Transition consistency verification method of computer network defending strategy
A computer network and verification method technology, applied in the field of computer network security, can solve problems such as inability to locate, inaccurate judgment of consistency, logical errors, etc., to achieve the effect of accurate analysis and positioning, and improve the efficiency of verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
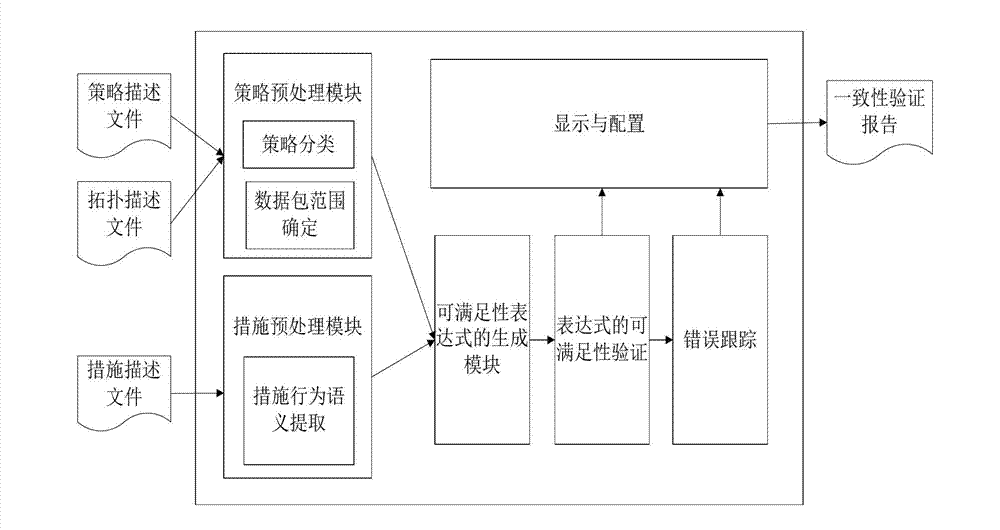
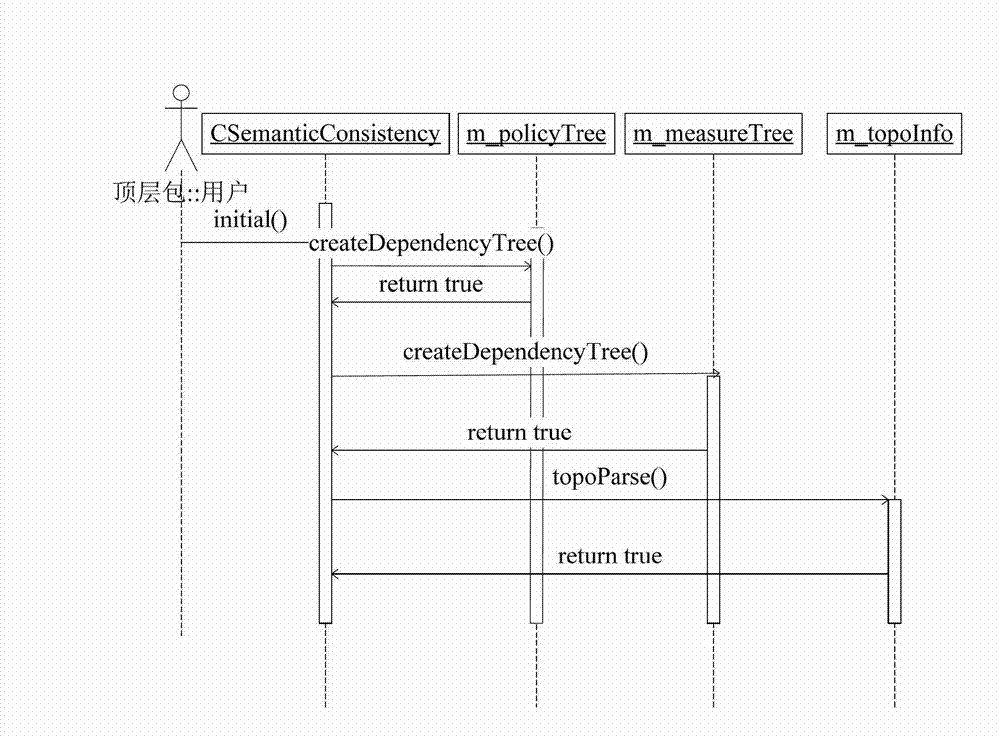
[0028] The invention adopts the SMT-based satisfiability solution theory to model the strategies and measures in the computer network defense, and then performs consistency verification on the two. If the structure is satisfiable, it indicates that there is an inconsistency between the strategy and the measure. The counterexample can be obtained by using the derivation rules, and the position, type and reason of the inconsistency can be obtained through further analysis.
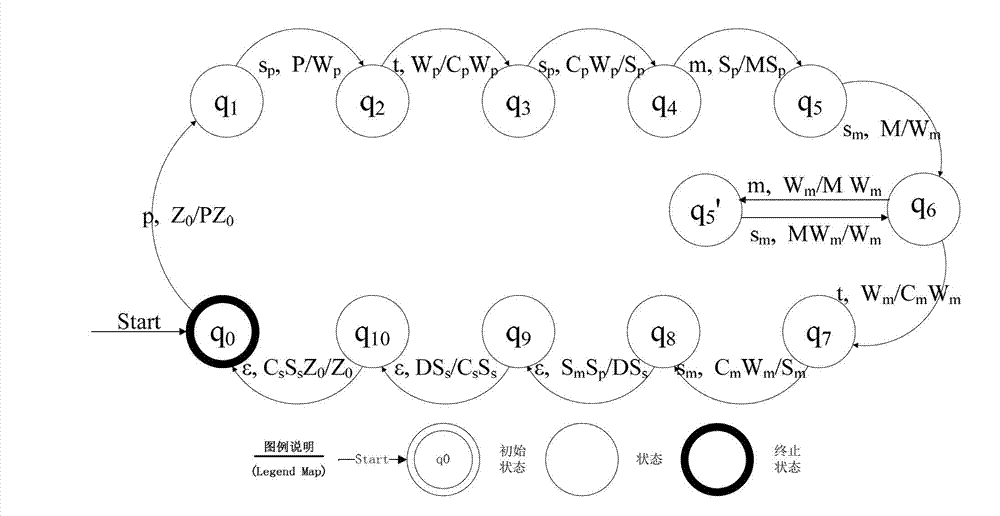
[0029] 1. Automaton description
[0030] According to the conceptual model of the consistency analysis of computer network defense strategy transformation given before, the automaton model of the consistency analysis of computer network defense strategy transformation is constructed, in which the state transition function of the automaton model is derived from the activities in the conceptual model Each state is composed of all the values of the entity concept at a certain moment. The model is represented...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com