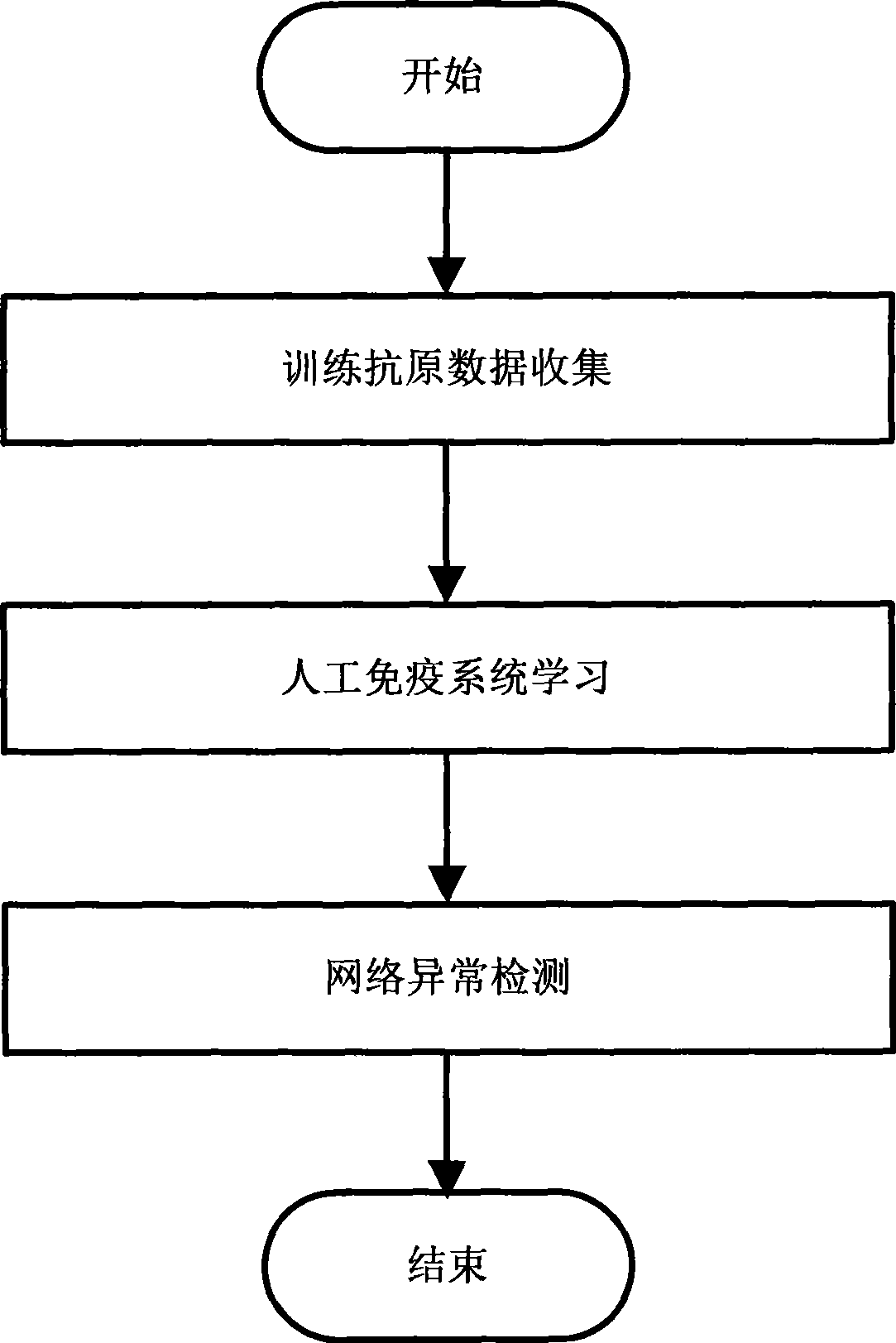
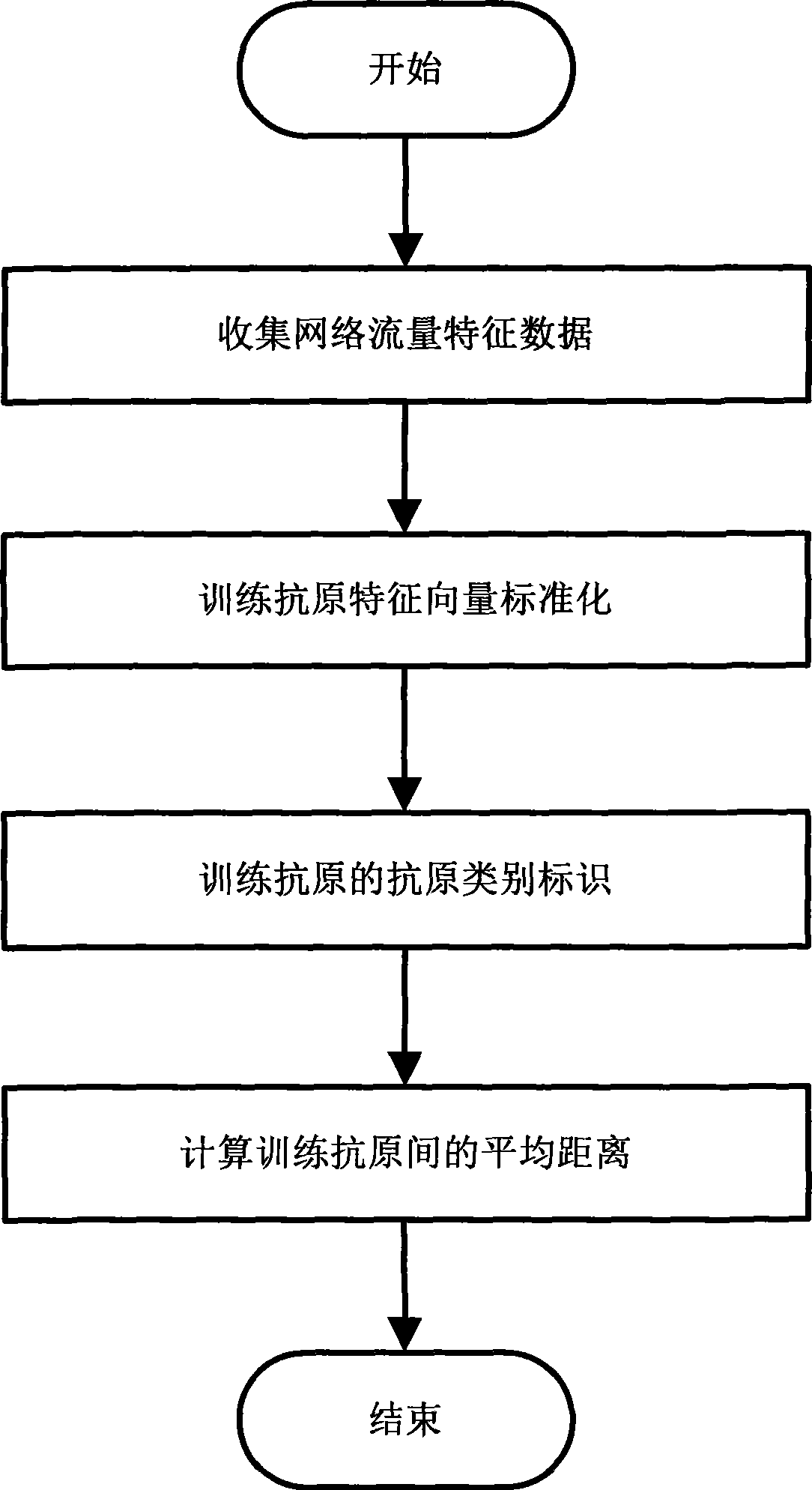
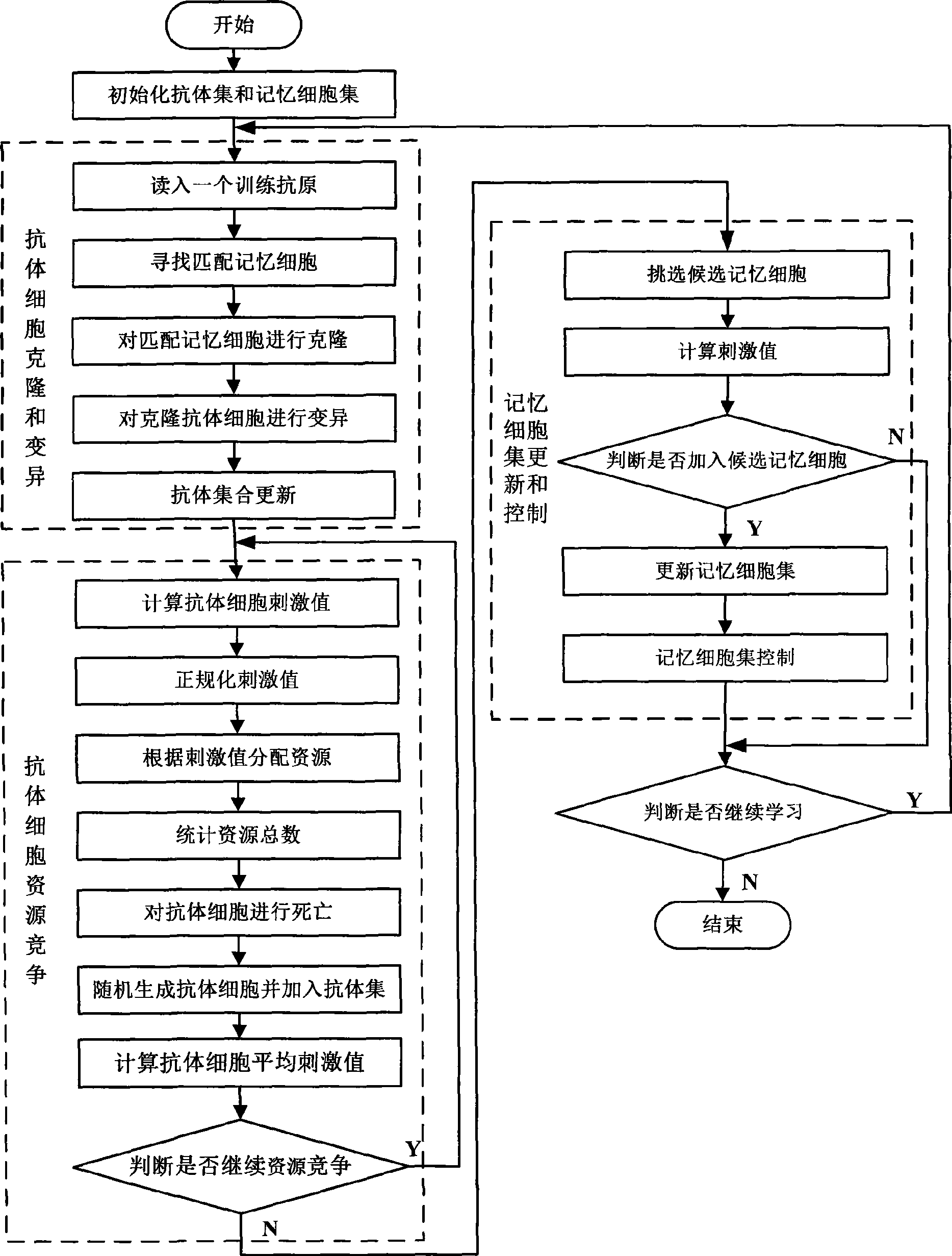
Network exception detecting method based on artificial immunity principle
A technology of artificial immunity and network anomaly, applied in the field of network anomaly detection based on the principle of artificial immunity, can solve the problems of slow detection speed and low detection accuracy, and achieve the effect of fast detection speed, high detection accuracy and wide application prospects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] Before explaining in detail, some nouns, symbols and some formulas used in the invention are first defined:
[0049] (1) Define M to represent a set of memory cells, m to represent a memory cell, and m∈M. Define B as an artificial antibody set, b represents an antibody cell and b ∈ B; define G as an antigen set, g represents an antigen, and g ∈ G; define C as an antigen set, and c represent a memory cell, antibody or antigen category, And c ∈ C.
[0050] (2) Define memory cell m, antibody cell b, antigen g consists of categories and feature vectors, namely , where m.c represents the category of memory cells mc, and m.c∈C={0, 1}, b.c and g.c represent antibody and antigen categories respectively, and b.c∈C={0, 1}, g.c∈C={0, 1}, where 0 indicates normal network behavior and 1 indicates abnormal network behavior. g.f, m.f, and b.f represent the eigenvectors of g, m, and b respectively, and the eigenvectors are composed of characteristic data describing network transactio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com