Method for reinforcing fingerprint Fuzzy Vault system security
A system security and fingerprint technology, applied in the fields of information security and biometric identification, network and information security, biometric authentication, and biometric encryption, it can solve problems such as increasing attack complexity, short exposure of minutiae templates, and affecting system performance. , to prevent cross-comparison security loopholes, improve system availability, and improve computing performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
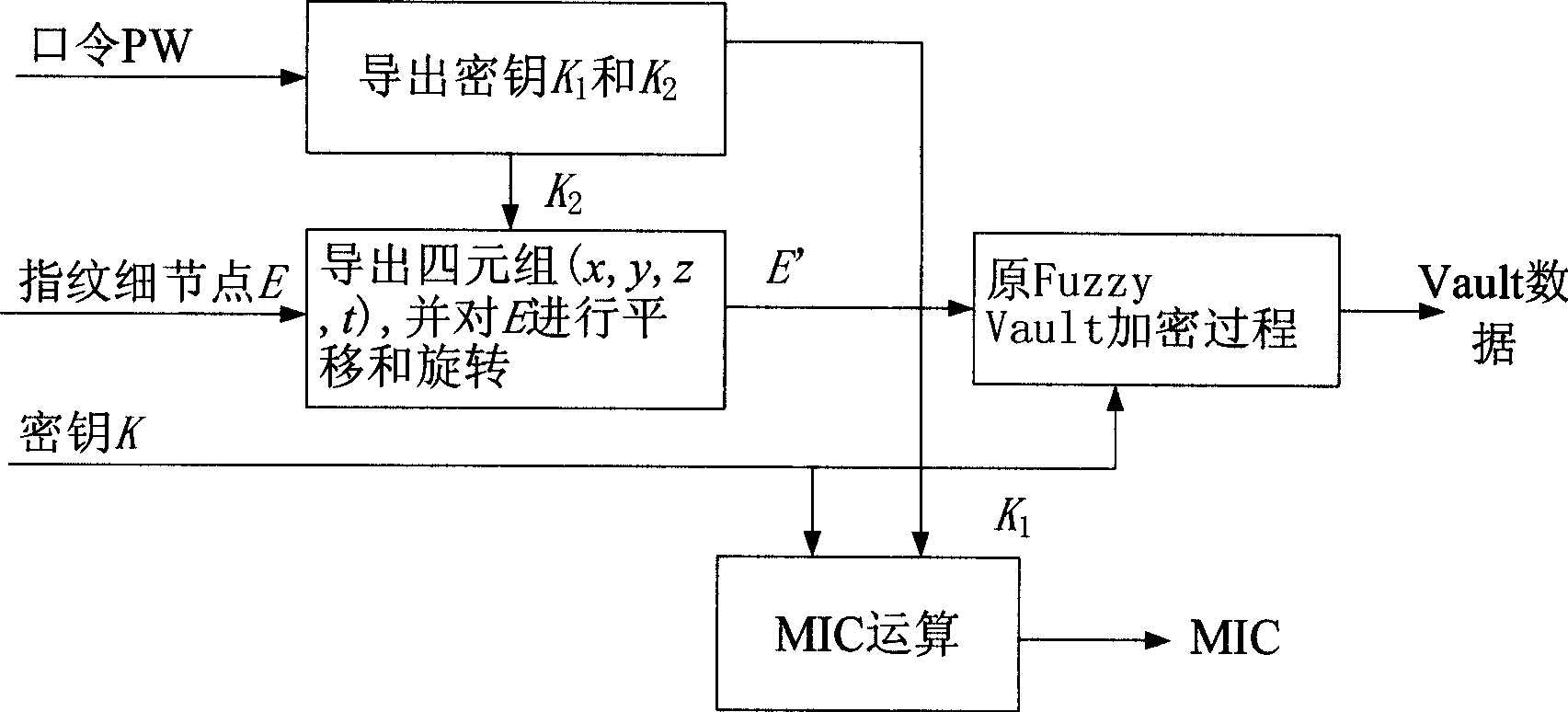
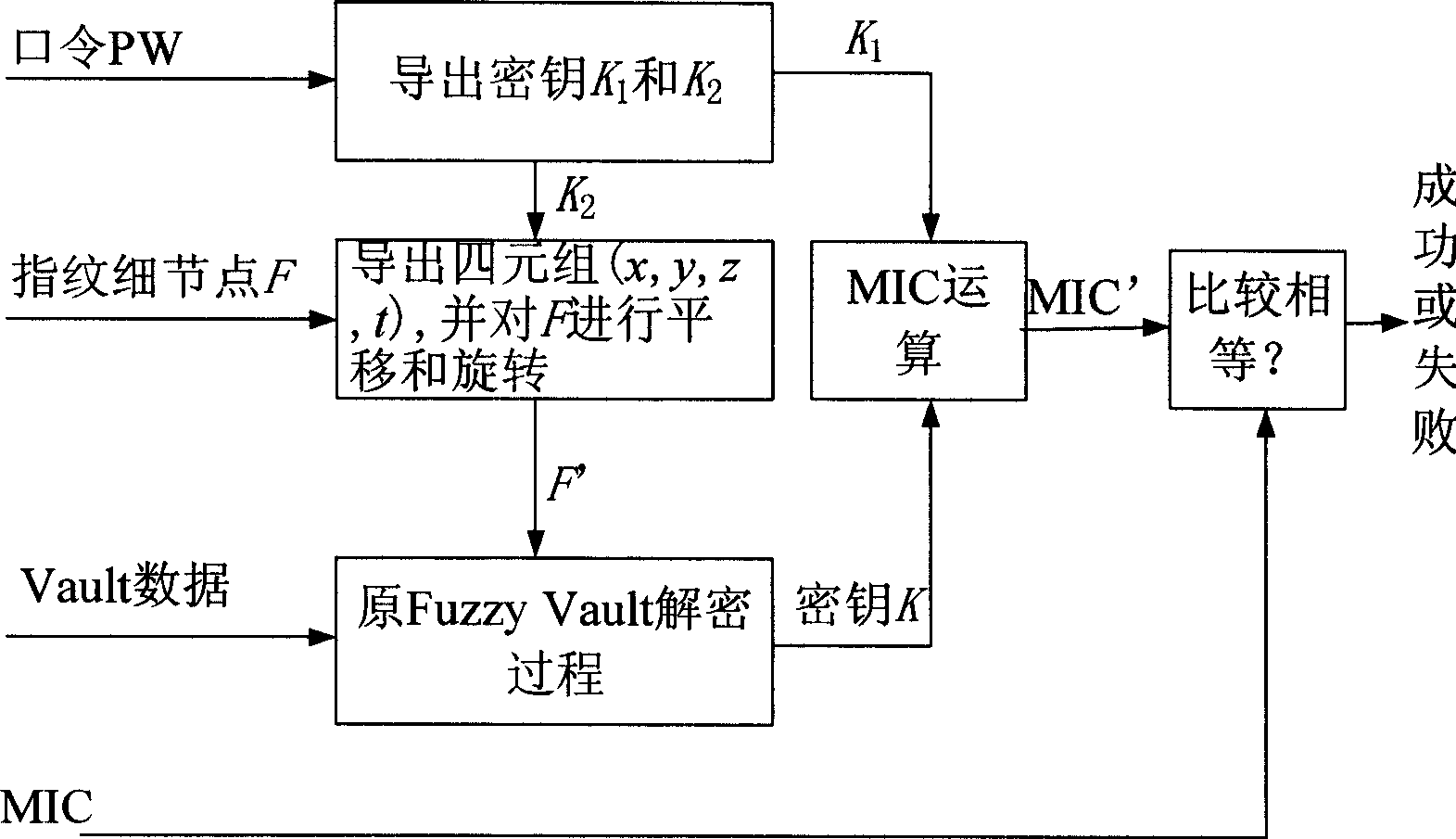
[0049] A complete, secure and revocable Fuzzy Vault encryption and decryption process will be described in the specific implementation manner with reference to the accompanying drawings.
[0050] refer to figure 1 , the Fuzzy Vault encryption process of the present invention is as follows:
[0051] 1) Fuzzy Vault encryption process: users can bind the key K with their own fingerprint detail point information E and secret password PW to generate Vault data.
[0052] In this process, the input information is fingerprint minutiae information E, password PW and key K; the output information is Vault data and integrity check value MIC. The encryption process is as follows:
[0053] 1.1) According to the password PW, derive two keys K 1 and K 2 ;
[0054] 1.2) Further expand and divide the key K2 to generate a secret quadruple information (x, y, z, t);
[0055] 1.3) Use the secret quadruple information (x, y, z, t) to perform rotation and translation transformation on the fing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com