A Method for Encrypting Executable Files When the Software Source Code Is Unknown
A technology for executing files and encryption methods, which is applied in the fields of instruments, computing, electrical digital data processing, etc., to achieve the effect of simple implementation, reducing the difficulty of encryption, and reducing infringement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0038] A method for encrypting an executable file when the software source code is unknown, comprising the following steps:
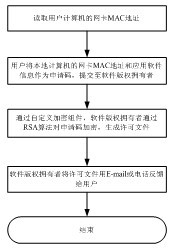
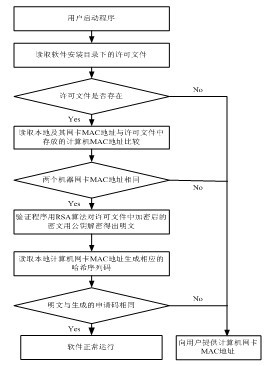
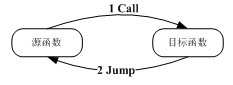
[0039] Step 1, start the executable file that has been injected into the custom dynamic link library; the specific method of injecting the custom dynamic link library into the executable file is as follows: image 3It is the process of injecting dynamic link library. In this process, before the dynamic link library is injected, the source function execution process can directly call the target function (as shown by arrow 1), and after the execution of the target function is completed, the source function can be directly returned (as shown by arrow 2). The selected target function is intercepted through the API HOOK technology, and the target function has the characteristic of being executed during the running of the program and only executed once. Inject a custom dynamic link library before the execution of the target function, and the user-defined use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com