Random concealed inquiry type cipher authentication technique
A password technology and password technology, applied in the direction of user identity/authority verification, etc., can solve the problem of inability to protect the security of user accounts, and achieve the effect of lifting the fixation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
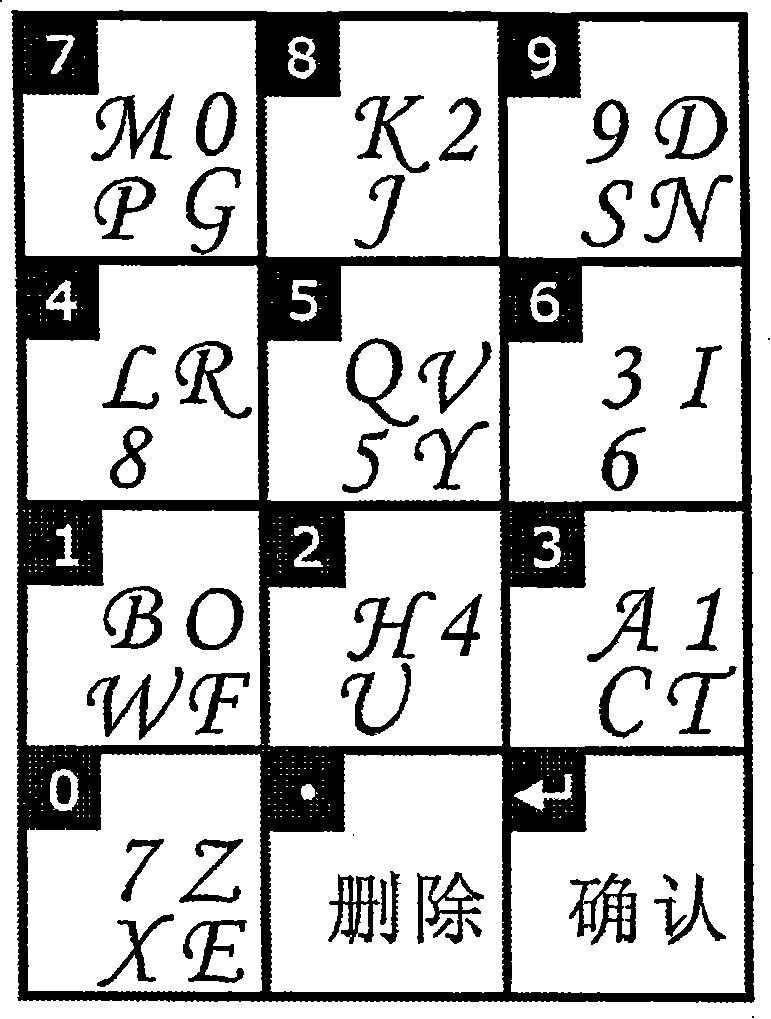
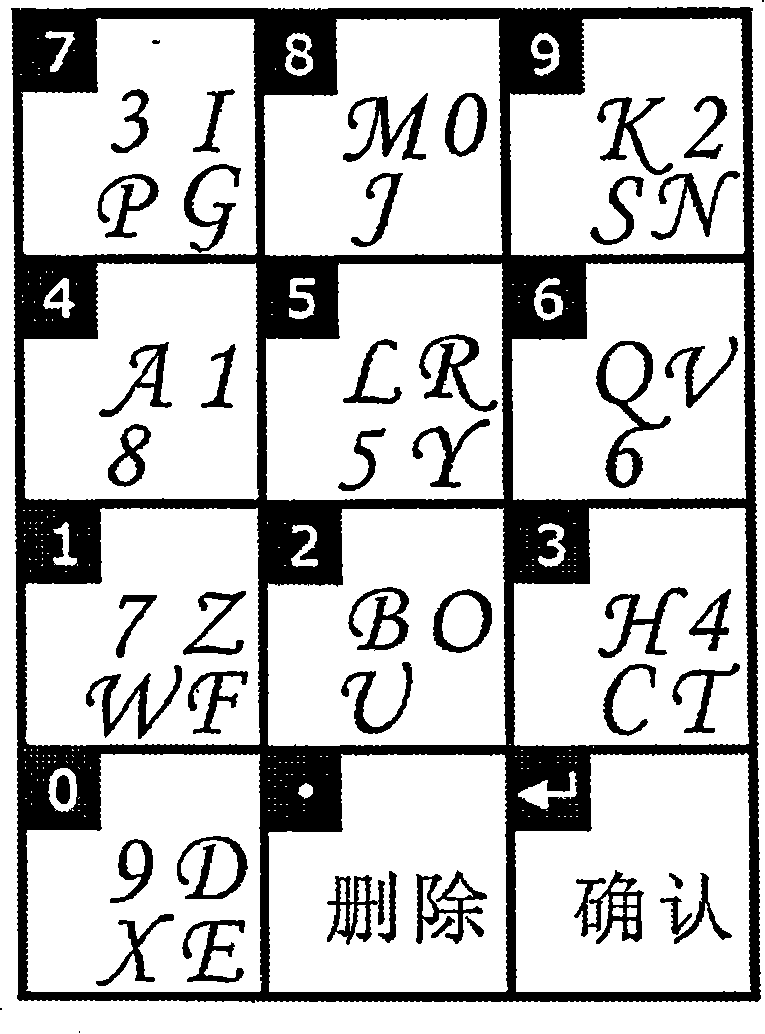
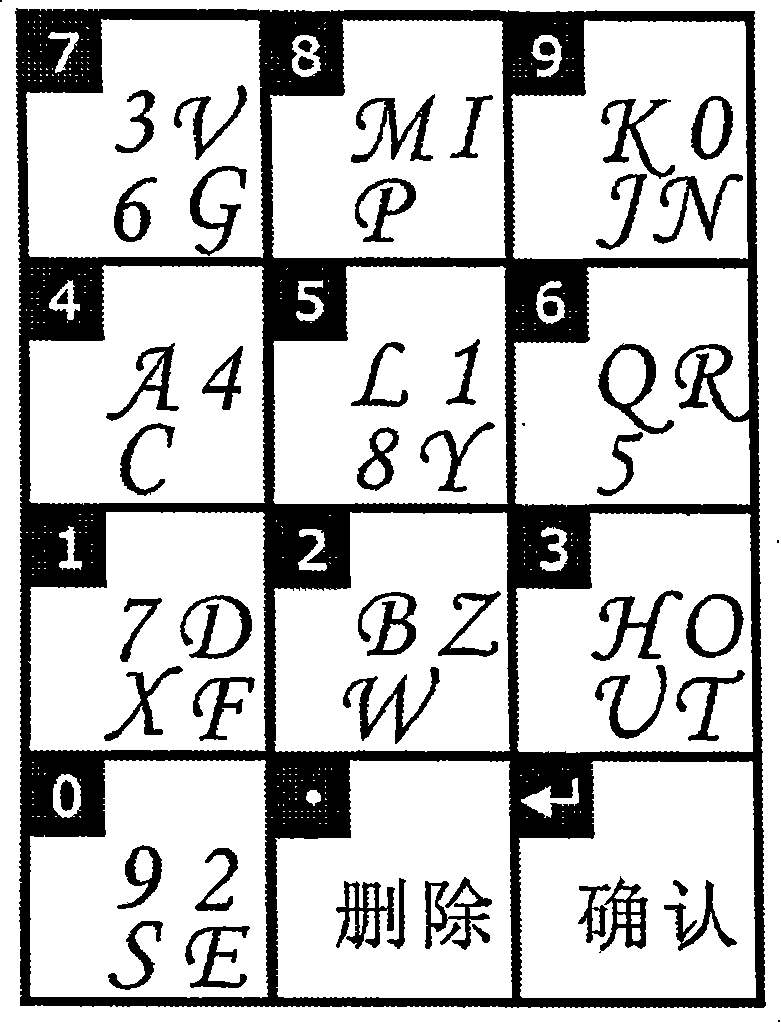
[0048] The implementation of this technology only needs to upgrade the code of the authentication part of the existing password system, and the original user data part does not need to be modified. Due to the diversity in the selection of development tools and programming languages for implementing this technology in an independent system or in an Internet system, it is impossible to list them one by one. Here, C language is used as an example to illustrate:
[0049] Core data structure:
[0050] 1. The structure array (character information table) used to store the effective password character set of the password:
[0051] structure
[0052] {
[0053] TCHAR character; / / store a valid character
[0054] HBITMAP hBitmap; / / Store the image handle corresponding to the character, the format is a bitmap.
[0055]}CharInfo[36]; / / 36 is the default effective number of characters, 0~9, A~Z. Can be expanded upon request.
[0056] 2. Due to people's thinking habits, in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com