Key management method for multicast
A management method and multicast key technology, applied in the field of computer network applications, can solve problems such as difficult implementation and expansion, and achieve the effects of easy implementation and deployment, good communication overhead and security, and good storage overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
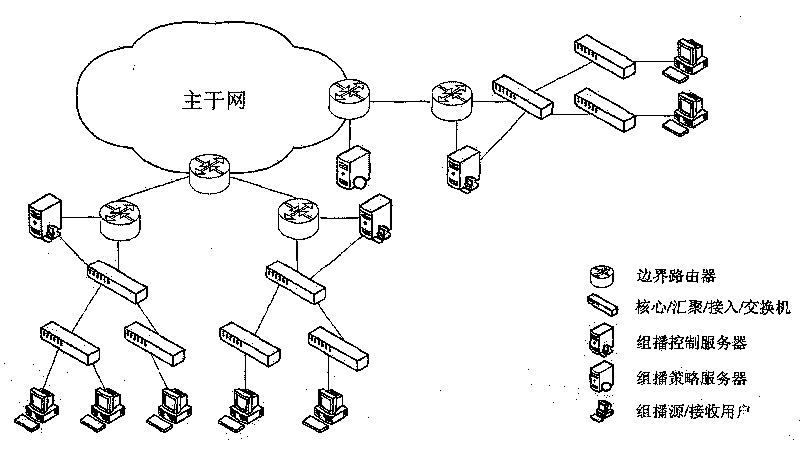
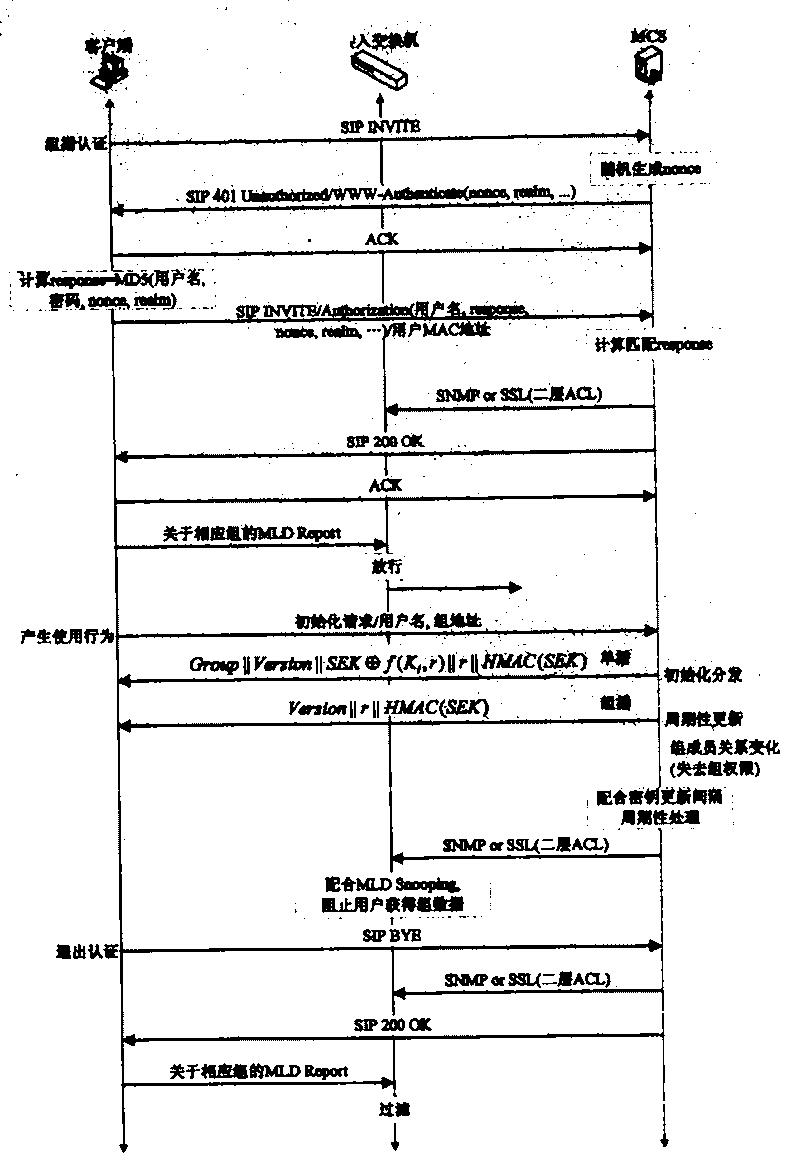
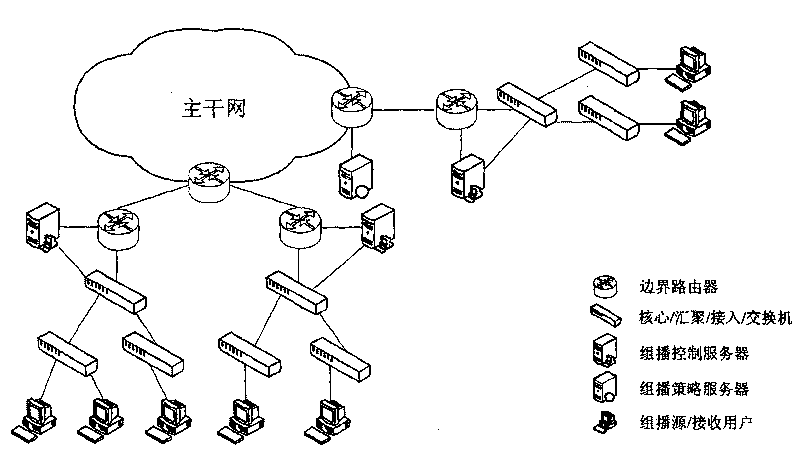
[0058] The present invention provides a complete set of multicast key management schemes, including multicast authentication, Layer 2 access control list ACL configuration, group key generation, key distribution triggered by group member initialization, group membership changes (users obtain / Loss of access to the group) triggers rekeying and rekeying when a timer expires. The invention proposes a multicast authentication method based on the session initialization protocol SIP to authenticate the user's multicast authority; through the simple network management protocol SNMP or the secure socket layer SSL interface, the access switch is configured with a two-layer ACL to realize The message filtering function of the multicast listener discovery protocol MLD has finely controlled the group members from the access switch port. On this basis, the present invention proposes a set of key distribution and update schemes, combined with the multicast listener discovery protocol of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com