Digital certificate revocation method and equipment
A digital certificate and digital technology, applied in the field of network security, can solve the problems of digital certificate revocation, network security hidden dangers, etc., and achieve the effect of ensuring security, user information security, and revocation process directly and quickly
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
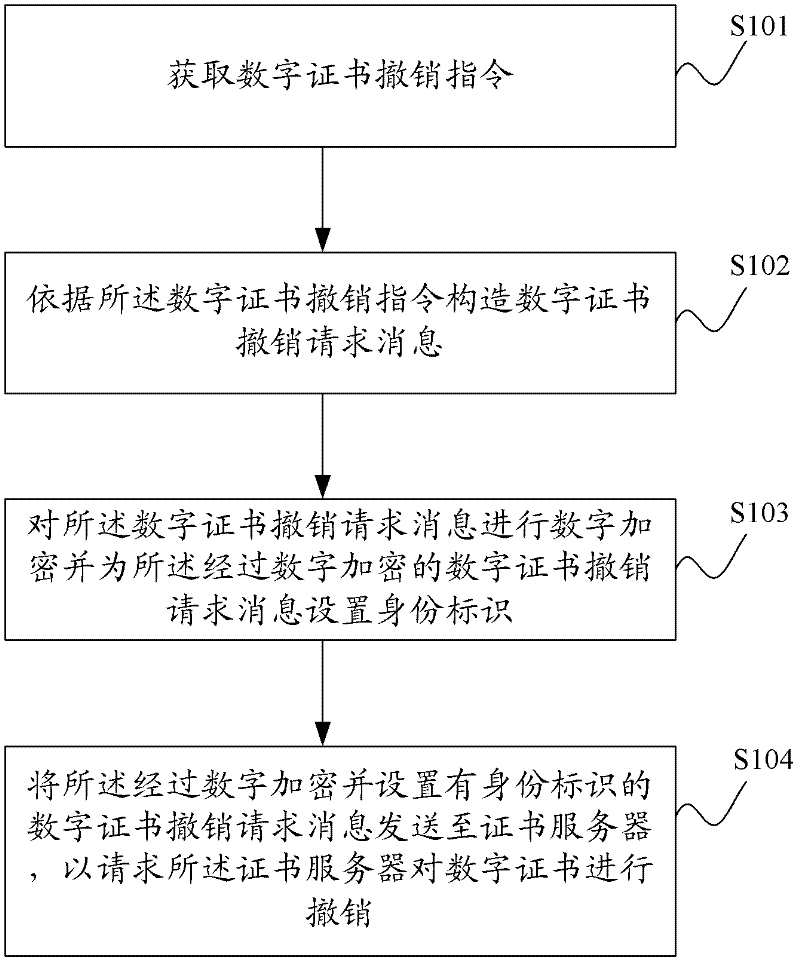
[0045] The processing flow chart of the digital certificate revocation method provided by the embodiment of the present invention is as follows: figure 1 As shown, it is applied to the terminal entity of PKI technology, including:
[0046] Step S101: Obtain a digital certificate revocation instruction.
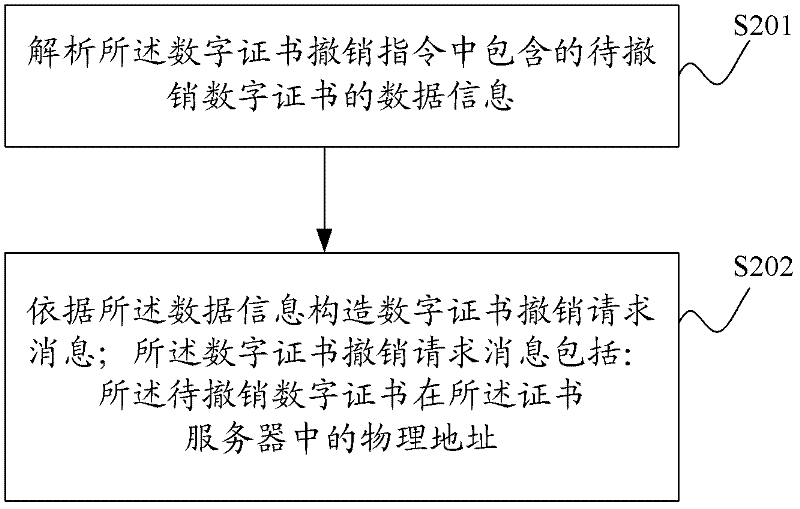
[0047] In this embodiment, the digital revocation instruction may be obtained when the user needs to revoke his digital certificate due to changes in user identity, user information, or user public key, user private key leakage, or user service suspension. A digital certificate revocation instruction sent by a user; it may also be a digital certificate revocation instruction automatically generated after a network device as an end entity detects an attack.
[0048] Step S102: Construct a digital certificate revocation request message according to the digital certificate revocation instruction.
[0049] When the terminal entity receives the digital certificate revocation inst...
Embodiment 2
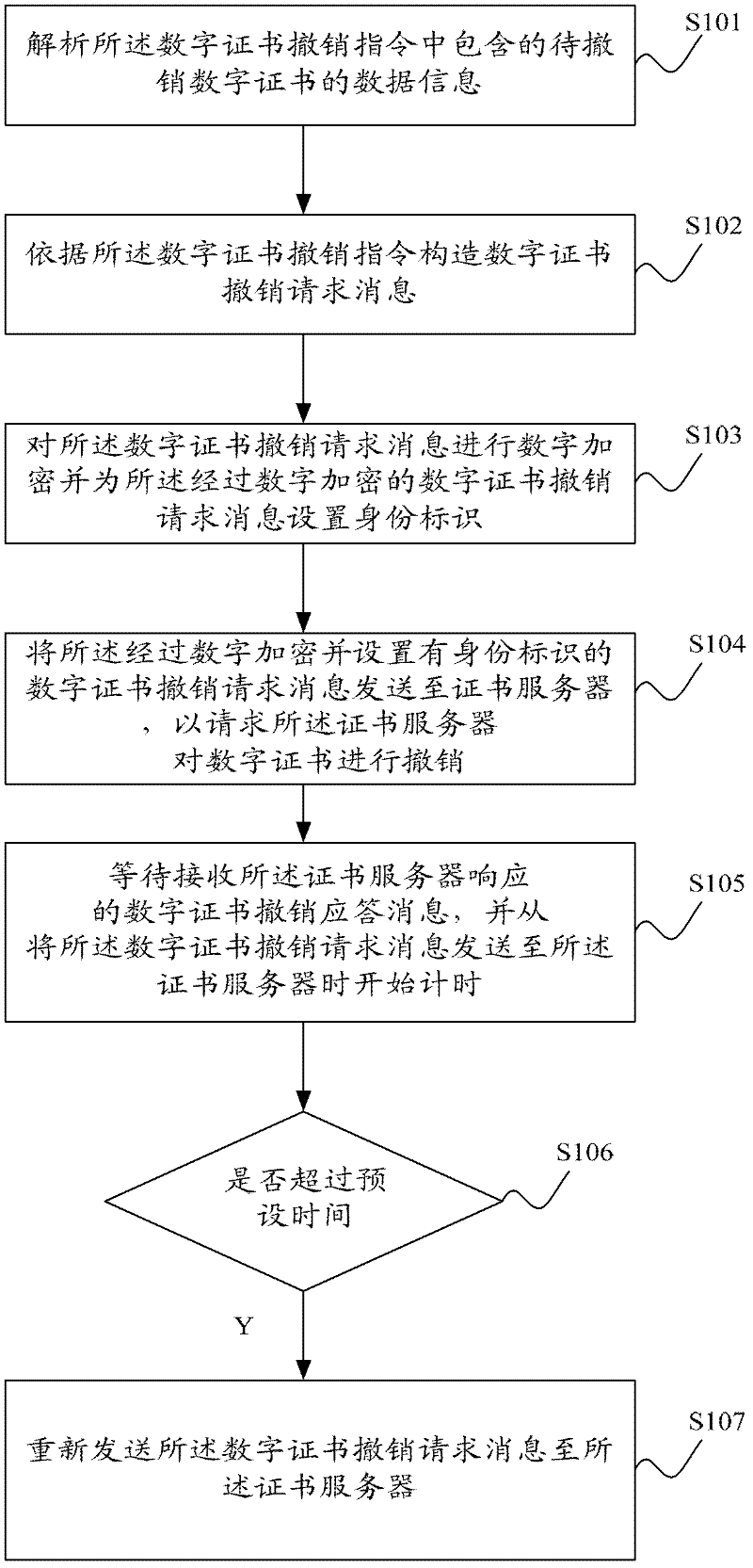
[0074] exist figure 1 On the basis of the method shown, when the digital certificate revocation request message is sent to the certificate server, optionally, it also includes waiting for the certificate server to respond to the digital certificate revocation request message, such as image 3 As shown, including steps S101-S107, wherein:
[0075] Step 101-step 104 are the same as those in Embodiment 1, and will not be repeated here.
[0076] Step S105: Waiting to receive the digital certificate revocation response message responded by the server in the certificate authority, and start timing from the time when the digital certificate revocation request message is sent to the certificate server;
[0077] After the digital certificate revocation request message is sent to the certificate server, start timing from the time point when the digital certificate revocation request message is sent out, and record the time from sending the digital certificate revocation request message...
Embodiment 3
[0087] The embodiment of the present invention provides a digital certificate revocation device corresponding to the digital certificate revocation request message shown in Embodiment 1, and its structural diagram is as follows Figure 5 shown, including:
[0088] An acquisition unit 301, a processor 302, an encoder 303 and a transmitter 304;
[0089] in:
[0090] The acquiring unit 301 is configured to acquire a digital certificate revocation instruction;
[0091] The processor 302 is configured to construct a digital certificate revocation request message according to the digital certificate revocation instruction;
[0092] The encoder 303 is configured to digitally encrypt the digital certificate revocation request message and set an identity for the digitally encrypted digital certificate revocation request message;
[0093] The transmitter 304 is configured to send the digitally encrypted certificate revocation request message set with the identity mark to the certific...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com