Obfuscating computer program code
A computer program and computer technology, applied in the field of tampering protection of computer program code, can solve problems such as complex tasks, program code confusion, and difficulty in analyzing programs, and achieve the effects of improving complexity, efficient methods, and promoting recovery.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
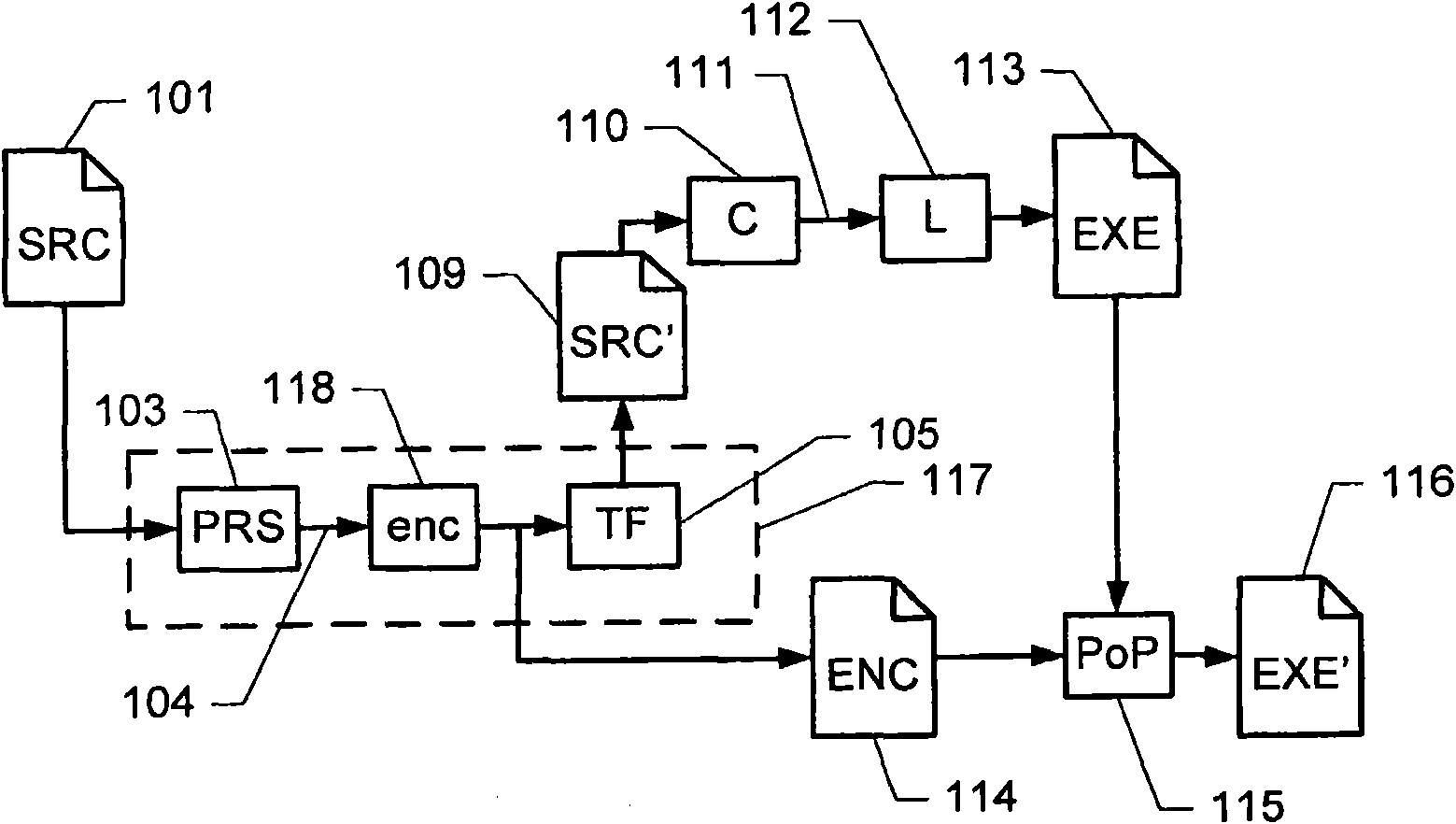
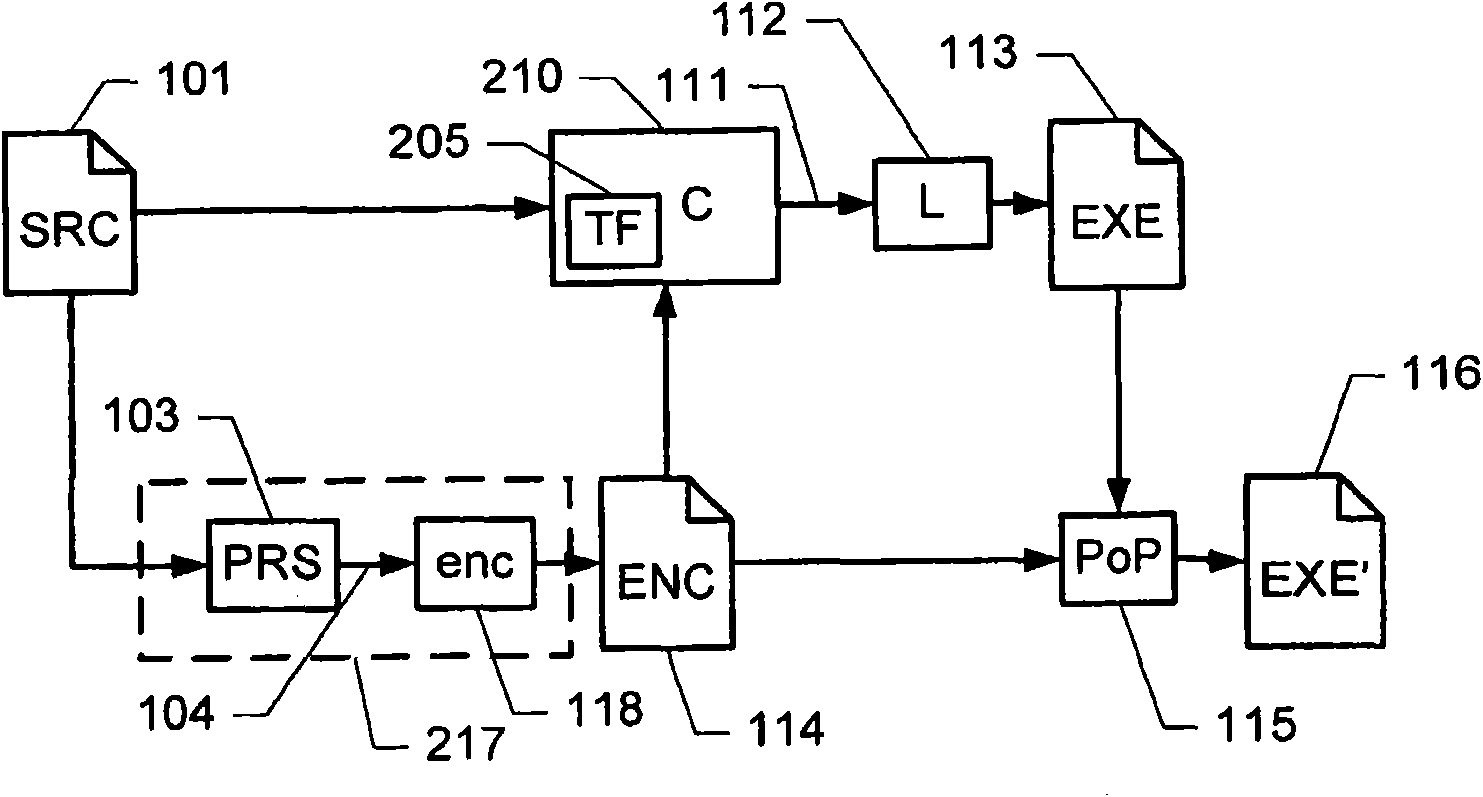
[0075] figure 1 A schematic block diagram showing an example of a process for tampering protection of program code. In particular, figure 1 Illustrates the workflow when building software components.
[0076] The process receives source code 101. Typically, the source code 101 uses a computer program in which a programmer has already written, usually in the form of a formal programming language such as C, C++, Java, etc. The source code can be automatically compiled by a compiler into object code or machine code or executed by an interpreter. The source code 101 may be represented as one or more text documents, or as any other suitable digital representation. Alternatively, the tamper protection process may receive different types of input representations in which function calls can be recognized, such as object codes.
[0077] The source code 101 is fed into the parser module 103. The parser module parses the source code and identifies one or more function calls in the source ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com