Method and device for detecting malicious flash files
A file and malicious technology, applied in computer security devices, instruments, electronic digital data processing, etc., can solve the problems of low coverage, high maintenance costs, and the inability to detect malicious flash features in real time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
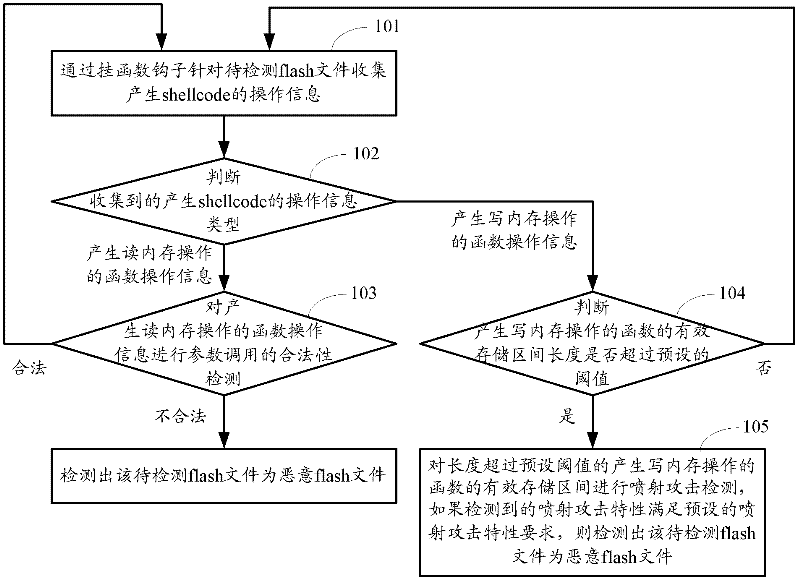
[0069] figure 1 The flow chart of the method for detecting malicious flash files using dynamic detection technology provided by Embodiment 1 of the present invention, such as figure 1 As shown, the method specifically includes the following steps:
[0070] Step 101: collect operation information for generating shellcode for the flash file to be detected through the function hook.
[0071] Before this step, there will be a preparation stage: create a new browser (IE) control process, and hang function hooks inside the flash analysis engine to take over the processing of some functions of the flash analysis engine. Shellcode is code or filling data that exploits a specific vulnerability. Generally, it is sent as data to the server to cause overflow. Here, some functions that may generate shellcode operations are hooked, including at least one of the following functions: Functions that generate memory read operations , such as date (Date) function and number (Number) function, ...
Embodiment 2
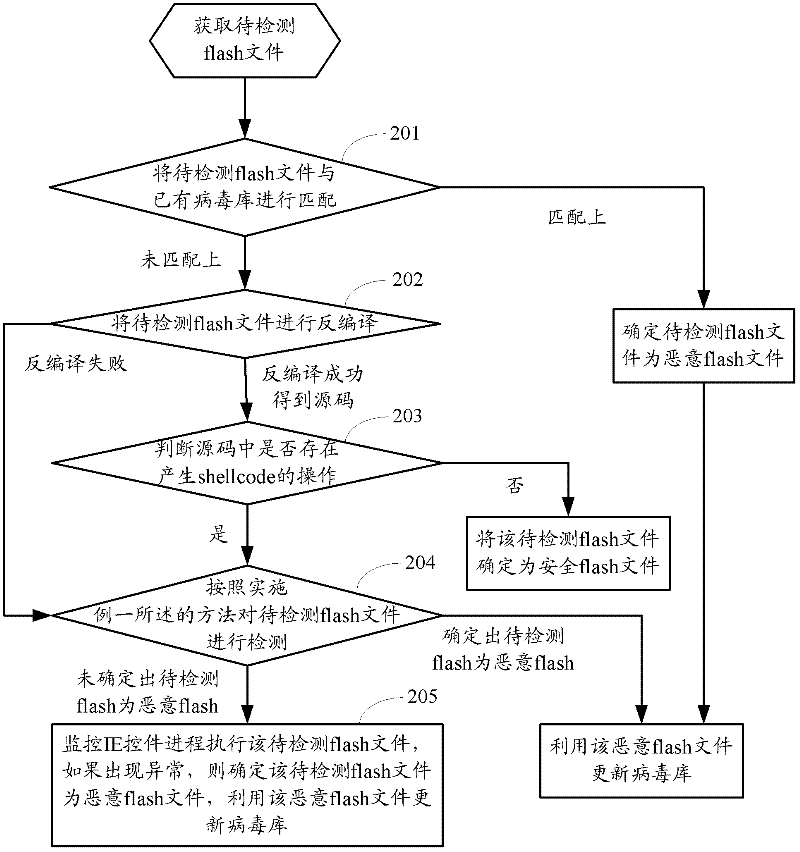
[0093] figure 2 The flow chart of the method for combining static detection technology and dynamic detection technology provided by Embodiment 2 of the present invention, as shown in figure 2 As shown, the method may include the following steps:
[0094] Step 201: Obtain the flash file to be detected, and match the flash file to be detected with the existing virus database. If they match, directly determine that the flash file to be detected is a malicious flash file, otherwise continue to step 202.
[0095] The existing virus database in the present invention may be a virus database established in an existing manner, or may be a virus database updated by using a malicious flash file detected in Embodiment 1 or Embodiment 2 of the present invention.
[0096] When matching the flash file to be detected with the existing virus database, hash calculation can be used, such as calculating the MD5HASH value of the flash file to be detected, and then using the calculated MD5HASH v...
Embodiment 3
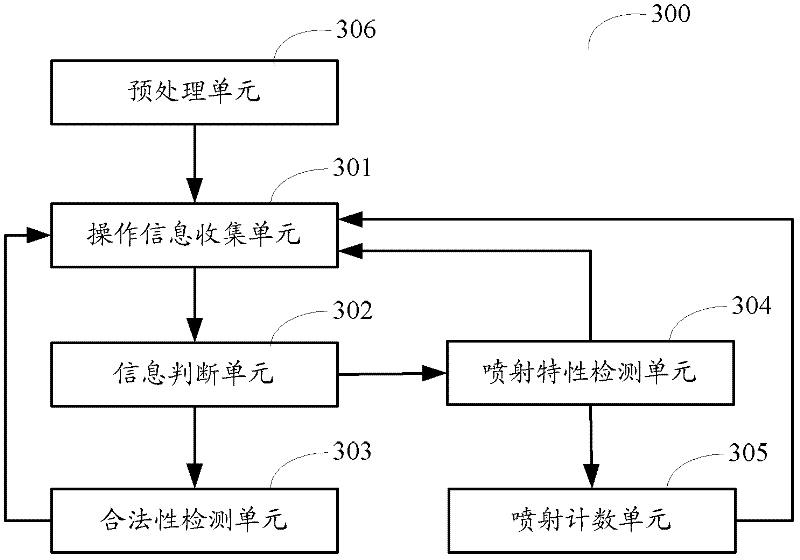
[0116] image 3 A schematic structural diagram of the dynamic detection module provided by Embodiment 3 of the present invention, such as image 3 As shown, the dynamic detection module 300 may include: an operation information collection unit 301 , an information judgment unit 302 , a legality detection unit 303 and an injection characteristic detection unit 304 .
[0117] The operation information collecting unit 301 collects the operation information of generating shellcode for the flash file to be detected through the function hook. The operation for generating the shellcode may include at least one of the following functions: functions for generating memory read operations, such as Date function and Number function, and functions for generating memory write operations, such as ByteArray function and string function.
[0118] The information judging unit 302 is used to judge the collected operation information that generates shellcode, if it is the function operation info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com