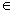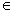Internet protocol security (IPSEC) tunnel data transmission method and device thereof
A data transmission method and IP data packet technology, applied in the field of data transmission, IPSEC tunnel data transmission method and device, can solve the problems of high overhead of bus resources and central processing unit, low processing efficiency of IPSEC small data volume IP message, etc. Achieve the effect of improving splitting efficiency, good promotion value, and improving processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] Embodiment one: a kind of IPSEC tunnel data transmission method comprises the following steps:
[0055] Step 1: The receiving end of the network card receives the IP message sent by the intranet, and outputs the data after packaging, encrypting, and encapsulating through the network data sending device;
[0056] Step 2: The network data receiving device performs data decryption, decapsulation, and unpacking, and then outputs the data through the output port of the network card.
Embodiment 2
[0057] Embodiment two: on the basis of embodiment one, as image 3 As shown, the specific process that the network data sending device carries out data packaging, encryption, and encapsulation in the step 1 is:
[0058] Step 11: The receiving end of the network card receives the IP message sent by the intranet, the first data receiving module classifies and stores the IP message according to the security policy table, and at the same time, the accumulator or timer in the timer and accumulator module monitors the data length of the IP message , the first data receiving module establishes corresponding buffers for different security policies;
[0059] Step 12: When one of the accumulators overflows or the timer is cleared, the first data receiving module outputs all IP packets in the corresponding buffer to the data reassembly module and clears the corresponding buffer; otherwise, the first data receiving module continues to receive IP packets;
[0060] Step 13: When the data ...
Embodiment 3
[0061] Embodiment three: on the basis of embodiment one or two, the specific process of the first data receiving module in the step 11 according to the classification and storage of IP packets in the security policy is:
[0062] Step 111: the first data receiving module matches the security policy in the security policy table according to the source IP address, destination IP address, source port address, destination port range, and quintuple information of the transport layer protocol of the received IP message;
[0063] Step 112: If the five-tuple information of the IP message matches the same security policy in the security policy table, it is the same type of IP message, otherwise it is a different type of IP message, and then the same type of IP message is temporarily received in order Stored in the corresponding same buffer; at the same time, calculate the data length through the accumulator, compare the result of the accumulator with the threshold set by the data receivi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com