Abnormal enquiry and monitor method based on target condition association rule database
A target condition and anomaly detection technology, applied in electrical digital data processing, special data processing applications, instruments, etc., can solve problems such as high false detection rate and missed detection rate, and achieve low missed detection rate, high precision, and space-time efficiency. high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
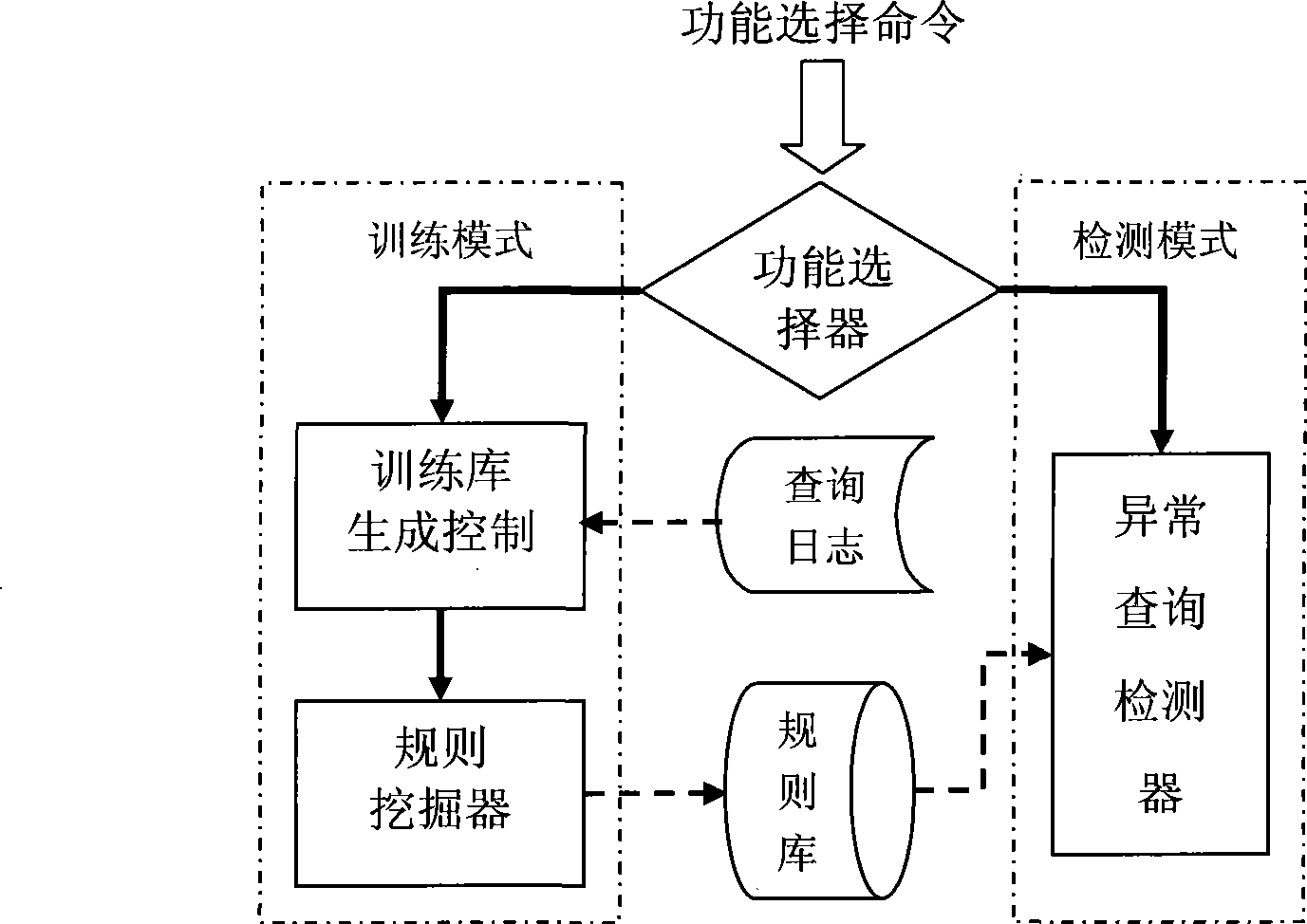
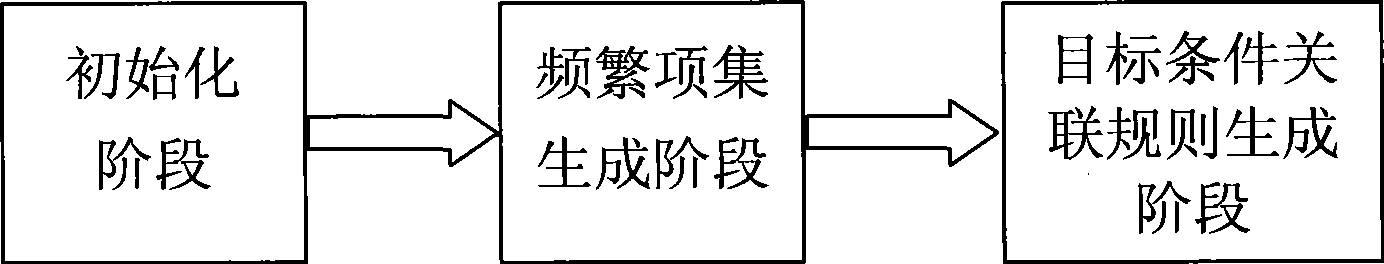
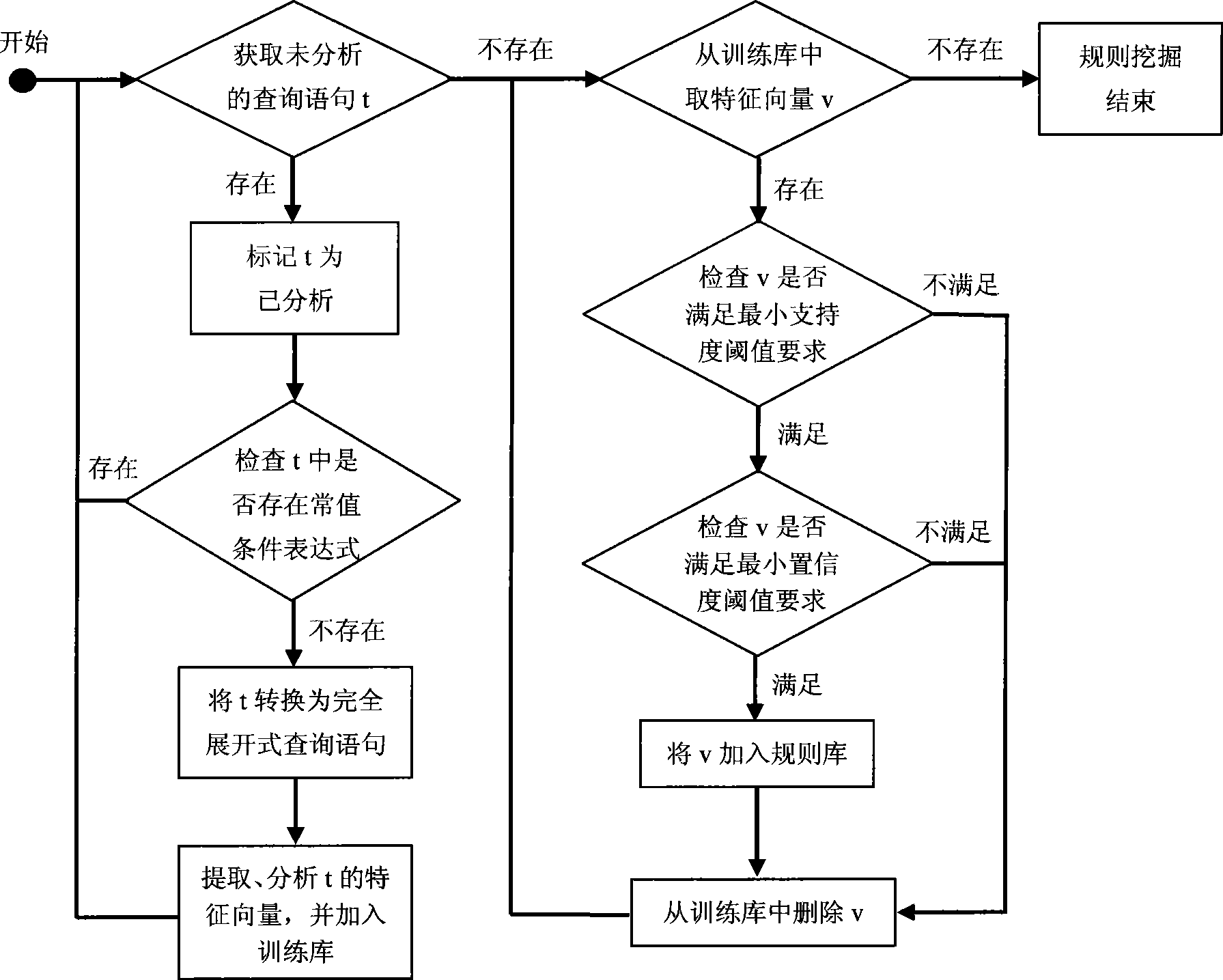
[0043] For the query sentence s="SELECT attribute FROM relational table WHERE condition...", we call the part before "WHERE" the target clause or target expression, and the part after it is called the condition clause or condition expression.
[0044] Condition factor: In the condition clause, the predicate expression that meets the SQL standard syntax requirements is the condition factor, which is in the form of "expr 1 opt expr 2 ", where expr 1 And expr 2 For expressions, values, or subqueries, etc., such as attr+2, 5 * attr, 100, etc., opt is a relational predicate, such as >, <, =, LIKE, IN, etc. The condition factor is the smallest element of the condition clause.
[0045] If the condition factor is always "true" or "false", it is called a constant value condition factor. For example, for the condition factors "1=1", "2!=2" and "age=age" (age is assumed to be some Relationship attributes), obviously, they are all constant conditional factors.
[0046] For something like "SEL...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com