MAC (Media Access Control) address table access control method, as well as apparatus and network device for the same
A technology of MAC address table and MAC address, applied in the field of network communication, can solve the problems of affecting device performance, small capacity of hardware MAC address table, low packet forwarding speed and efficiency, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
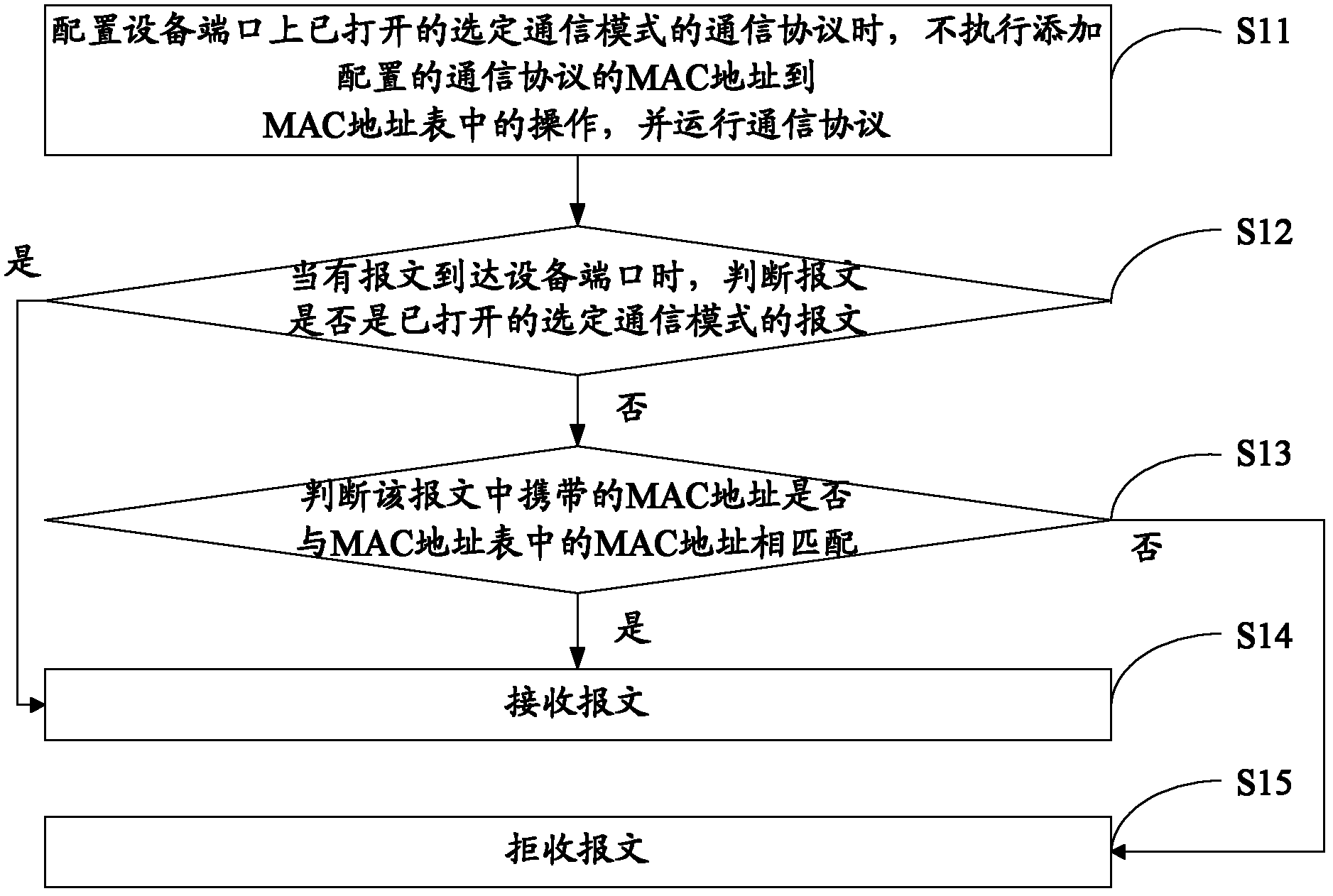
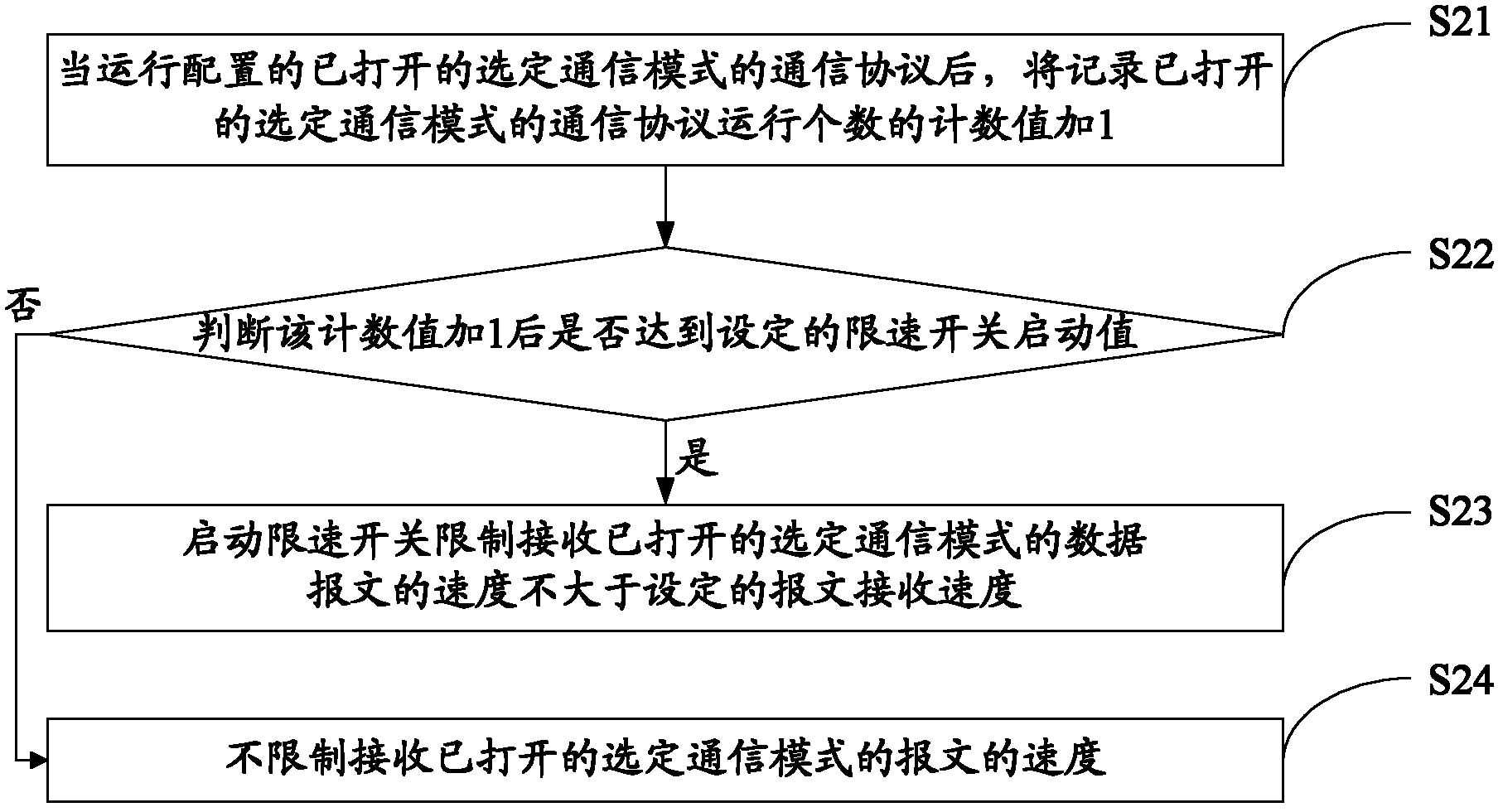
[0102]In this embodiment, the configuration communication protocol is used as an example to illustrate the specific process of the MAC address table access control method. The specific steps are as follows: Image 6 Shown:
[0103] Step S501: Monitor the number of MAC addresses in the software MAC address table.
[0104] Step S502: Determine whether the number of MAC addresses in the software MAC address table is greater than the capacity of the hardware MAC address table, if yes, execute step S503; otherwise, execute step S501.
[0105] Step S503: Count the number of MAC addresses in each communication mode in the software MAC address table; set the communication mode with the largest number of MAC addresses as the selected communication mode.
[0106] When the communication mode with the largest number of MAC addresses is one, the selected communication mode is one; when the communication mode with the largest number of MAC addresses is two, the selected communication mode ...
Embodiment 2
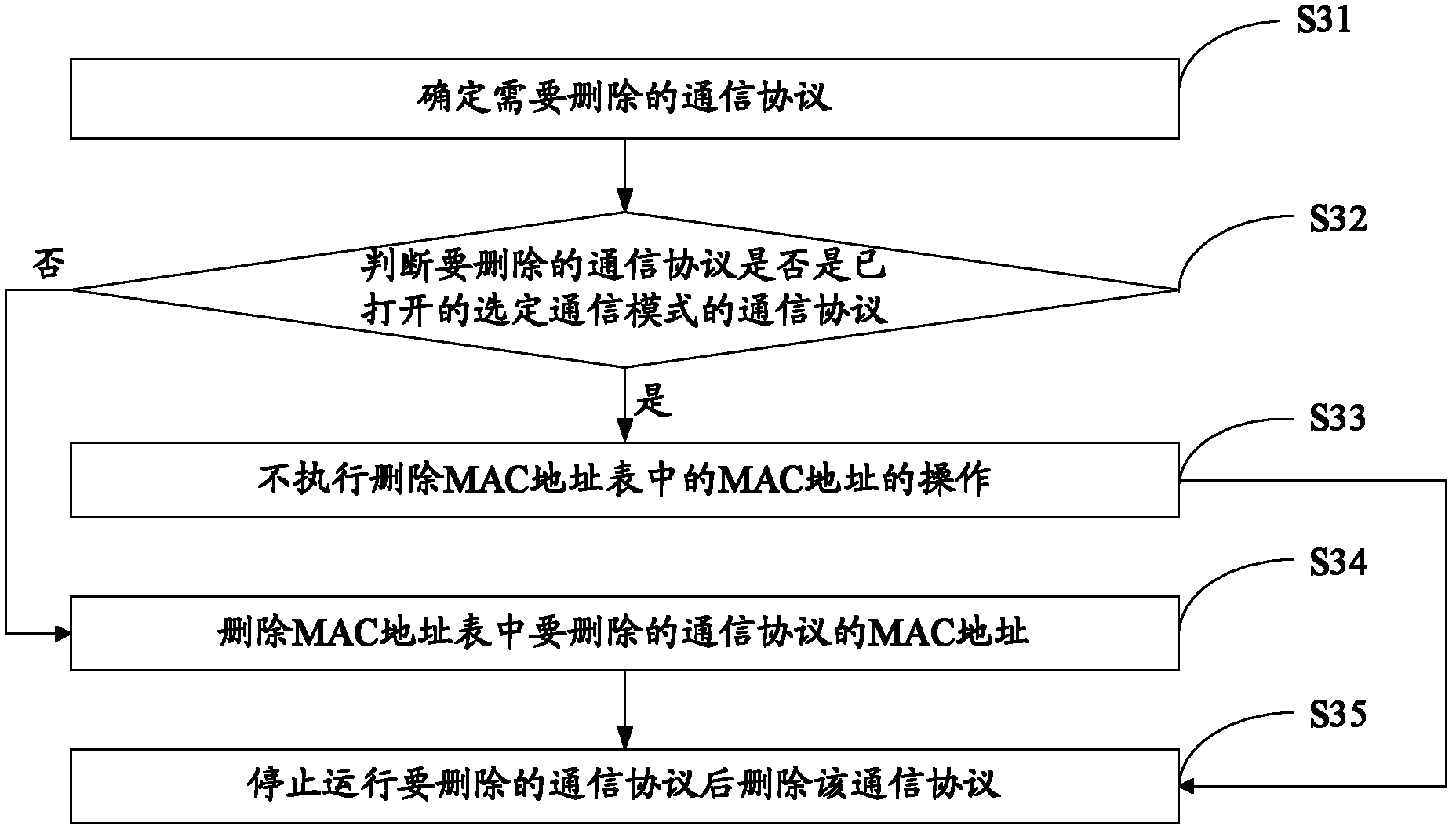
[0121] In this embodiment, the specific flow of the MAC address table access control method is described by taking the deletion of the communication protocol as an example. The specific steps are as follows: Figure 7 Shown:
[0122] Step S601: Determine the communication protocol that needs to be deleted.
[0123] Step S602: Determine whether the communication protocol to be deleted is the communication protocol of the selected communication mode that has been turned on, and if so, perform step S603; otherwise, perform step S604.
[0124] Step S603: Execute step S609 without performing the operation of deleting the MAC address in the MAC address table.
[0125] Step S604: Delete the MAC address of the communication protocol to be deleted configured in the MAC address table, and execute step S605.
[0126] Step S605: Monitor the number of MAC addresses in the software MAC address table.
[0127] Step S606: Determine whether the number of MAC addresses in the software MAC ad...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com