Entity bidirectional identification method
A physical and legal technology, applied in the direction of public key for secure communication, user identity/authority verification, digital transmission system, etc., to achieve the effect of facilitating application implementation and simplifying operating conditions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
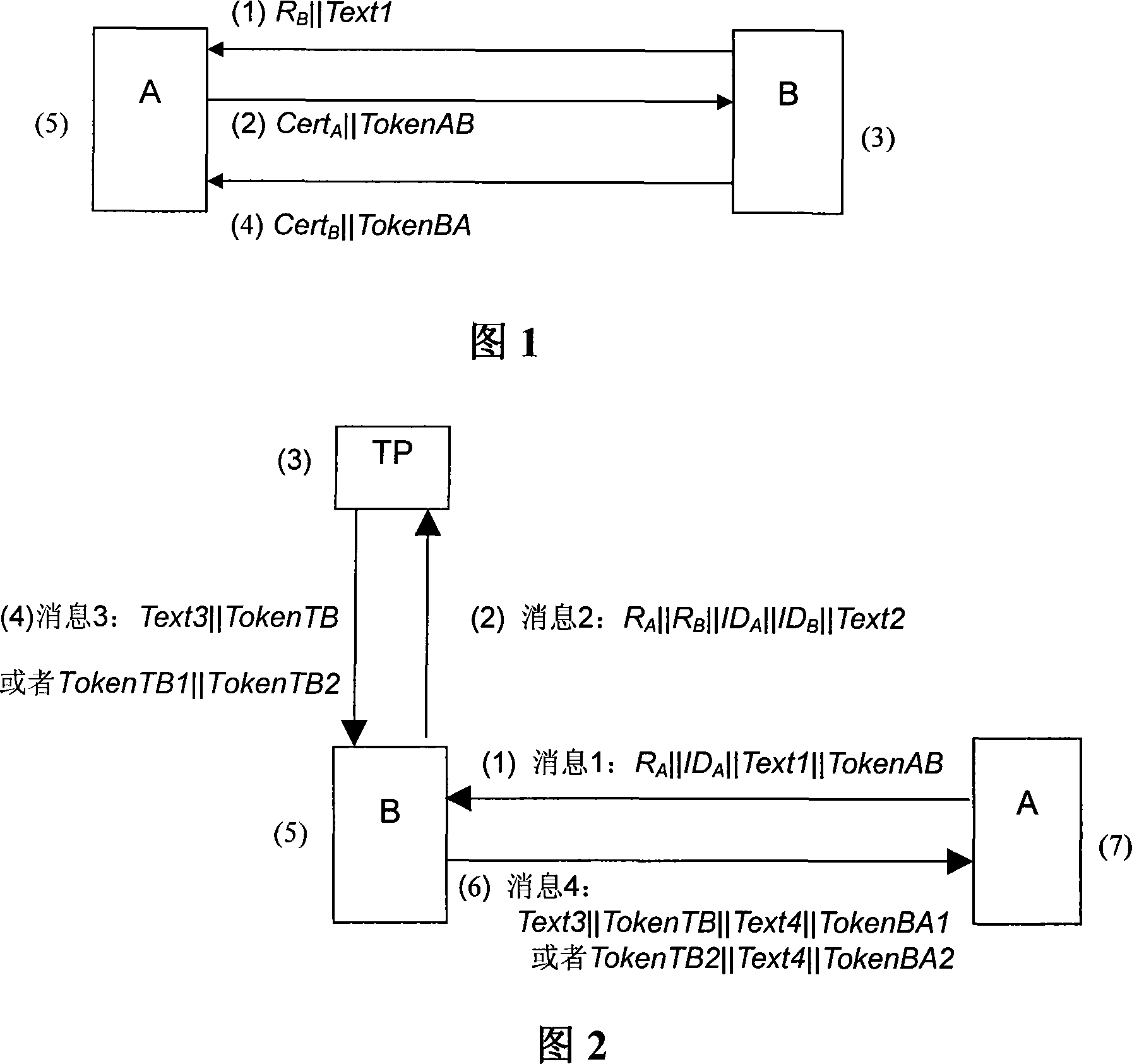
[0040] Referring to Fig. 2, the method of the present invention involves three entities, two authentication entities A and B, and a trusted third party TP (Trusted third Party), which is a trusted third party for the authentication entities A and B. The system that realizes peer-to-peer authentication between two entities A and B through a trusted third party TP is called a TePA (Tri-element Peer Authentication) system. valid X Indicates the certificate Cert X Validity; PublicKey X is the public key of entity X (X stands for A or B); ID X Is the identity of entity X, by the certificate Cert X or the entity's discriminator X means; Pub X Indicates the verification result of entity X, which is determined by the certificate Cert X and its validityValid X Consists of or consists of entity X and its public key PublicKey XComposition, Token is the token field, defined as follows:
[0041] TokenAB=sS A (R A ‖ID A ‖Text1)
[0042] TokenTB=R A ‖R B ‖Pub A ‖Pub B ‖sS TP...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com