Special data filtering method for eliminating denial-of-service attacks to DNS (domain name system) service
A denial of service attack and DNS service technology, applied in the field of network security, can solve the problems of low precision, poor defense, high economic cost, etc., achieve low calculation and deployment costs, achieve congestion control, and high intelligence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The preferred embodiments of the present invention are given below in conjunction with the accompanying drawings to describe the technical solution of the present invention in detail.
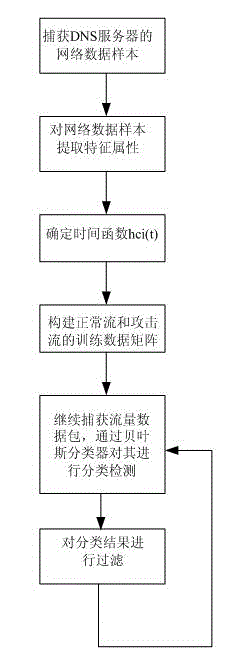
[0036] figure 1 The flow chart of the data filtering method for the denial of service attack of the DNS service proposed by the present invention is shown, and the specific implementation steps are:
[0037] Step 1, capturing network data samples of the DNS server.
[0038] Obtain the network data flow of the server from the mirror port of the switch on the DNS server side, and store it in the data file.
[0039] Step 2, extracting feature attributes from the captured network data samples.
[0040] (1) Extract feature attributes
[0041] The network data packet information captured in step 1 includes the quantity of various data packets, statistical information of source IP address and destination IP address, statistical information of data packet type (request or response), and the l...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com