Method and system for compiling network security audit strategy
A network security and editing system technology, applied in the field of computer network security, can solve the problems of poor policy reusability, difficult integration of other systems, and single operation mode of policy definition, and achieves easy deployment, simplified formulation process, and convenient policy. The effect of transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
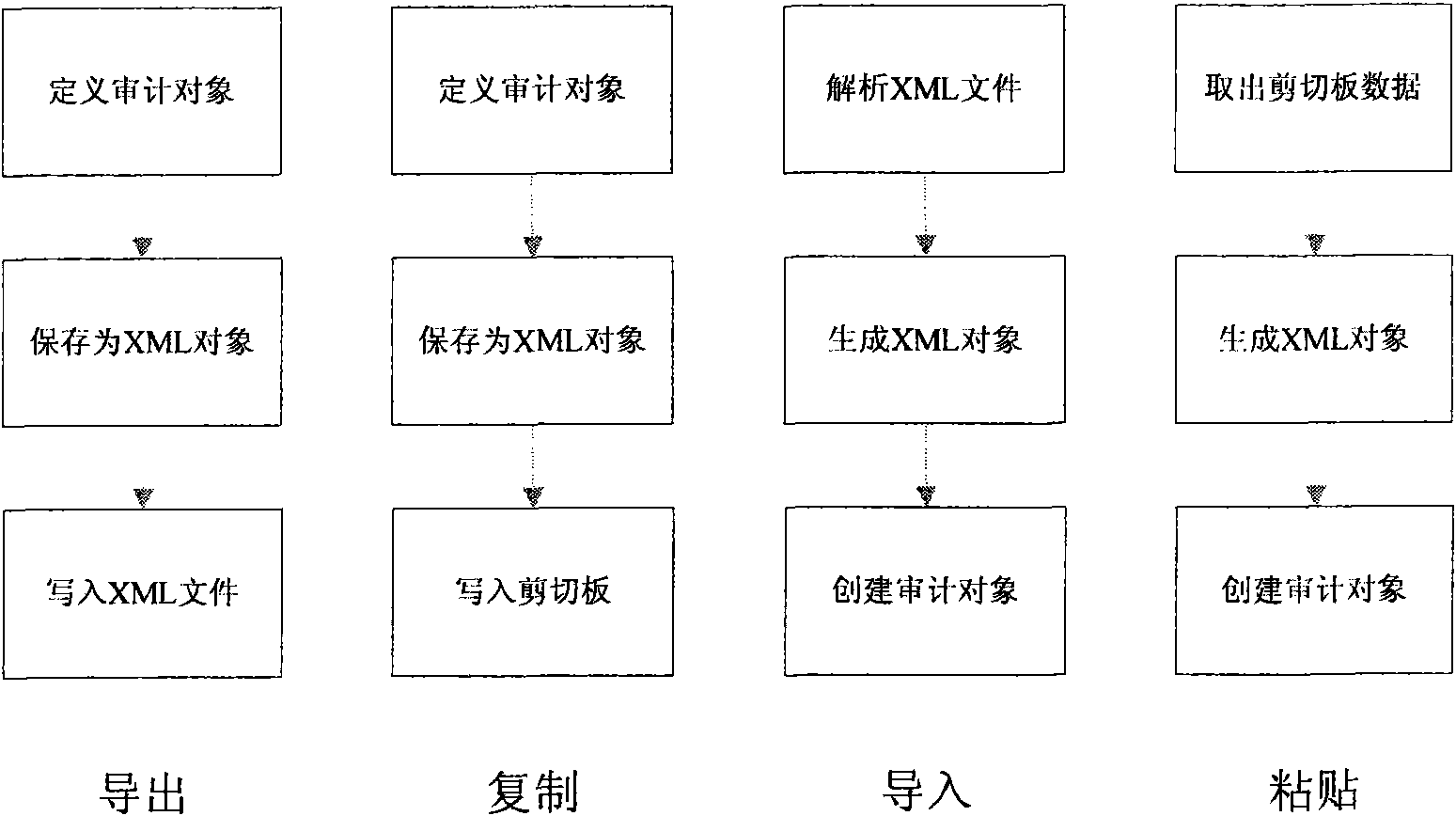
[0026] Embodiment 1: We describe the entire implementation process of a policy editing method for network security auditing according to the present invention in combination with specific embodiments. Such as image 3 A flow chart of a network security audit policy editing method shown, which includes the following steps:
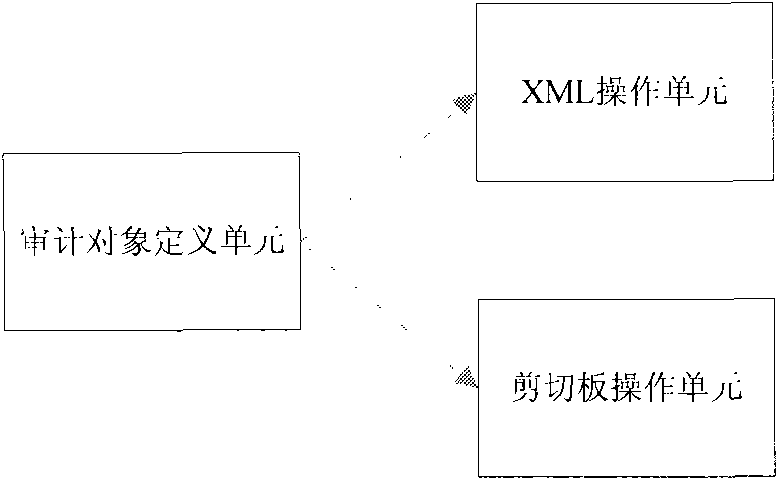
[0027] Step 1 defines data information such as protection host, protection service, role and access rules according to the logical relationship of "role accessing host's service to perform specific operations", and saves it in the database as an audit object; the "role accessing host's service The logical relationship of performing specific operations" is reflected in which service objects are included in the host object, which specifically indicates what services the host provides, or which services of the host need to be audited. The role that needs to access the service is defined under the service object, and the access operation of the role is defined...
Embodiment 2
[0043] Embodiment 2: Below in conjunction with concrete data, embodiment 1 is described further.
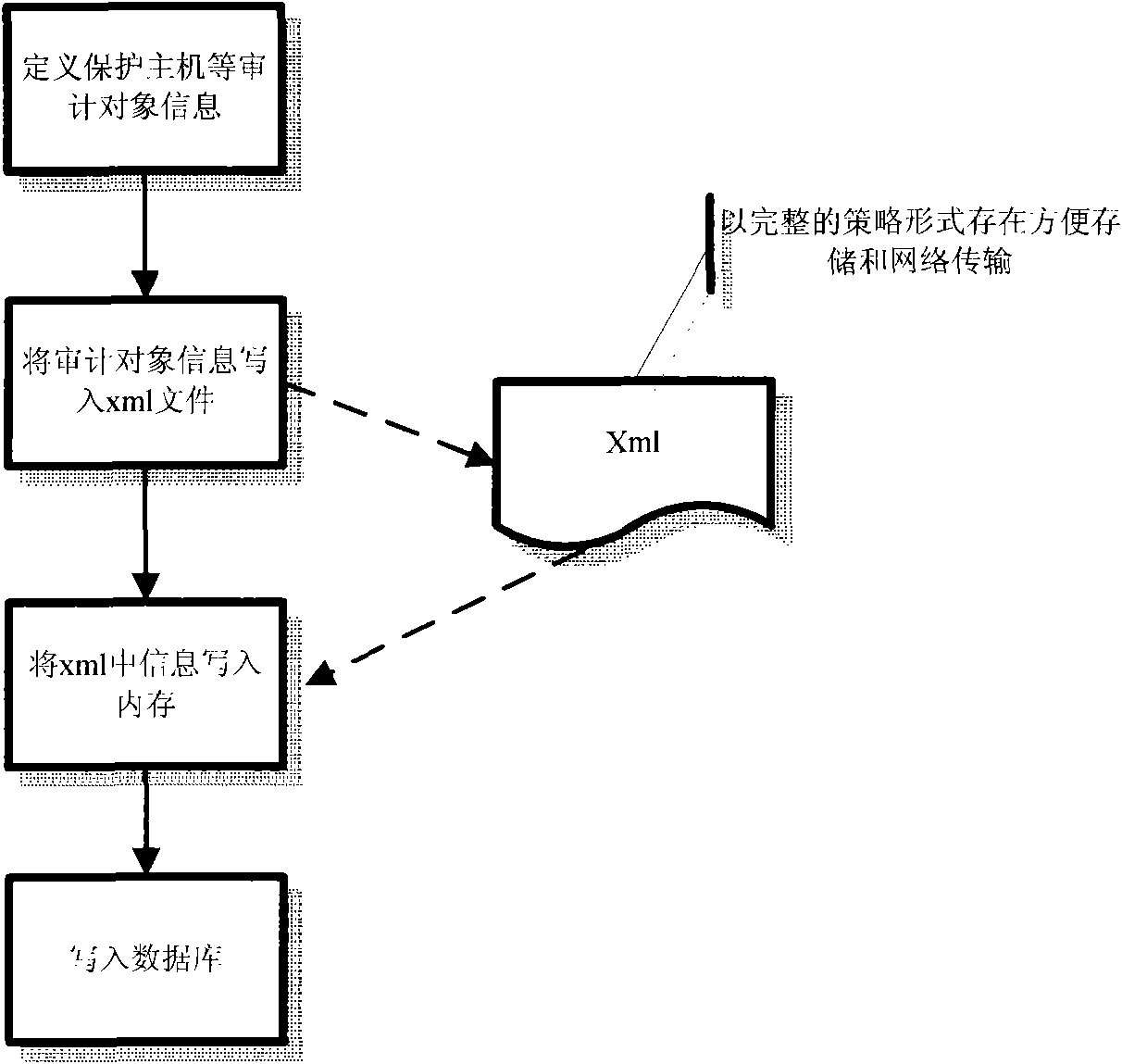
[0044] First of all, suppose we have a business host, which mainly provides telnet service, and now we need to audit the operation behavior of users accessing the business host. Audit rules can be defined in this way. First, define the host object. We name the host object Server101; ID is the unique identifier of the host object, and the value is 001; the IP address of the host object is 192.168.30.101; The value is 1; of course, the service object can also be defined as a subnet.
[0045] Then define the service, here the service is defined as Telnet; there is also an ID, the value is 001; the service also has a port number, the port number of the telnet protocol is 23.
[0046]Next, define the role Role, which mainly determines the action of the audit engine after the operation rules are matched. Here we define the alarm mode as: 1 means alarm; log level: 1, means intermediate...
Embodiment 3
[0062] Example 3: figure 1 It is a flowchart of a policy editing method for a network security audit according to the present invention, as shown in the figure, according to an embodiment of the present invention, firstly define the audit object information such as the protection host; then use XML as a medium to write the audit object into XML file to realize the export operation; and then write the XML file into the memory database to realize the import operation. In this embodiment, the XML exists in the form of a complete policy, which is convenient for storage and network transmission.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com