RFID (Radio Frequency Identification) triple safety certification method based on label ID (Identification) random division
A security authentication and re-authentication technology, applied in the field of RFID air interface security, can solve problems such as single authentication mode and security risks, and achieve the effect of anonymity and forward untraceability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] 1. RFID system initialization
[0038] When the RFID system is initialized, each tag and reader has a unique identifier ID T and ID R ; The database has all tags and identifiers of readers; tags, readers and background databases have a secret shared key K. In this system, the backward communication link from the reader to the background database is considered safe.
[0039] 2. Certification process
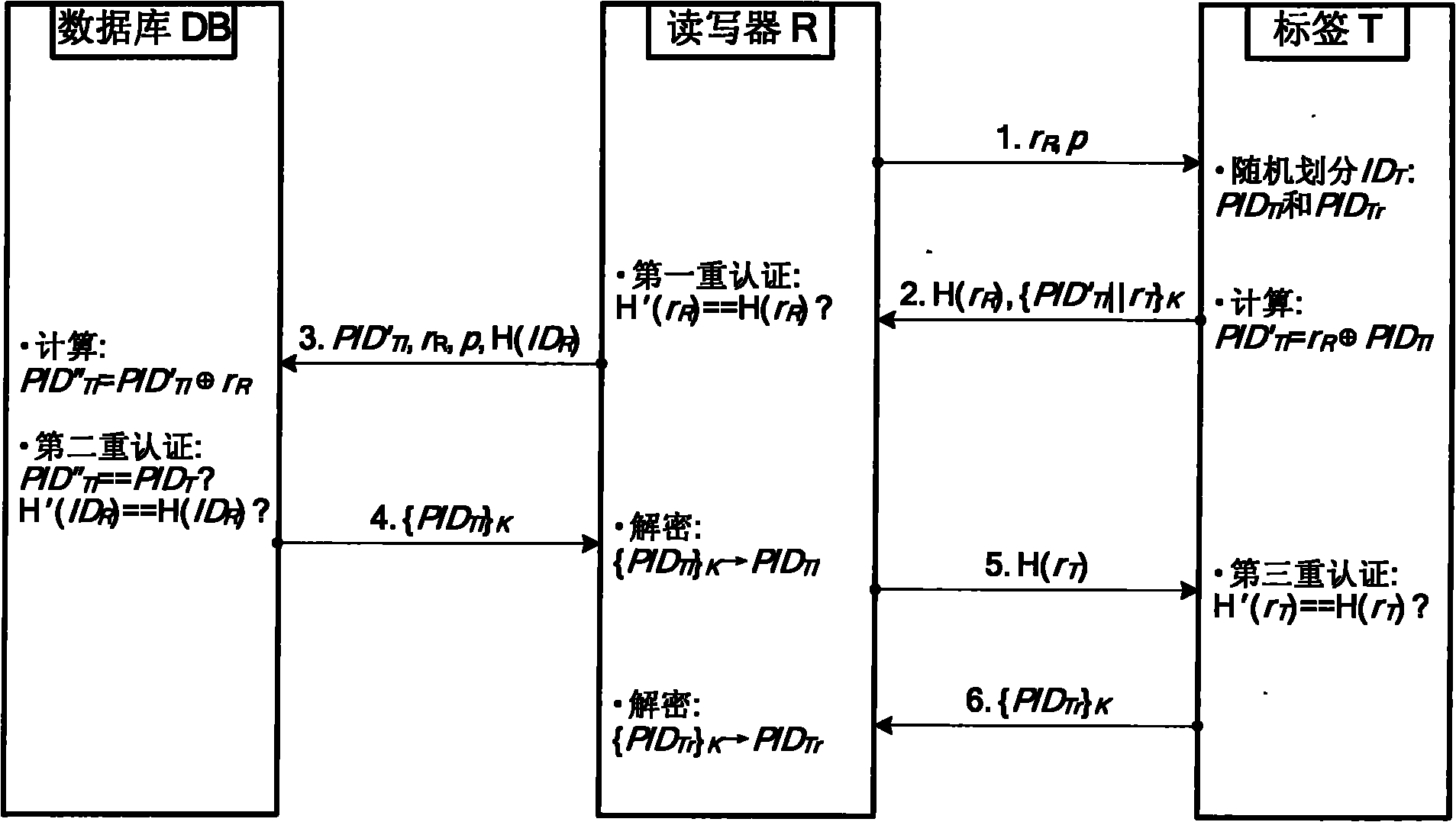
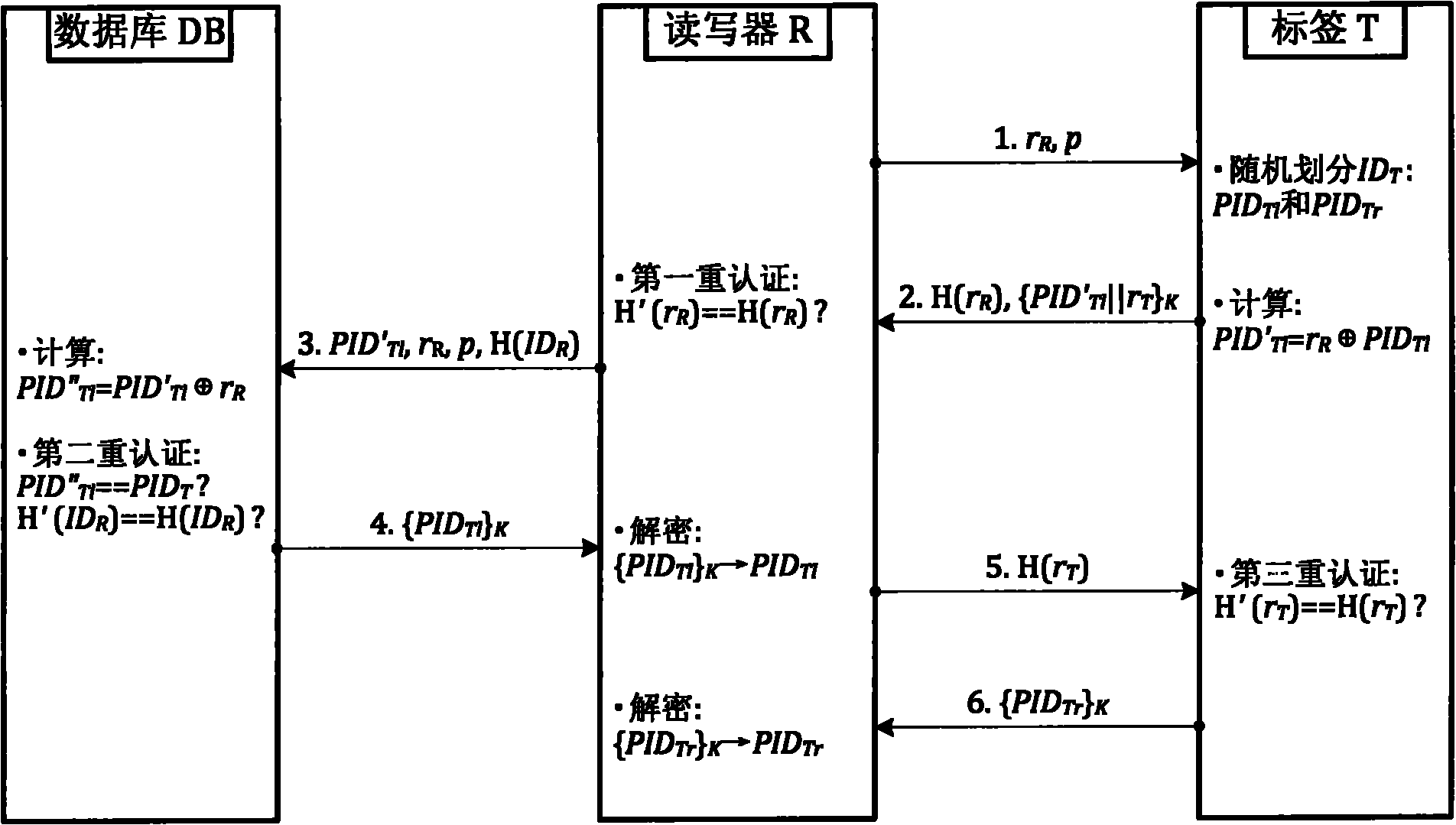
[0040] RFID system security authentication protocol such as figure 1 As shown, the authentication steps are as follows:
[0041] (1) Reader query request: the reader R first generates two random numbers r R and p, and r R and p are sent to tag T as an inquiry request;
[0042] (2) The tag ID is randomly divided: after the tag T receives the request, it R Perform Hash operation to get H(r R ). At the same time, the tag T sends its own identifier ID T Randomly divide into left identifiers and the right identifier Two parts (of which, with The division of i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com