Method for structuring one-way Hash function based on random function
A random function and construction method technology, applied in the field of information security, can solve problems such as difficulty for cryptanalysts, difficulty in one-way, and complex algorithm design
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
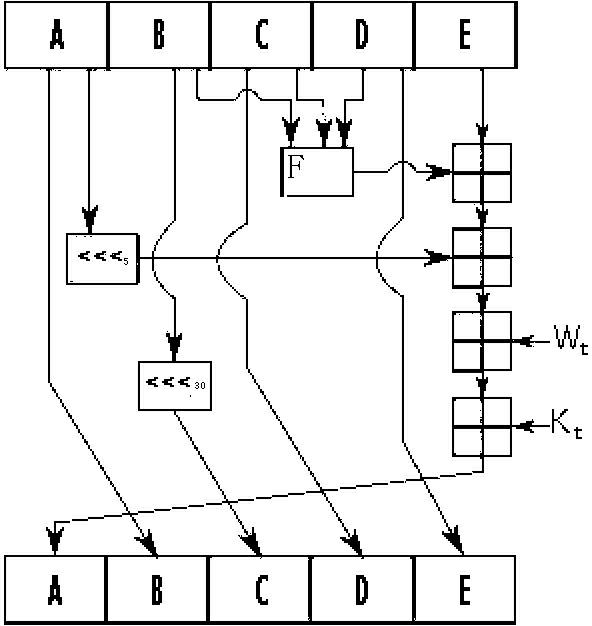
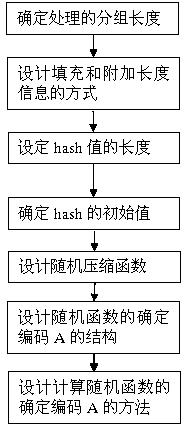
[0024] The following is an example of constructing a random hash function. For convenience and concise description, a relatively short algorithm is used and existing algorithms are used for reference.
[0025] Follow the steps to construct a random hash function:
[0026] The first step is to determine the processed packet length of 512bit.
[0027] The second step is to design the way of padding and additional length information, and pad the message. The first bit is filled with 1, and the subsequent bits are all 0. Fill it to 512n-64. If it happens to be in the form of 512n-64, fill it with 512bit , the first bit is also filled with 1, and the subsequent bits are all 0, n is the smallest integer that meets this condition, and 64 bits are reserved for additional message length, because in reality, the binary length of most messages is generally not Will exceed 64, that is, the length does not exceed 2 64 . When the binary value of the length of the message exceeds 64, that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com