CC (Communication Center) attack protective method and system thereof
A legal, pre-set time technology, applied in the field of network security, can solve problems such as difficult protection systems and affecting domain name access, and achieve the effect of improving protection capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] In order to describe the purpose and technical solution of the present invention in more detail, the present invention will be further described below in conjunction with the accompanying drawings.
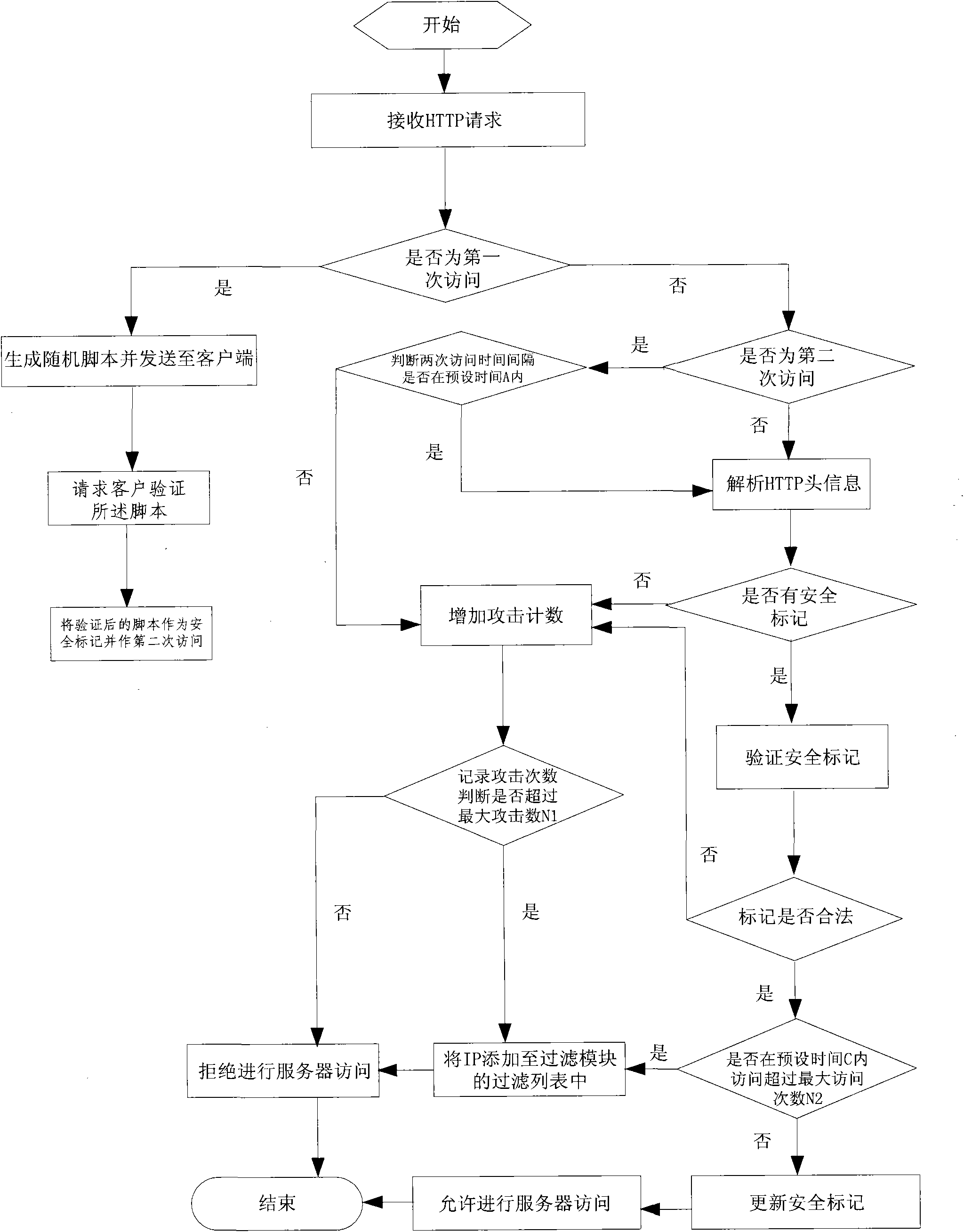
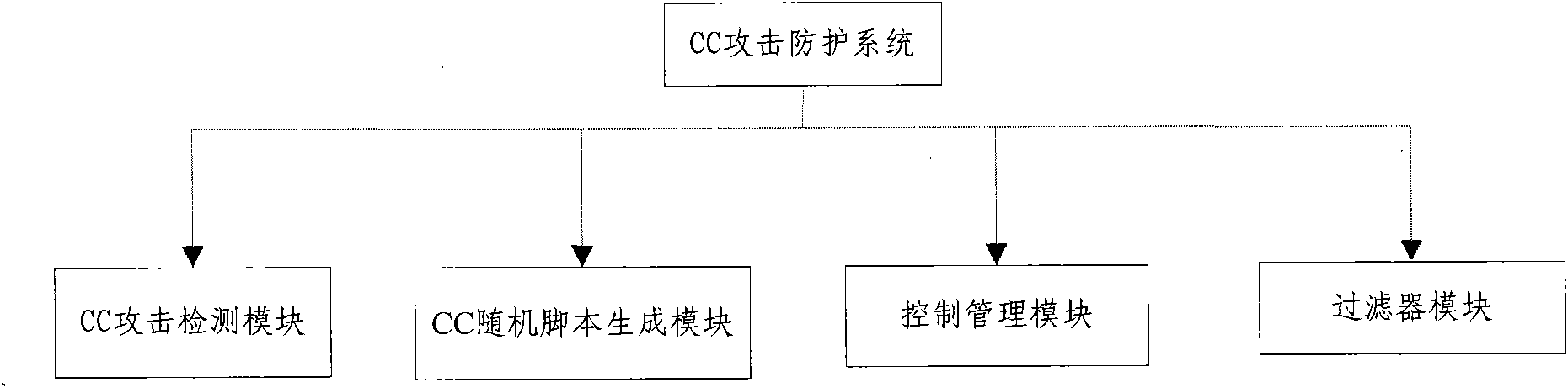
[0033] The following is attached figure 1 The CC attack protection method of the present invention and the modules of the system for completing each step of the method are described.
[0034] Step 1: Set the corresponding working parameters by controlling the management module, the WEB server receives the HTTP request, and the CC attack detection module judges whether the visiting IP is the first visit.
[0035] Step 2-1: If it is the first visit, the CC random script generation module generates a client script and sends it to the client, requests the client to verify the script, and uses the verified script as a security token for the second visit .
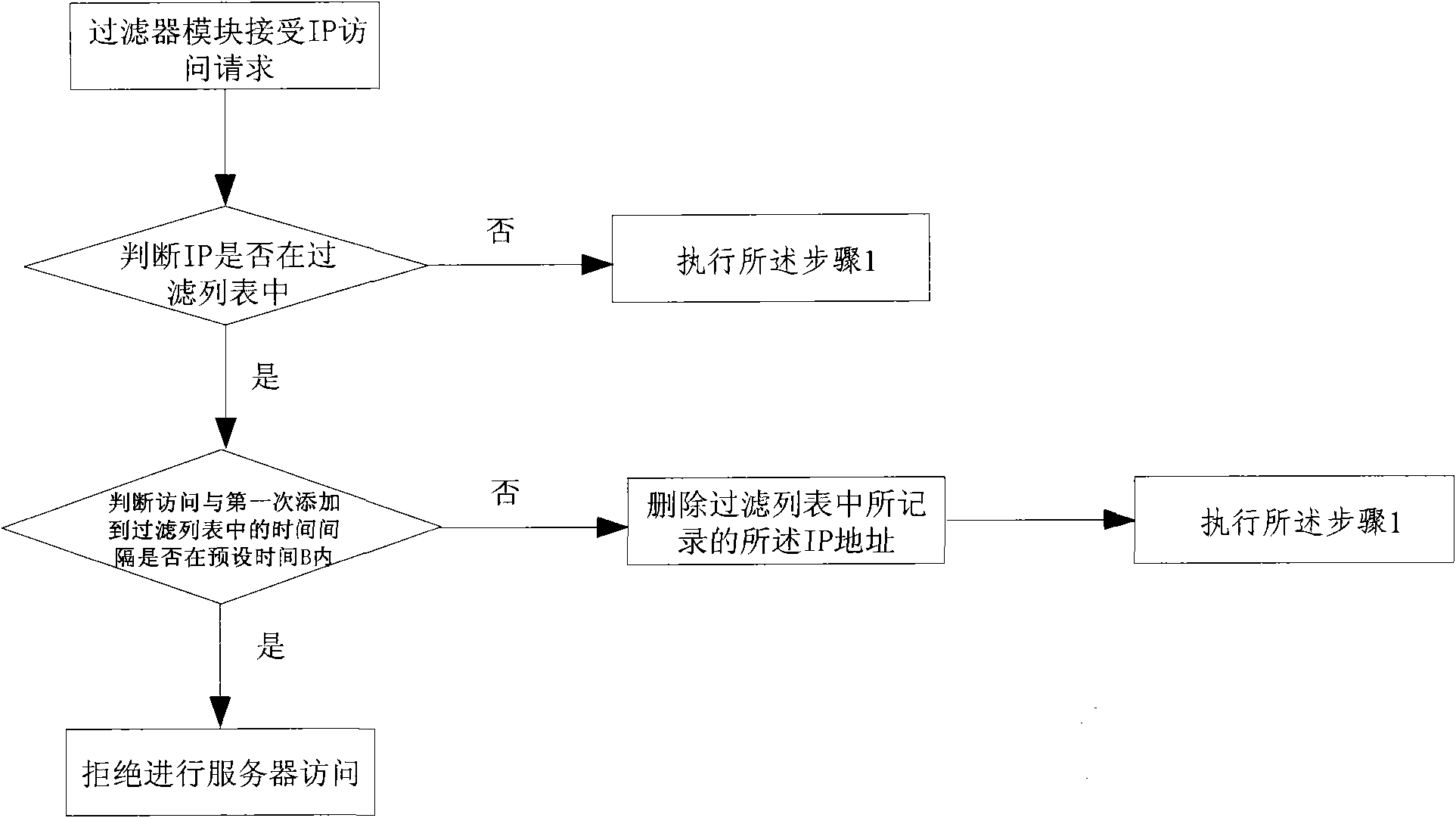
[0036] Step 2-2: If it is not the first visit, the CC attack detection module judges whether it is the second visit; if i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com