Computer system, computer network and data communication method
A computer system and computer network technology, applied in the field of computer security, can solve problems such as attacks that cannot solve processes and systems, and achieve the effect of strengthening security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
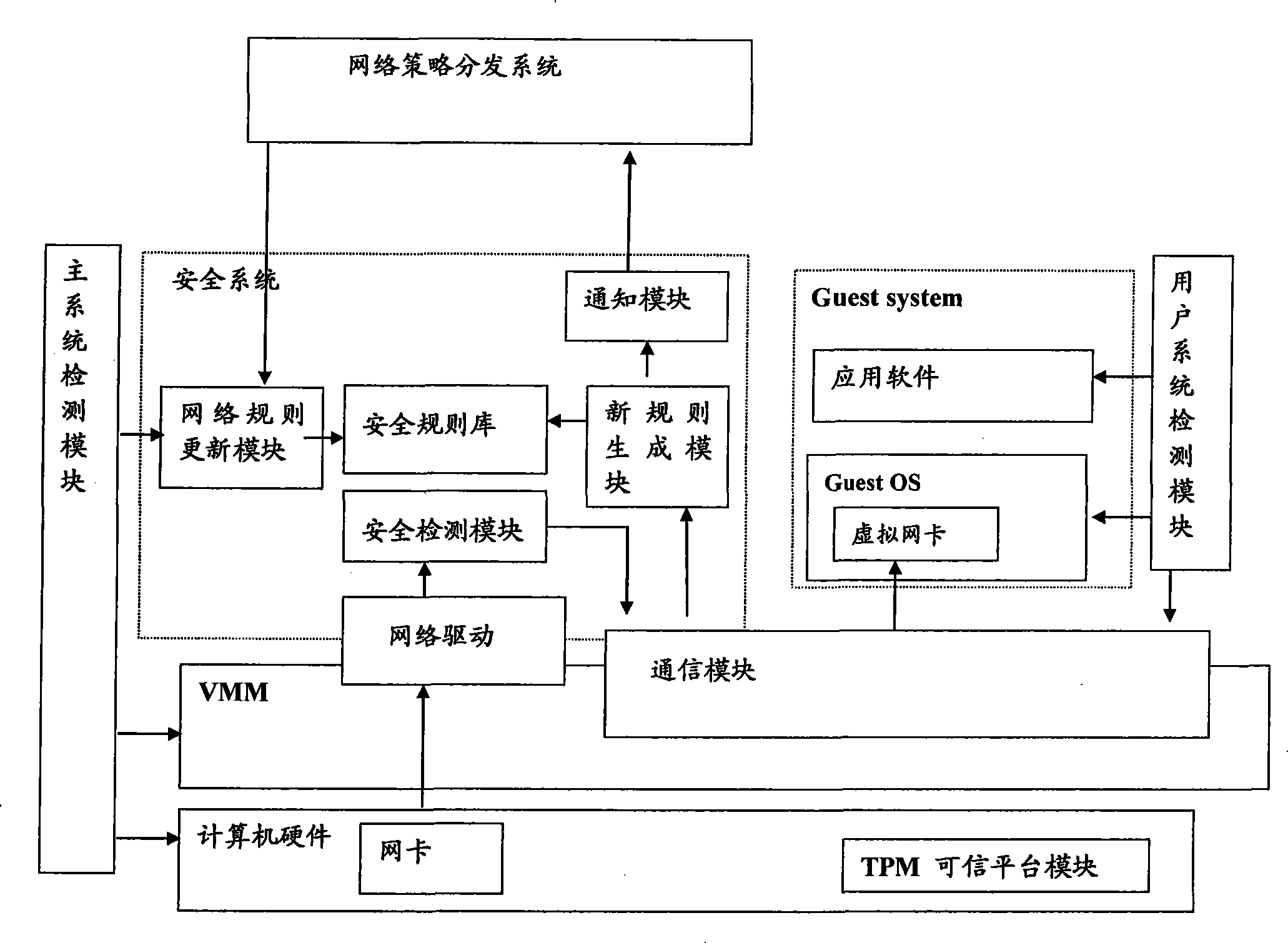
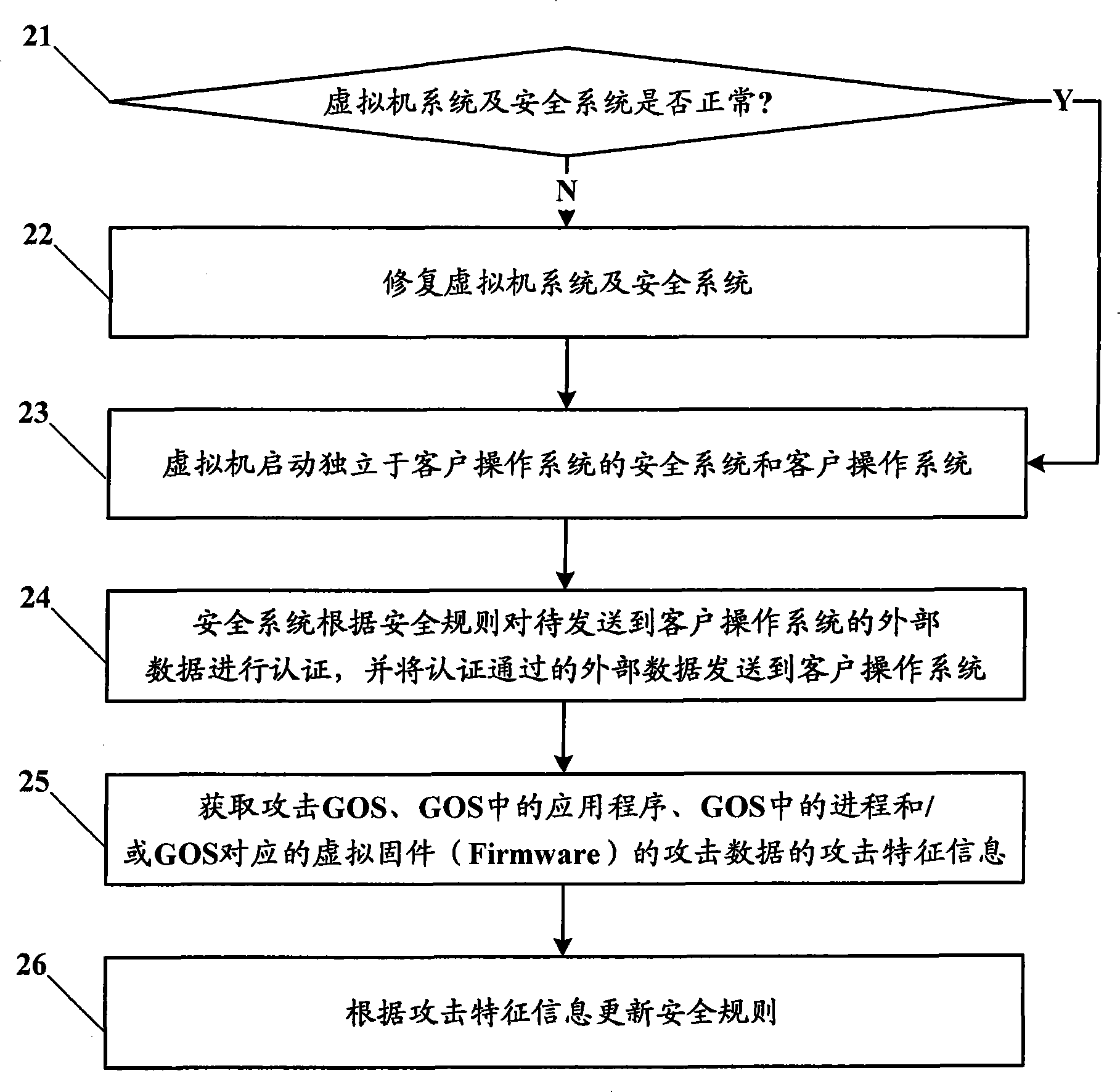
[0081] In the embodiment of the present invention, by setting up a security system independent of the client operating system, the security subsystem verifies the externally input data, and sends the verified data to the client operating system, so as to realize safe data communication.
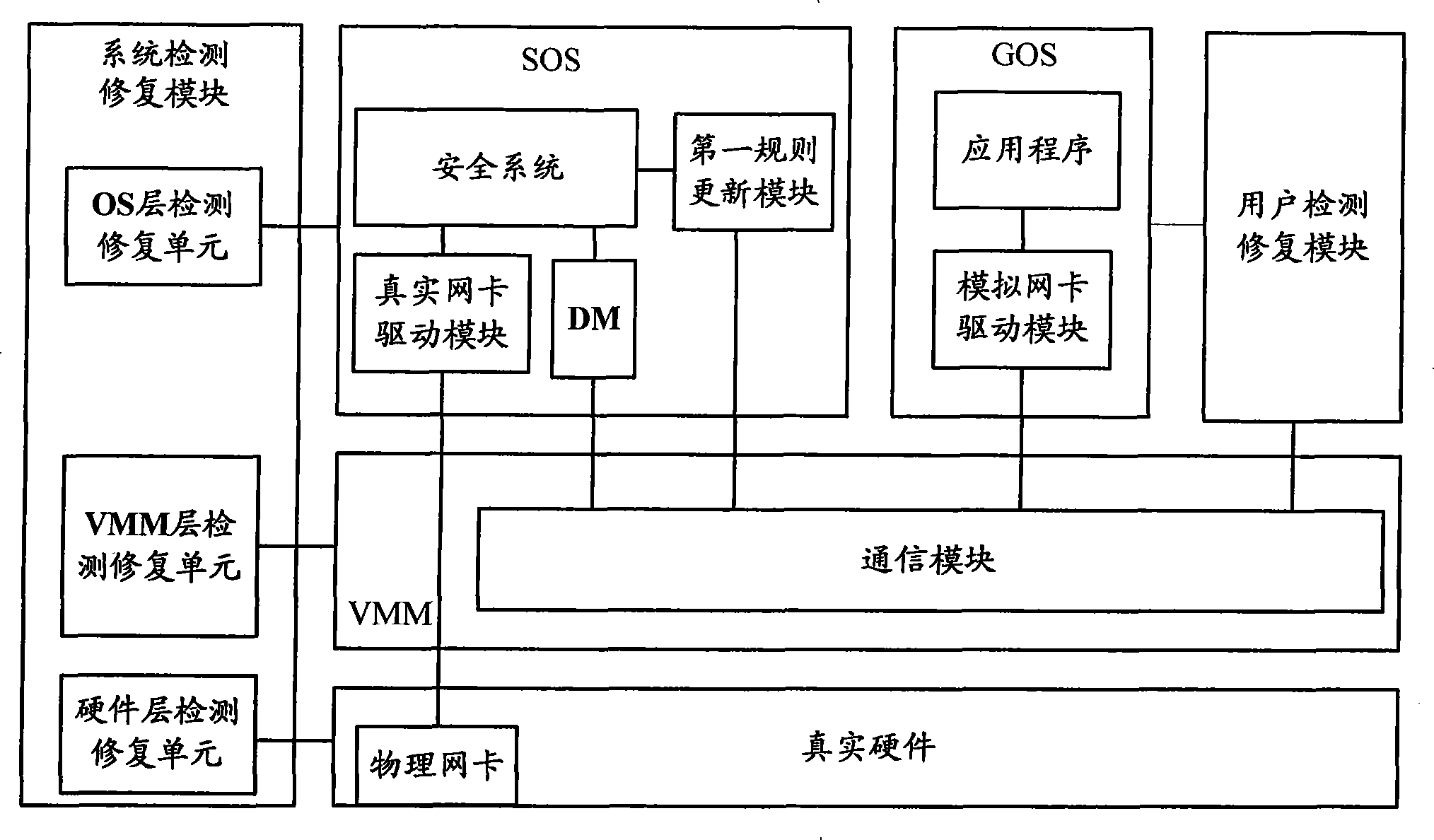
[0082] The computer system of the embodiment of the present invention is as figure 1 As shown, it includes a guest operating system GOS (GuestOperation System), a service operating system SOS (Service Operation System), a virtual machine monitor VMM (Virtual Machine Monitor) and a user system detection module, wherein:
[0083] A communication module is set in the VMM;
[0084] The settings in SOS are:
[0085] Real network driver, data interaction with physical network card, receiving data transmitted by physical network card;
[0086] Device model DM (Device Module), used to provide virtual network card for GOS;
[0087] The settings in GOS are:
[0088] The virtual network card is use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com