Network inbreak event association detecting method
A technology of event correlation and detection method, applied in the field of network security, to achieve the effect of improving speed and efficiency, reducing the amount of analysis data, and reducing the false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
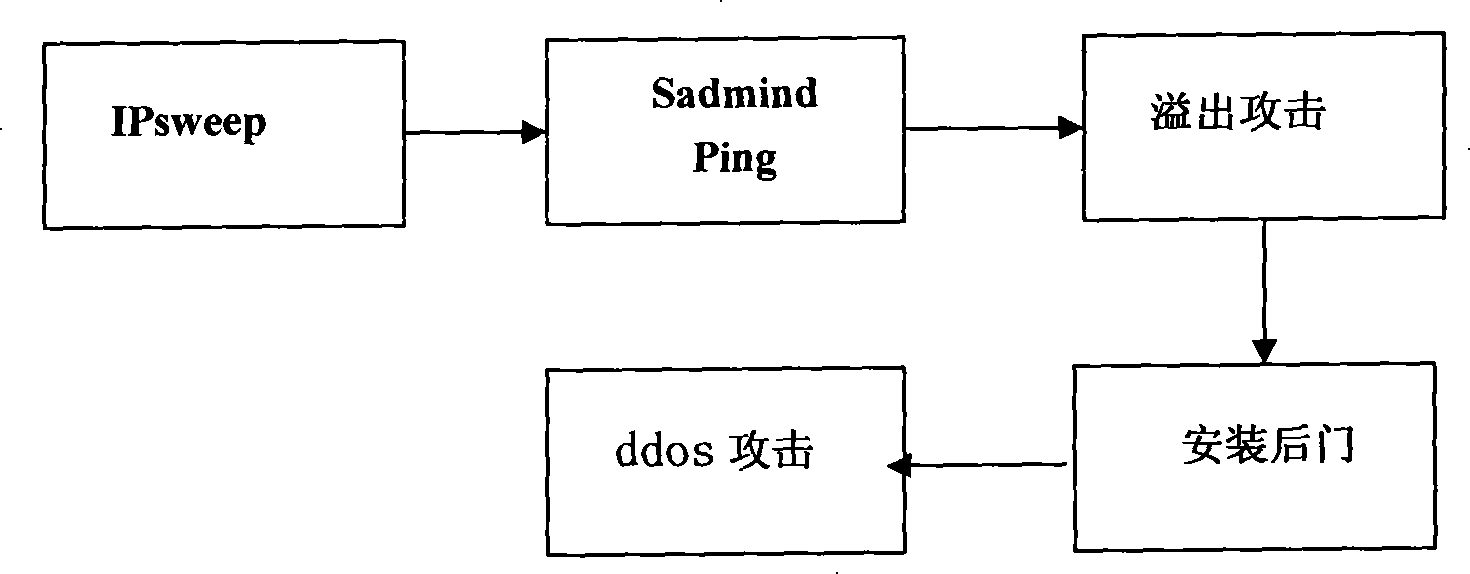
[0025] 3. If the Solaris host has a vulnerability, use the host with the sadmind vulnerability to launch a buffer overflow attack to obtain the root authority of the host. This attack step needs to be performed multiple times to obtain the root authority of multiple hosts;
[0026] 4. Install denial-of-service attack programs on these hosts that have obtained root authority, and install a control program on one of the hosts;
[0027] 5. The hacker controls the denial of service ddos attack program from the control machine to attack;
[0028] The hacker's intrusion is an orderly process, and only after the previous intrusion steps are successful, the subsequent intrusion steps can be executed normally.
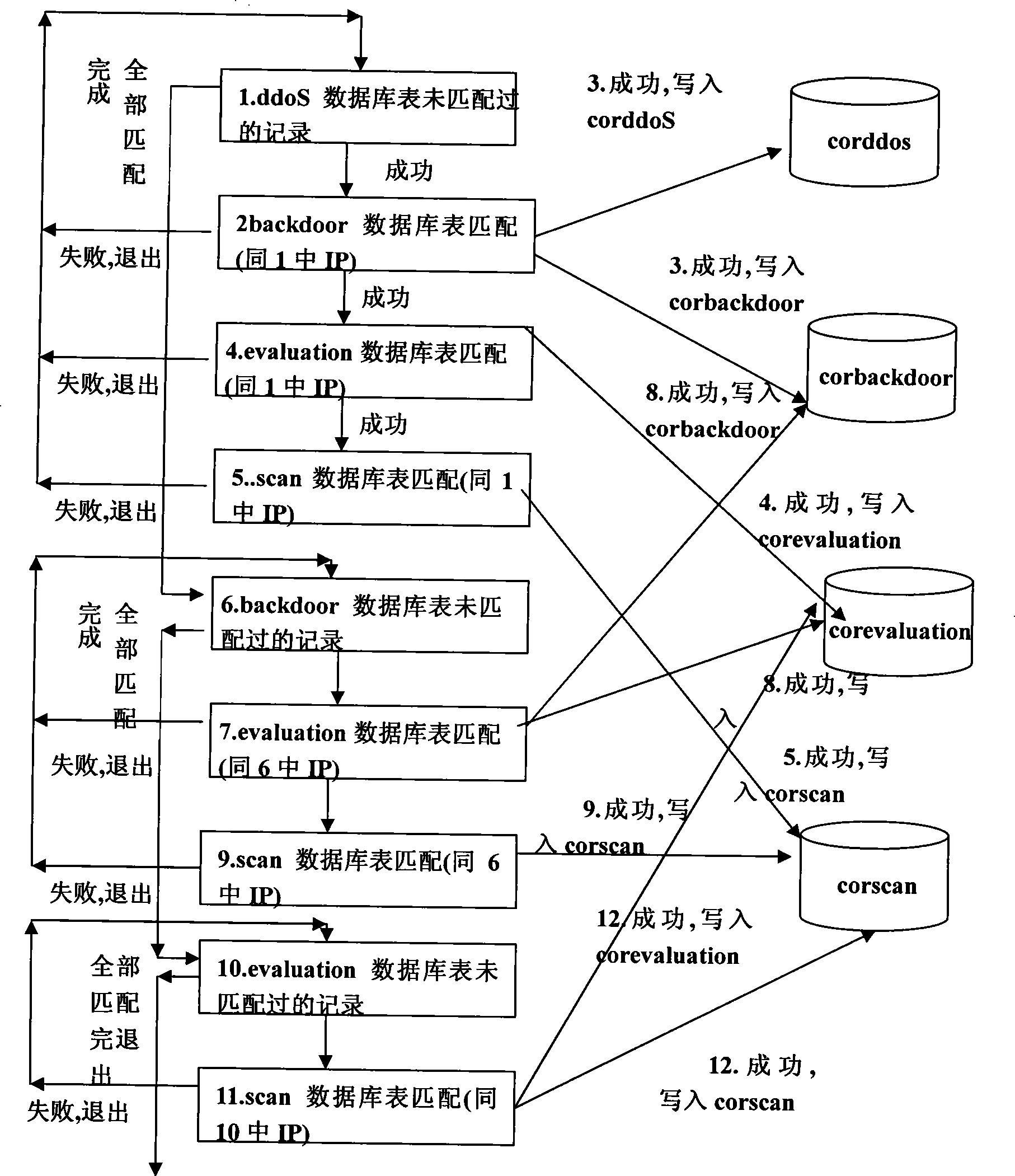
[0029] like figure 2 As shown, this embodiment proposes the following specific steps for the general sequence of the above-mentioned hacking system:
[0030] First, four database tables are established to store four types of original alarm events: scan for vulnerabilities,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com