Authentication method for limiting mobile phone without using by others
A technology for users and mobile phones, which is applied in the field of authentication where users restrict others from illegally using mobile phones. It can solve the problems of reducing password security, restrictions, and high cost of system transformation, so as to meet individual needs, reduce the frequency of use, and reduce construction costs. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
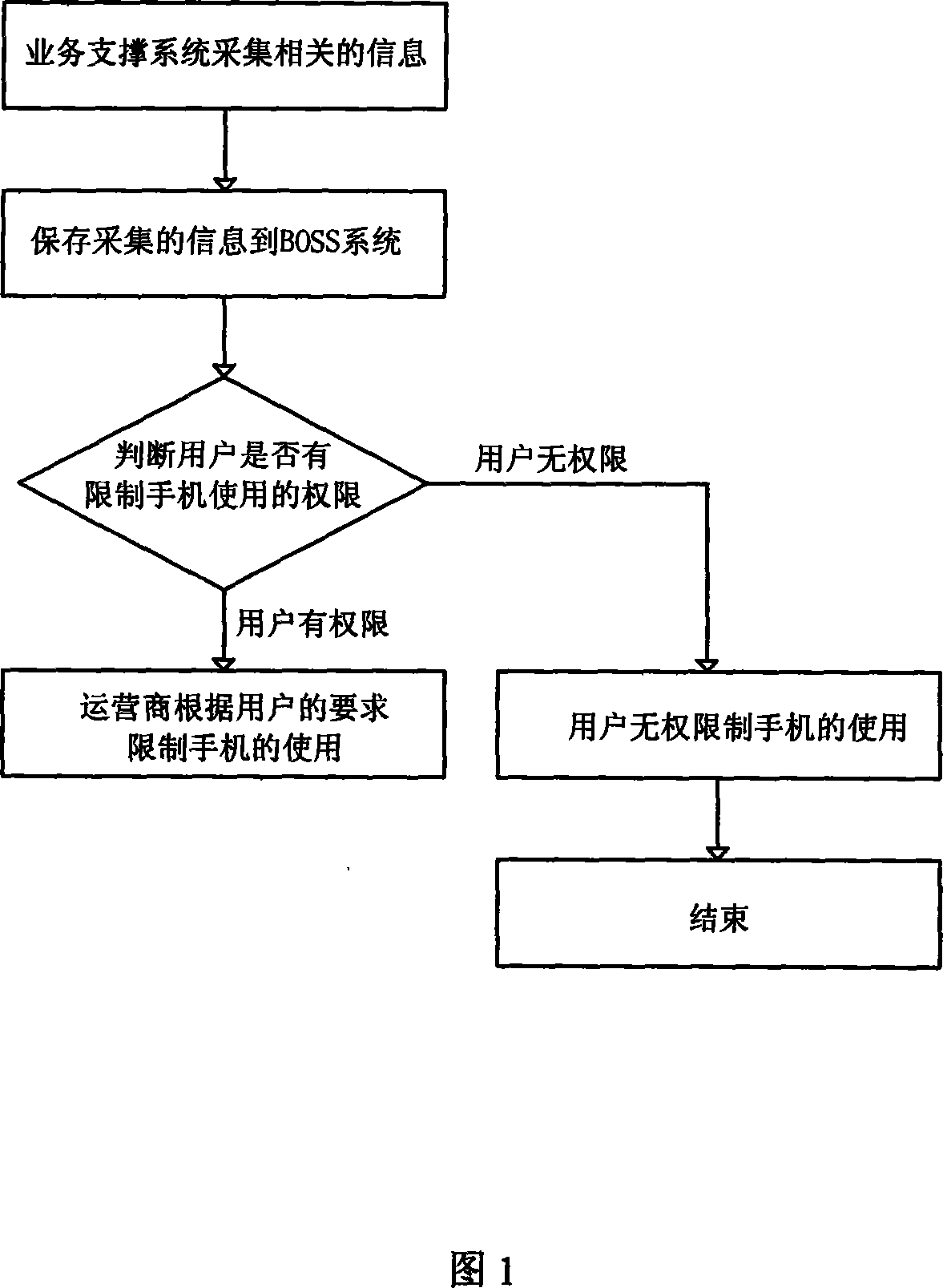
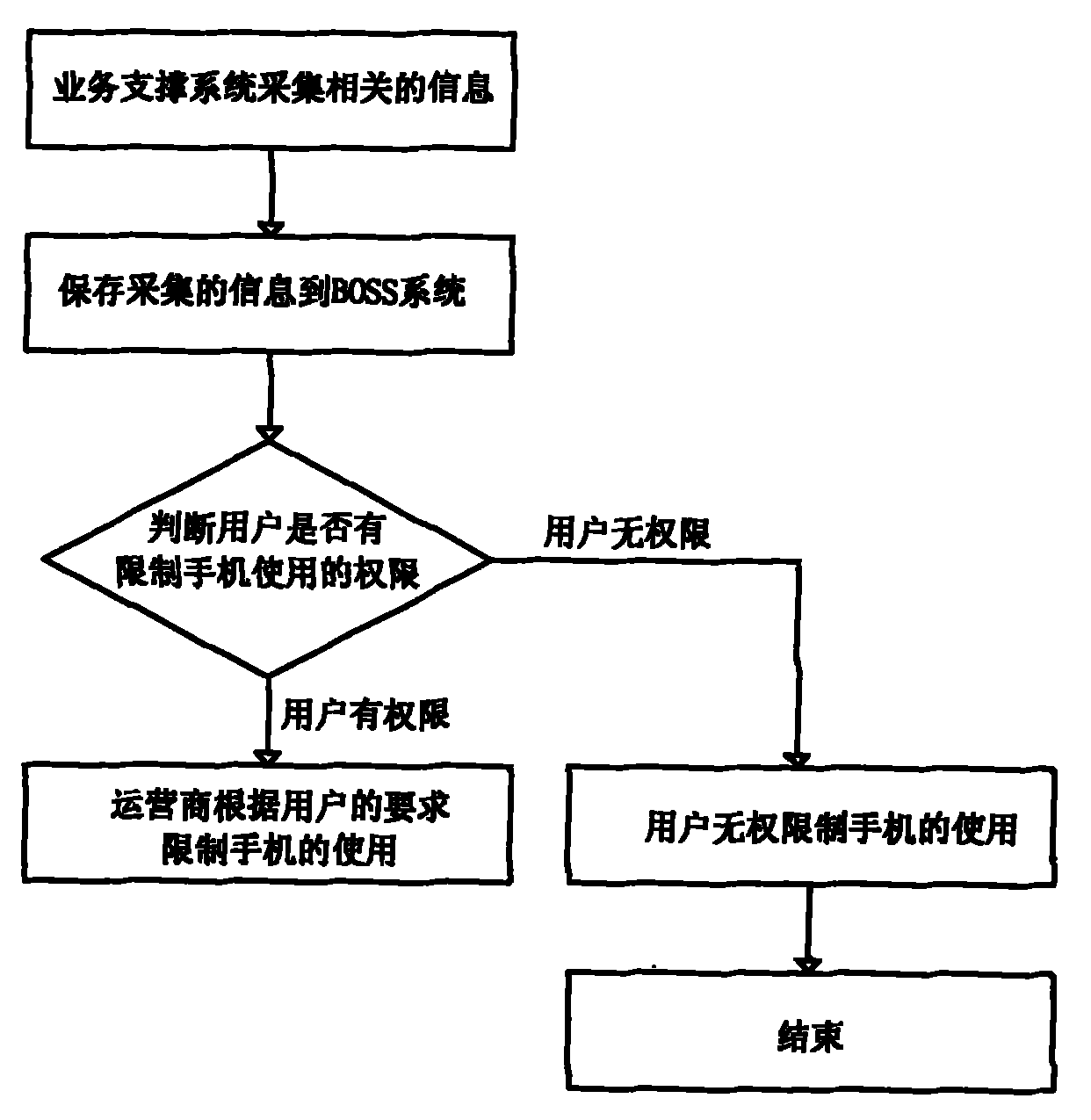
[0023] As shown in Figure 1, an authentication method for a user to restrict others from illegally using a mobile phone, the processing flow is as follows:
[0024] A. In the process of providing communication services to users, the business support system collects mobile phone numbers, corresponding mobile phone IMEI, usage time and related user information;
[0025] B. Save the user information collected in step A to the BOSS system;
[0026] C. When a user initiates to restrict the use of a mobile phone, the operator judges whether the user who initiates the restriction of mobile phone use has the right to perform this operation according to the information saved in step B;
[0027] D. When the relevant proof provided by the user is consistent with the user information saved in step B, the user has the right to restrict operations, and the operator will restrict the mobile phones that are required to be restricted according to the user's requirements.
[0028] The business...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com