Quantum security digital terminal applied to PSTN (Public Switched Telephone Network)
A quantum security and digital terminal technology, which is applied to key distribution, can solve problems such as short security periods, and achieve the effect of increasing speed and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
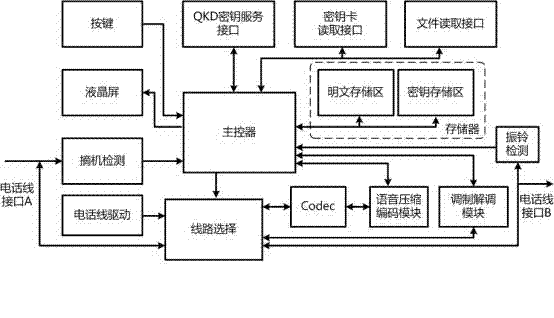
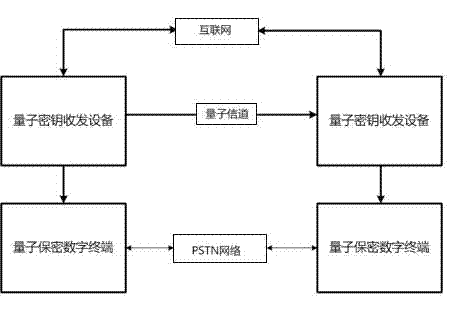
[0027] see figure 1 and figure 2 , the quantum security digital terminal applied to the PSTN network, including a main controller, a QKD key service interface, a voice compression coding module, a CODEC module, a modem module, a line selection module, a first telephone line interface and a second telephone line Interface; the main controller is connected to the quantum key server through the QKD key service interface; the main controller sends the user ID of the other party and the size of the required quantum key to the quantum key server through the QKD key service interface; the main controller The quantum key is also received through the QKD key service interface; the main controller is electrically connected to the modem module, the modem module is connected to the line selection module, and the line selection module is electrically connected to the main controller; the main controller is connected to the voice compression coding The modules are electrically connected, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com