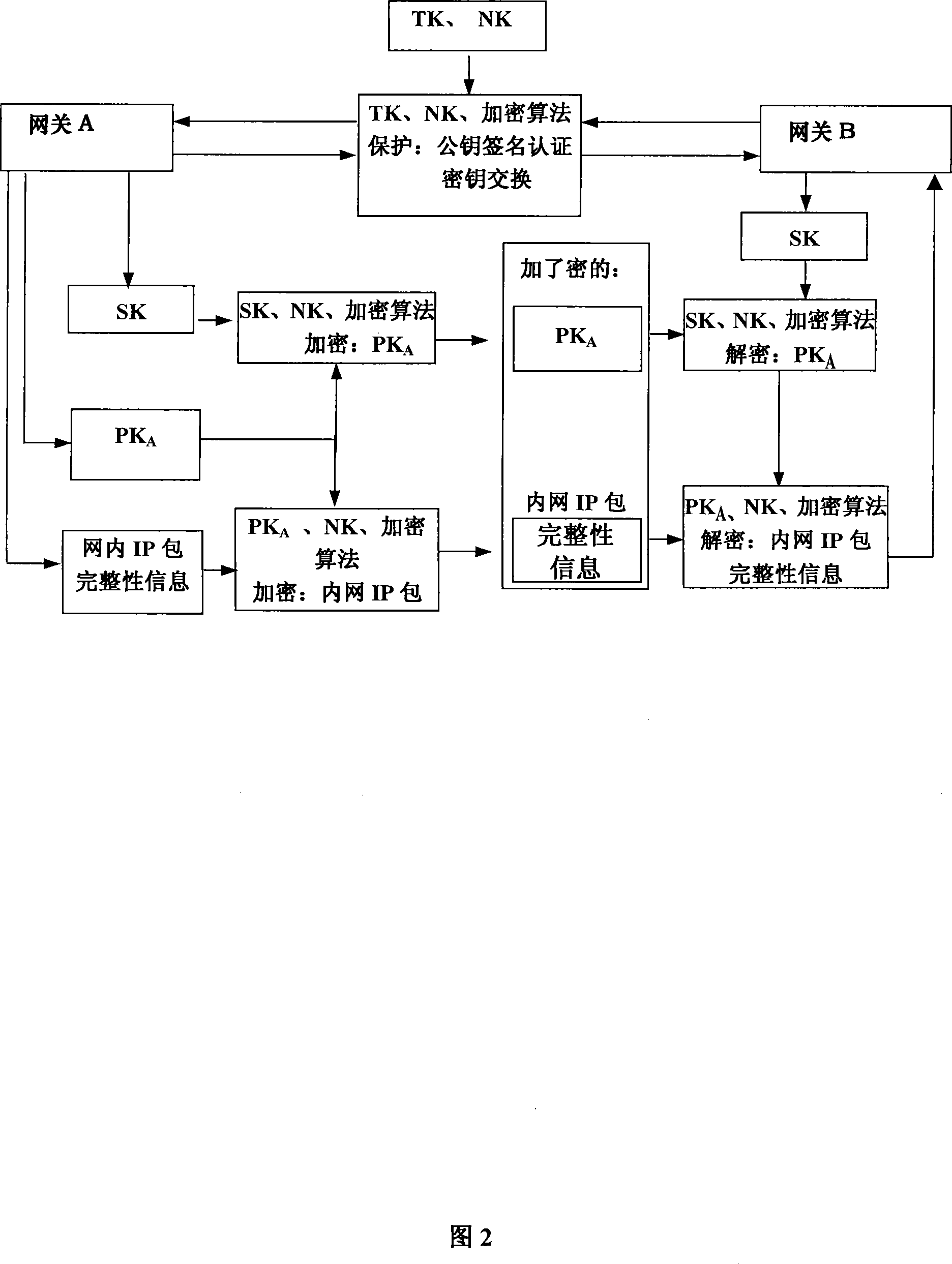
[0030] The third step is to establish a dedicated encrypted tunnel (i.e. VPN dedicated protocol): negotiate and exchange encrypted tunnel parameters, such as user names of both parties, protocol type, encryption algorithm, key length, length of public key algorithm, encrypted tunnel retention period, Encrypted tunnel timeout reconnection, timestamp;
[0031] The fourth step, identity verification and key exchange stage: use the negotiated encryption algorithm, pre-shared key, public key, hash function and digital signatu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com