Method for realizing fuzzing of software on the basis of state protocol
A technology for protocol implementation and fuzz testing, which is applied in software testing/debugging, instrumentation, electrical digital data processing, etc., can solve the problems of insufficient state protocol support, low test coverage, poor test efficiency, etc., and achieve the goal of improving test coverage Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
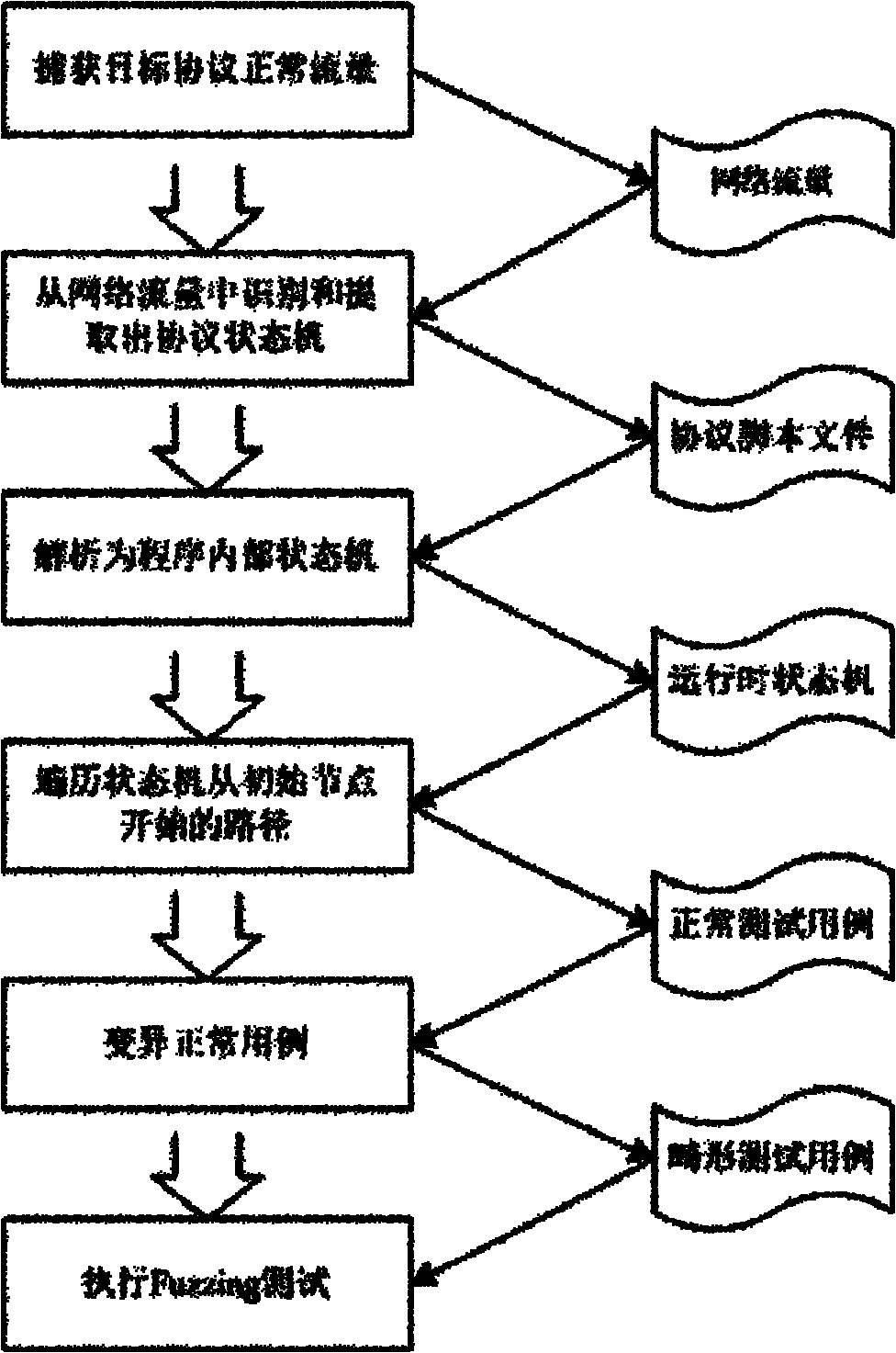
[0038] The specific implementation manner of the present invention will be described in more detail below in conjunction with the accompanying drawings.
[0039] Step 1), capture the target state protocol to realize the normal interaction flow of the software.
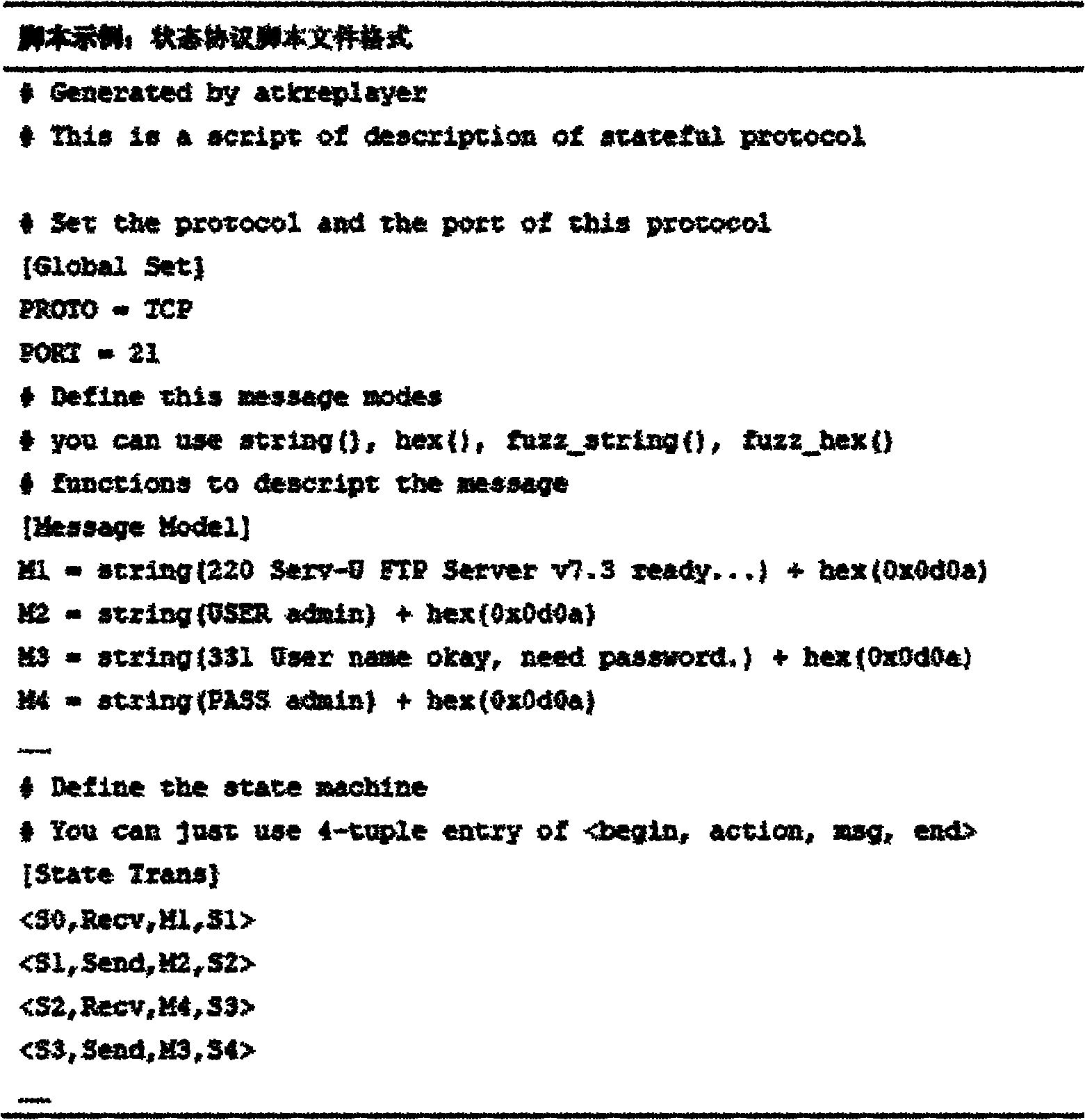
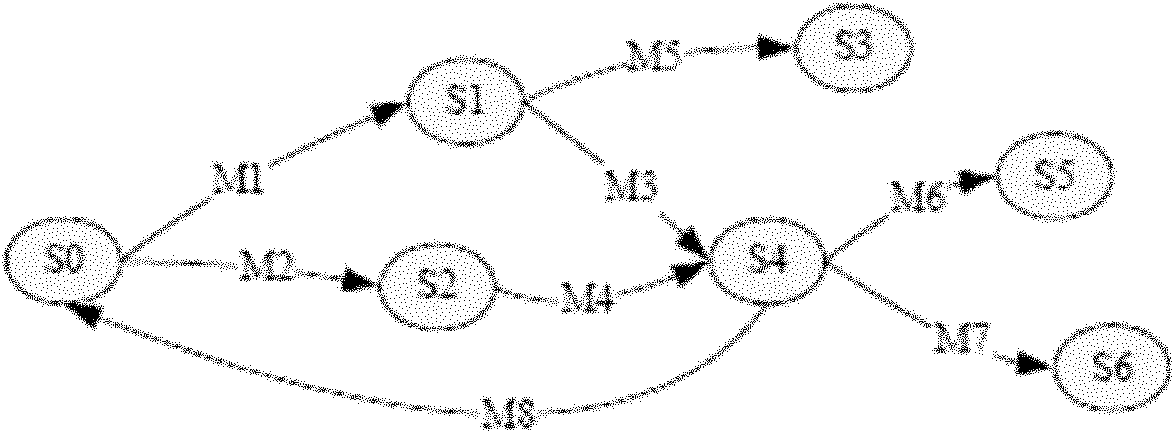
[0040] The status protocol includes network protocols such as FTP and SIP. This embodiment takes the fuzzy test of the FTP server as an example to illustrate the method of the present invention.
[0041] 1.1) Install the normal functional environment of the target program. Enable the FTP server and FTP client to communicate normally, and ensure the normal use of FTP functions such as login, view, download, and upload;
[0042] 1.2) Turn on the network sniffing and packet capture tools, and prepare to capture the normal communication traffic of the target program. Currently commonly used packet capture tools include Wireshark, Tcpdump, etc. These tools can accurately capture network packets of specified interfaces and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com