Security strategy decomposition and verification system in cloud storage environment
A security strategy and cloud storage technology, applied in transmission systems, electrical components, etc., can solve problems such as single point failure, network congestion, and heavy server load, and achieve the effects of reducing communication overhead, avoiding excessive load, and ensuring convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Below in conjunction with accompanying drawing and example the present invention is described in further detail.
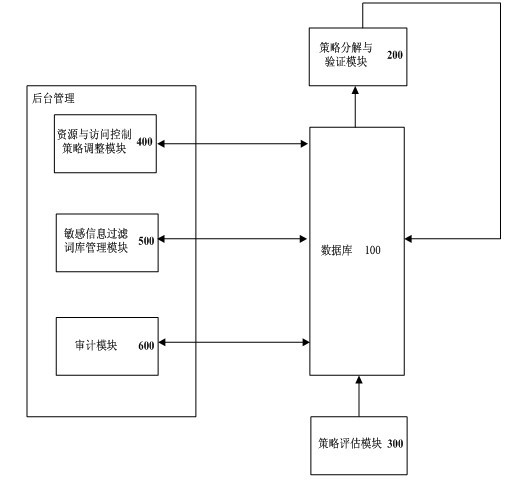
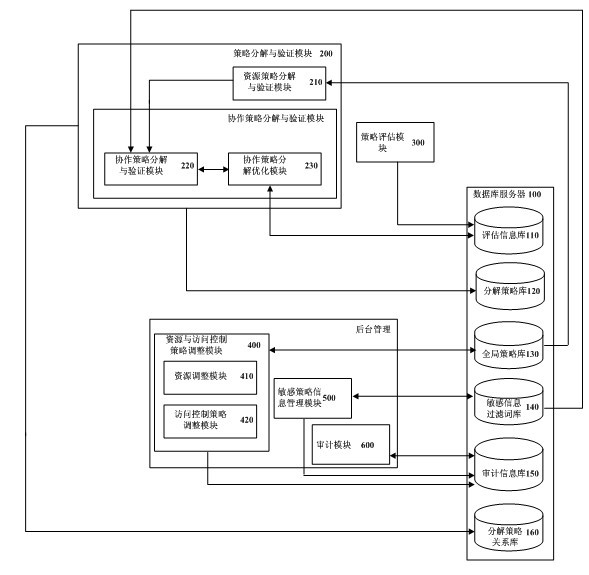
[0026] like figure 1 As shown, the functions of the system of the present invention can be divided into: policy decomposition and verification, policy evaluation and background management, the system includes a database 100, a policy decomposition and verification module 200, a policy evaluation module 300, a resource and access control policy adjustment module 400, Sensitive information filtering lexicon management module 500 and audit module 600 .
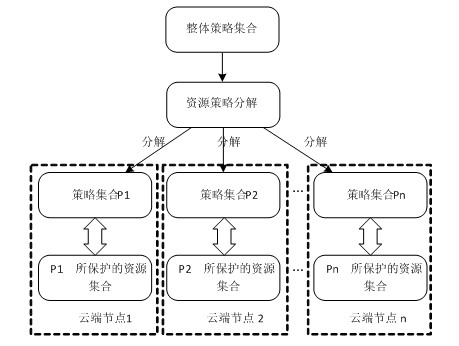
[0027] The database 100 is used to store the global access control policy for implementing access control by the system, the decomposed policy based on resource distribution characteristics, and the encrypted information on the relationship between policies obtained based on the sensitive information filtering lexicon, and store evaluation information to guide and optimize the strategy decomposition process a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com