File access filtering method
A filtering method and file access technology, applied in the field of network security, can solve the problems of decreased efficiency, consumption of memory and CPU resources, and illegal operations without recording files, so as to improve the speed and speed up the comparison efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The specific implementation manners of the present invention will be described in further detail below in conjunction with the accompanying drawings and examples. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
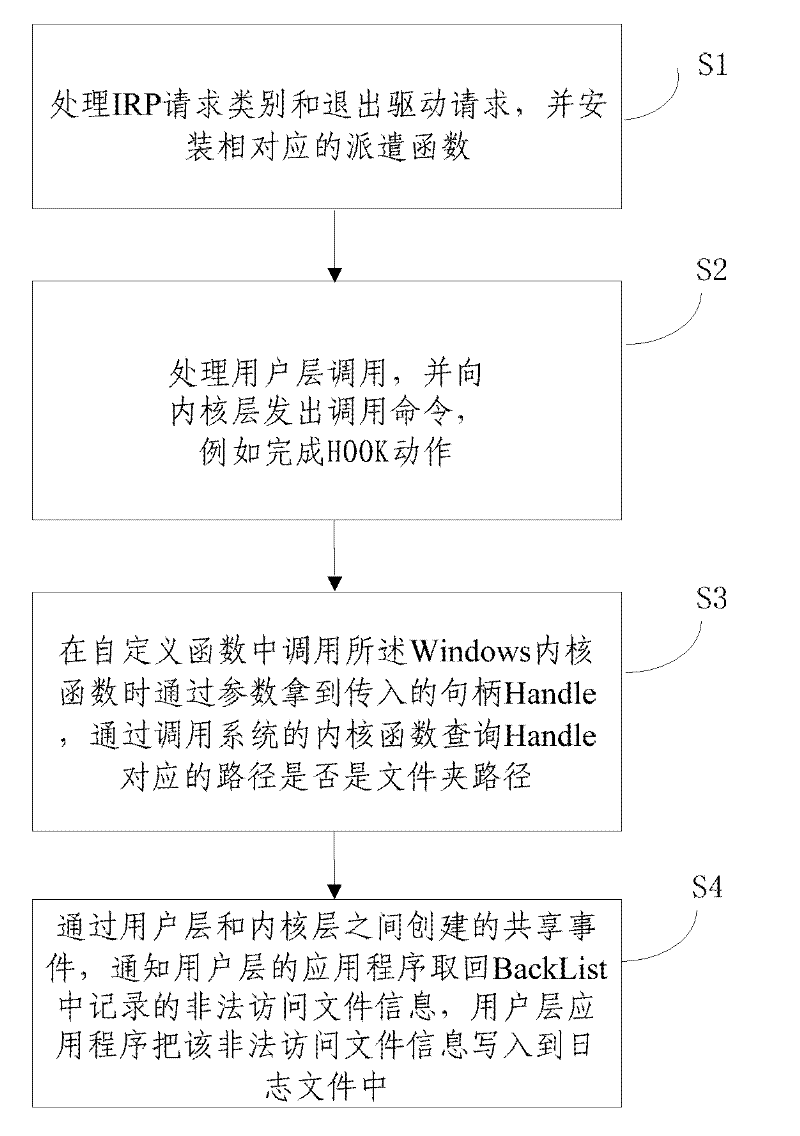
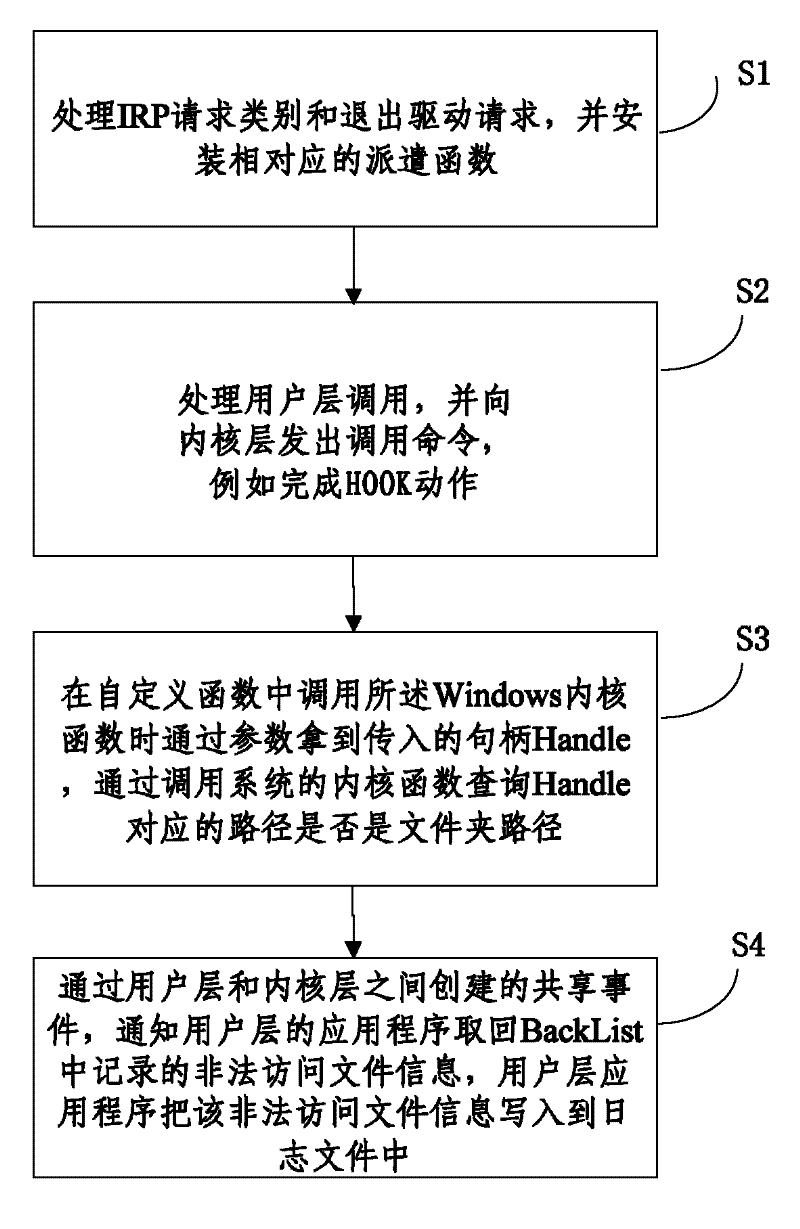
[0022] Such as figure 1 As shown, the file access filtering method of the present invention comprises the following steps:
[0023] S1, process the I / O request packet IRP request category and exit the driver request DriverUnload, and install the corresponding dispatch function;
[0024] S2, process the user layer call, and send a call command to the kernel layer, for example: when the user layer sends a start command, the kernel layer starts to search for the address of the Windows kernel function ZwCreateFile in the system service description table SSDT, and converts this address into a custom The address of the function MyCreateFile, so as to complete the HOOK action;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com