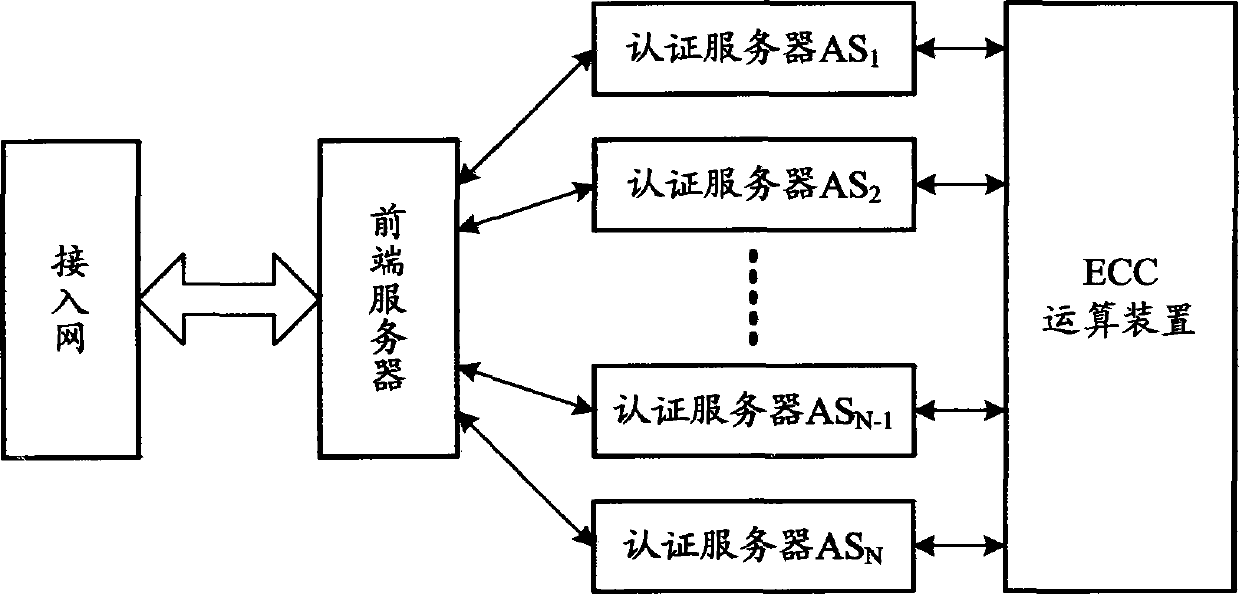
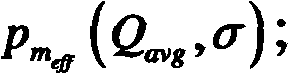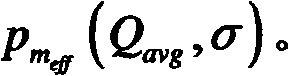Realizing method of elliptic curve cryptography arithmetic device in authentication system
An elliptic curve cryptography and authentication system technology, applied in the field of secure access to wireless communication systems, can solve problems such as increasing the cost of system deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0156] The technical scheme of optimizing the parameter set (L=h; m=M) of the ECC computing device can be designed as follows:
[0157] Firstly, the DSP kernel in the system is divided into L operation unit groups. It is assumed that these groups of operation units can use different parameters m, where the number of divisions of each dot multiplication operation unit is marked as m l , l=1, 2,..., L, they form a set M={m l |l=1, 2, ..., h}.
[0158] Define the number of equivalent segments as m l The mathematical expectation of :
[0159] m eff = E ( m l ) = Σ l m l L ,
[0160] For L dot multiplication units, it can be constructed Combinations, select several combinations correspond...
Embodiment 2
[0180] Embodiment 2 is to embodiment 1 when m eff It is an integer, that is, for the same parameter group, it is divided into L operation unit groups, and the segment number m of each operation unit group is all the same. According to the agreement, the parameter group (L=h; m=M) can be abbreviated as ( L=h; m=m 0 ), where m 0 = m 1 = m 2 =…=m L .
[0181] To the parameter group (L=h; m=m of ECC computing device 0 ) to optimize the technical scheme can be designed as follows:
[0182] For the given system parameter nT and other necessary explanations, a mathematical model is established for the system, and then the simulation is carried out by the Monte Carlo method according to the different conditions of m∈M, respectively according to the specified Q avg and σ parameters to generate authentication request input samples, and then simulate the concurrent processing process and strategy of the input samples by the DSP core, and obtain the timeout probability p of authent...
Embodiment 3
[0201] Embodiment 3 is a special case of Embodiment 2. When the authentication server system works under light load conditions, for example, the number of authentication requests waiting is less than the preset threshold value Q th , a reasonable assumption can be made at this point: the timeout probability of authentication request processing p≈0. Under this condition, for the parameter set (L=h; m=m 0 ) The optimized technical scheme can also be designed as follows:
[0202] According to the simulation analysis and combined with engineering experience, the following parameter constants are determined: q 1 ,q 2 ,q 3 ,q 4 , and its unit is the number of authentication requests / second. These constants should satisfy the condition: q 1 2 3 4 th . Record and calculate the average number of authentication requests Q received by the authentication server system per second in a pre-designed statistical period (such as 60 minutes) avg , and then according to the attached Fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com